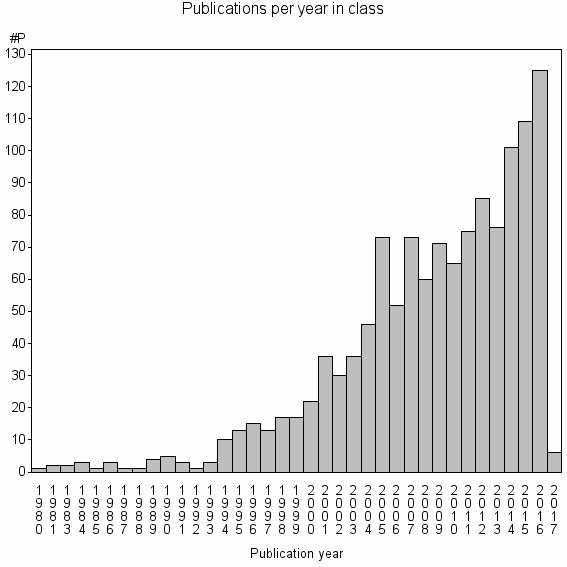
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 8401 | 1256 | 38.7 | 31% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | COMPUTERS & SECURITY | journal | 1263011 | 20% | 21% | 249 |
| 2 | INFORMATION SECURITY | authKW | 1239456 | 15% | 26% | 194 |
| 3 | INFORMATION SECURITY MANAGEMENT | authKW | 770307 | 3% | 81% | 39 |
| 4 | INFORMATION SYSTEMS SECURITY | authKW | 521223 | 2% | 79% | 27 |
| 5 | GRAPHICAL PASSWORD | authKW | 405714 | 2% | 76% | 22 |
| 6 | INFORMATION SECURITY AWARENESS | authKW | 366078 | 1% | 94% | 16 |
| 7 | INFORMATION SECURITY POLICY | authKW | 311161 | 1% | 80% | 16 |
| 8 | INFORMATION SECURITY CULTURE | authKW | 243100 | 1% | 100% | 10 |
| 9 | IS SECURITY | authKW | 241664 | 1% | 76% | 13 |
| 10 | INFORMATION SECURITY GOVERNANCE | authKW | 186995 | 1% | 77% | 10 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Information Systems | 50362 | 52% | 0% | 650 |
| 2 | Information Science & Library Science | 16385 | 18% | 0% | 228 |
| 3 | Computer Science, Software Engineering | 7998 | 19% | 0% | 235 |
| 4 | Management | 4813 | 14% | 0% | 173 |
| 5 | Computer Science, Hardware & Architecture | 4011 | 10% | 0% | 129 |
| 6 | Computer Science, Theory & Methods | 3929 | 16% | 0% | 199 |
| 7 | Computer Science, Cybernetics | 2101 | 4% | 0% | 49 |
| 8 | Ergonomics | 1599 | 3% | 0% | 43 |
| 9 | Operations Research & Management Science | 753 | 6% | 0% | 75 |
| 10 | Computer Science, Artificial Intelligence | 675 | 7% | 0% | 83 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | IS SECUR | 155581 | 1% | 80% | 8 |
| 2 | STAND BANK INFORMAT TECHNOL | 97240 | 0% | 100% | 4 |
| 3 | TUCKS GLASSMEYER MCNAMEE DIGITAL STRATEGIES | 72930 | 0% | 100% | 3 |
| 4 | INFORMAT PROC SCI | 55864 | 2% | 12% | 19 |
| 5 | INFORMAT SECUR NETWORK GRP | 54696 | 0% | 75% | 3 |
| 6 | COMMAND CONTROL INFORMAT WARFARE | 48620 | 0% | 100% | 2 |
| 7 | MANAGEMENT TECHNOL SECUR | 48620 | 0% | 100% | 2 |
| 8 | SYST COMP TECHNOL | 48620 | 0% | 100% | 2 |
| 9 | INFORMAT CYBER SECUR | 43756 | 0% | 60% | 3 |
| 10 | SECUR CONVERGENCE | 36462 | 0% | 50% | 3 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | COMPUTERS & SECURITY | 1263011 | 20% | 21% | 249 |
| 2 | IEEE SECURITY & PRIVACY | 92264 | 4% | 8% | 49 |
| 3 | JOURNAL OF MANAGEMENT INFORMATION SYSTEMS | 22562 | 2% | 4% | 25 |
| 4 | COMMUNICATIONS OF THE ACM | 20075 | 5% | 1% | 59 |
| 5 | MIS QUARTERLY | 17131 | 2% | 3% | 28 |
| 6 | JOURNAL OF ORGANIZATIONAL AND END USER COMPUTING | 12140 | 1% | 6% | 8 |
| 7 | EUROPEAN JOURNAL OF INFORMATION SYSTEMS | 11435 | 2% | 2% | 19 |
| 8 | INFORMATION SYSTEMS RESEARCH | 11058 | 2% | 2% | 19 |
| 9 | DECISION SUPPORT SYSTEMS | 10708 | 3% | 1% | 34 |
| 10 | INFORMATION & MANAGEMENT | 10469 | 2% | 2% | 28 |
Author Key Words |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | CARDENAS-SOLANO, LJ , MARTINEZ-ARDILA, H , BECERRA-ARDILA, LE , (2016) INFORMATION SECURITY MANAGEMENT: A BIBLIOGRAPHIC REVIEW.PROFESIONAL DE LA INFORMACION. VOL. 25. ISSUE 6. P. 931 -948 | 42 | 68% | 0 |
| 2 | BARTON, KA , TEJAY, G , LANE, M , TERRELL, S , (2016) INFORMATION SYSTEM SECURITY COMMITMENT: A STUDY OF EXTERNAL INFLUENCES ON SENIOR MANAGEMENT.COMPUTERS & SECURITY. VOL. 59. ISSUE . P. 9 -25 | 44 | 56% | 1 |
| 3 | IFINEDO, P , (2016) CRITICAL TIMES FOR ORGANIZATIONS: WHAT SHOULD BE DONE TO CURB WORKERS' NONCOMPLIANCE WITH IS SECURITY POLICY GUIDELINES?.INFORMATION SYSTEMS MANAGEMENT. VOL. 33. ISSUE 1. P. 30 -41 | 35 | 74% | 0 |
| 4 | SAFA, NS , VON SOLMS, R , FURNELL, S , (2016) INFORMATION SECURITY POLICY COMPLIANCE MODEL IN ORGANIZATIONS.COMPUTERS & SECURITY. VOL. 56. ISSUE . P. 70 -82 | 35 | 67% | 1 |
| 5 | DA VEIGA, A , MARTINS, N , (2015) IMPROVING THE INFORMATION SECURITY CULTURE THROUGH MONITORING AND IMPLEMENTATION ACTIONS ILLUSTRATED THROUGH A CASE STUDY.COMPUTERS & SECURITY. VOL. 49. ISSUE . P. 162 -176 | 24 | 100% | 3 |
| 6 | GAO, X , ZHONG, WJ , MEI, SE , (2015) SECURITY INVESTMENT AND INFORMATION SHARING UNDER AN ALTERNATIVE SECURITY BREACH PROBABILITY FUNCTION.INFORMATION SYSTEMS FRONTIERS. VOL. 17. ISSUE 2. P. 423 -438 | 31 | 69% | 3 |
| 7 | GAO, X , ZHONG, WJ , (2016) A DIFFERENTIAL GAME APPROACH TO SECURITY INVESTMENT AND INFORMATION SHARING IN A COMPETITIVE ENVIRONMENT.IIE TRANSACTIONS. VOL. 48. ISSUE 6. P. 511 -526 | 35 | 59% | 0 |
| 8 | REECE, RP , STAHL, BC , (2015) THE PROFESSIONALISATION OF INFORMATION SECURITY: PERSPECTIVES OF UK PRACTITIONERS.COMPUTERS & SECURITY. VOL. 48. ISSUE . P. 182 -195 | 26 | 76% | 2 |
| 9 | CROSSLER, RE , JOHNSTON, AC , LOWRY, PB , HU, Q , WARKENTIN, M , BASKERVILLE, R , (2013) FUTURE DIRECTIONS FOR BEHAVIORAL INFORMATION SECURITY RESEARCH.COMPUTERS & SECURITY. VOL. 32. ISSUE . P. 90 -101 | 31 | 55% | 44 |
| 10 | POSEY, C , ROBERTS, TL , LOWRY, PB , HIGHTOWER, RT , (2014) BRIDGING THE DIVIDE: A QUALITATIVE COMPARISON OF INFORMATION SECURITY THOUGHT PATTERNS BETWEEN INFORMATION SECURITY PROFESSIONALS AND ORDINARY ORGANIZATIONAL INSIDERS.INFORMATION & MANAGEMENT. VOL. 51. ISSUE 5. P. 551 -567 | 32 | 62% | 7 |
Classes with closest relation at Level 1 |