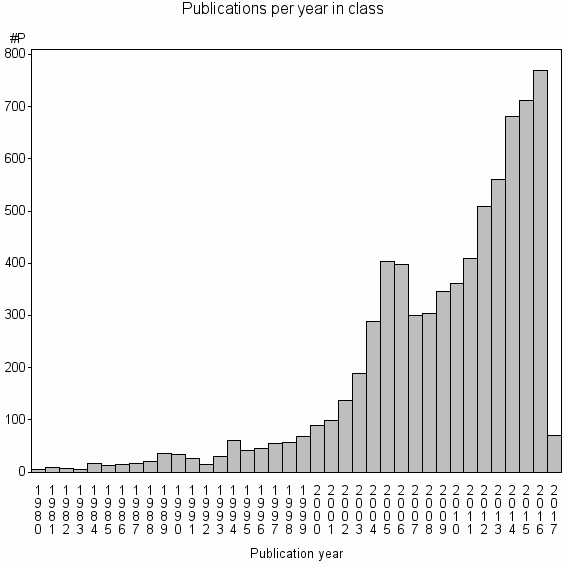
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 1591 | 7195 | 29.9 | 27% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | COMPUTERS & SECURITY | journal | 990704 | 7% | 44% | 528 |
| 2 | DIGITAL INVESTIGATION | journal | 974768 | 4% | 73% | 314 |
| 3 | INTRUSION DETECTION | authKW | 973638 | 6% | 56% | 408 |
| 4 | NETWORK SECURITY | authKW | 418775 | 4% | 34% | 291 |
| 5 | DIGITAL FORENSICS | authKW | 407342 | 2% | 59% | 164 |
| 6 | MALWARE | authKW | 337684 | 2% | 69% | 116 |
| 7 | INTRUSION DETECTION SYSTEM | authKW | 330792 | 2% | 60% | 131 |
| 8 | INFORMATION SECURITY | authKW | 314419 | 3% | 32% | 234 |
| 9 | COMPUTER SECURITY | authKW | 292284 | 2% | 45% | 154 |
| 10 | IEEE SECURITY & PRIVACY | journal | 231949 | 3% | 29% | 186 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Information Systems | 220068 | 45% | 2% | 3258 |
| 2 | Computer Science, Software Engineering | 58874 | 21% | 1% | 1521 |
| 3 | Computer Science, Hardware & Architecture | 54302 | 16% | 1% | 1124 |
| 4 | Computer Science, Theory & Methods | 44645 | 22% | 1% | 1584 |
| 5 | Telecommunications | 42468 | 21% | 1% | 1488 |
| 6 | Computer Science, Artificial Intelligence | 10771 | 11% | 0% | 762 |
| 7 | Computer Science, Interdisciplinary Applications | 6698 | 9% | 0% | 631 |
| 8 | Engineering, Electrical & Electronic | 6372 | 19% | 0% | 1394 |
| 9 | Information Science & Library Science | 3458 | 4% | 0% | 265 |
| 10 | Computer Science, Cybernetics | 1590 | 1% | 0% | 106 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | INFORMAT ASSURANCE GRP | 58446 | 0% | 66% | 21 |
| 2 | SECUR COMMUN NETWORK | 40719 | 0% | 80% | 12 |
| 3 | COMP SCI | 38440 | 17% | 1% | 1192 |
| 4 | IS SECUR | 27146 | 0% | 80% | 8 |
| 5 | RELIABLE SOFTWARE GRP | 22619 | 0% | 67% | 8 |
| 6 | COMP SECUR | 22017 | 0% | 20% | 26 |
| 7 | COMP SCI ENGN | 21555 | 6% | 1% | 430 |
| 8 | INFORMAT SECUR | 21535 | 1% | 6% | 80 |
| 9 | ADV CYBER FORENS | 21210 | 0% | 100% | 5 |
| 10 | SECURE INFORMAT SYST | 20918 | 0% | 25% | 20 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | COMPUTERS & SECURITY | 990704 | 7% | 44% | 528 |
| 2 | DIGITAL INVESTIGATION | 974768 | 4% | 73% | 314 |
| 3 | IEEE SECURITY & PRIVACY | 231949 | 3% | 29% | 186 |
| 4 | SECURITY AND COMMUNICATION NETWORKS | 108007 | 3% | 14% | 188 |
| 5 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 77775 | 1% | 20% | 94 |
| 6 | COMPUTER NETWORKS | 30723 | 2% | 4% | 165 |
| 7 | IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY | 26389 | 1% | 7% | 94 |
| 8 | ACM TRANSACTIONS ON INFORMATION AND SYSTEM SECURITY | 22930 | 0% | 17% | 32 |
| 9 | INTERNATIONAL JOURNAL OF INFORMATION SECURITY | 21277 | 1% | 13% | 38 |
| 10 | JOURNAL OF NETWORK AND COMPUTER APPLICATIONS | 19067 | 1% | 5% | 88 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | INTRUSION DETECTION | 973638 | 6% | 56% | 408 | Search INTRUSION+DETECTION | Search INTRUSION+DETECTION |
| 2 | NETWORK SECURITY | 418775 | 4% | 34% | 291 | Search NETWORK+SECURITY | Search NETWORK+SECURITY |
| 3 | DIGITAL FORENSICS | 407342 | 2% | 59% | 164 | Search DIGITAL+FORENSICS | Search DIGITAL+FORENSICS |
| 4 | MALWARE | 337684 | 2% | 69% | 116 | Search MALWARE | Search MALWARE |
| 5 | INTRUSION DETECTION SYSTEM | 330792 | 2% | 60% | 131 | Search INTRUSION+DETECTION+SYSTEM | Search INTRUSION+DETECTION+SYSTEM |
| 6 | INFORMATION SECURITY | 314419 | 3% | 32% | 234 | Search INFORMATION+SECURITY | Search INFORMATION+SECURITY |
| 7 | COMPUTER SECURITY | 292284 | 2% | 45% | 154 | Search COMPUTER+SECURITY | Search COMPUTER+SECURITY |
| 8 | ANOMALY DETECTION | 229687 | 3% | 23% | 231 | Search ANOMALY+DETECTION | Search ANOMALY+DETECTION |
| 9 | MALWARE DETECTION | 210439 | 1% | 81% | 61 | Search MALWARE+DETECTION | Search MALWARE+DETECTION |
| 10 | TRAFFIC CLASSIFICATION | 209313 | 1% | 77% | 64 | Search TRAFFIC+CLASSIFICATION | Search TRAFFIC+CLASSIFICATION |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | BHUYAN, MH , BHATTACHARYYA, DK , KALITA, JK , (2014) NETWORK ANOMALY DETECTION: METHODS, SYSTEMS AND TOOLS.IEEE COMMUNICATIONS SURVEYS AND TUTORIALS. VOL. 16. ISSUE 1. P. 303 -336 | 51 | 65% | 47 |
| 2 | QUICK, D , CHOO, KKR , (2014) IMPACTS OF INCREASING VOLUME OF DIGITAL FORENSIC DATA: A SURVEY AND FUTURE RESEARCH CHALLENGES.DIGITAL INVESTIGATION. VOL. 11. ISSUE 4. P. 273 -294 | 42 | 82% | 11 |
| 3 | TEH, PS , TEOH, ABJ , YUE, SG , (2013) A SURVEY OF KEYSTROKE DYNAMICS BIOMETRICS.SCIENTIFIC WORLD JOURNAL. VOL. . ISSUE . P. - | 37 | 93% | 17 |
| 4 | HOQUE, N , BHATTACHARYYA, DK , KALITA, JK , (2015) BOTNET IN DDOS ATTACKS: TRENDS AND CHALLENGES.IEEE COMMUNICATIONS SURVEYS AND TUTORIALS. VOL. 17. ISSUE 4. P. 2242 -2270 | 42 | 82% | 1 |
| 5 | LIN, WC , KE, SW , TSAI, CF , (2015) CANN: AN INTRUSION DETECTION SYSTEM BASED ON COMBINING CLUSTER CENTERS AND NEAREST NEIGHBORS.KNOWLEDGE-BASED SYSTEMS. VOL. 78. ISSUE . P. 13 -21 | 29 | 88% | 18 |
| 6 | GAN, CQ , YANG, XF , ZHU, QY , (2014) PROPAGATION OF COMPUTER VIRUS UNDER THE INFLUENCES OF INFECTED EXTERNAL COMPUTERS AND REMOVABLE STORAGE MEDIA.NONLINEAR DYNAMICS. VOL. 78. ISSUE 2. P. 1349 -1356 | 33 | 97% | 4 |
| 7 | AB RAHMAN, NH , CHOO, KKR , (2015) A SURVEY OF INFORMATION SECURITY INCIDENT HANDLING IN THE CLOUD.COMPUTERS & SECURITY. VOL. 49. ISSUE . P. 45 -69 | 41 | 72% | 5 |
| 8 | LOUKAS, G , OKE, G , (2010) PROTECTION AGAINST DENIAL OF SERVICE ATTACKS: A SURVEY.COMPUTER JOURNAL. VOL. 53. ISSUE 7. P. 1020 -1037 | 43 | 78% | 22 |
| 9 | CARDENAS-SOLANO, LJ , MARTINEZ-ARDILA, H , BECERRA-ARDILA, LE , (2016) INFORMATION SECURITY MANAGEMENT: A BIBLIOGRAPHIC REVIEW.PROFESIONAL DE LA INFORMACION. VOL. 25. ISSUE 6. P. 931 -948 | 44 | 71% | 0 |
| 10 | ZHANG, CM , HUANG, HT , (2016) OPTIMAL CONTROL STRATEGY FOR A NOVEL COMPUTER VIRUS PROPAGATION MODEL ON SCALE-FREE NETWORKS.PHYSICA A-STATISTICAL MECHANICS AND ITS APPLICATIONS. VOL. 451. ISSUE . P. 251 -265 | 36 | 77% | 1 |
Classes with closest relation at Level 2 |