Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
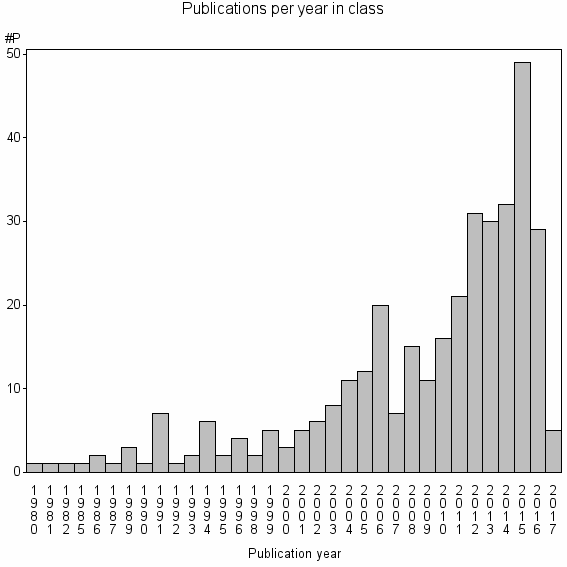
| 23300 | 351 | 27.4 | 21% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | RETURN ORIENTED PROGRAMMING | authKW | 473634 | 2% | 78% | 7 |
| 2 | DEVICE DRIVERS | authKW | 391467 | 3% | 50% | 9 |
| 3 | HYPERVISORS | authKW | 231983 | 1% | 67% | 4 |
| 4 | SR IOV | authKW | 217482 | 1% | 50% | 5 |
| 5 | VIRTUALIZATION | authKW | 216397 | 11% | 6% | 40 |
| 6 | HYPERVISOR | authKW | 201317 | 3% | 26% | 9 |
| 7 | CROSS VM COMMUNICATIONS | authKW | 173989 | 1% | 100% | 2 |
| 8 | DMA ATTACKS | authKW | 173989 | 1% | 100% | 2 |
| 9 | DRIVER ISOLATION | authKW | 173989 | 1% | 100% | 2 |
| 10 | HARDWARE ASSISTED PAGING | authKW | 173989 | 1% | 100% | 2 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Software Engineering | 12864 | 44% | 0% | 155 |
| 2 | Computer Science, Hardware & Architecture | 5857 | 23% | 0% | 81 |
| 3 | Computer Science, Information Systems | 5266 | 32% | 0% | 112 |
| 4 | Computer Science, Theory & Methods | 3936 | 29% | 0% | 103 |
| 5 | Telecommunications | 800 | 13% | 0% | 46 |
| 6 | Engineering, Electrical & Electronic | 391 | 21% | 0% | 75 |
| 7 | Architecture | 99 | 1% | 0% | 3 |
| 8 | COMPUTER APPLICATIONS & CYBERNETICS | 31 | 0% | 0% | 1 |
| 9 | Computer Science, Artificial Intelligence | 19 | 3% | 0% | 9 |
| 10 | Computer Science, Interdisciplinary Applications | 8 | 2% | 0% | 7 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | ADV ARCHITECTURE TECHNOL | 86995 | 0% | 100% | 1 |
| 2 | CHEM ELECT ENGN SYST PHYS | 86995 | 0% | 100% | 1 |
| 3 | COMP ENGN DEI | 86995 | 0% | 100% | 1 |
| 4 | COMP SOLUT GRP | 86995 | 0% | 100% | 1 |
| 5 | HIGH FREQUENCY TECHNOL RADIO SYST | 86995 | 0% | 100% | 1 |
| 6 | INTEGRATED IL ENGN CIFE | 86995 | 0% | 100% | 1 |
| 7 | INTERUNIV CONSORTIUM INFORMAT CINI | 86995 | 0% | 100% | 1 |
| 8 | IPADS | 86995 | 0% | 100% | 1 |
| 9 | JRC USMILE | 86995 | 0% | 100% | 1 |
| 10 | KERNEL GRP | 86995 | 0% | 100% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | IEEE SECURITY & PRIVACY | 66580 | 6% | 3% | 22 |
| 2 | ACM SIGPLAN NOTICES | 36429 | 13% | 1% | 45 |
| 3 | ACM TRANSACTIONS ON COMPUTER SYSTEMS | 20165 | 3% | 2% | 10 |
| 4 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 8848 | 2% | 1% | 7 |
| 5 | ACM TRANSACTIONS ON INFORMATION AND SYSTEM SECURITY | 7357 | 1% | 2% | 4 |
| 6 | IBM SYSTEMS JOURNAL | 7001 | 3% | 1% | 9 |
| 7 | ACM TRANSACTIONS ON ARCHITECTURE AND CODE OPTIMIZATION | 5013 | 1% | 1% | 5 |
| 8 | ACM COMPUTING SURVEYS | 3973 | 2% | 1% | 6 |
| 9 | IBM JOURNAL OF RESEARCH AND DEVELOPMENT | 3577 | 3% | 0% | 9 |
| 10 | COMPUTER | 3409 | 3% | 0% | 11 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | RETURN ORIENTED PROGRAMMING | 473634 | 2% | 78% | 7 | Search RETURN+ORIENTED+PROGRAMMING | Search RETURN+ORIENTED+PROGRAMMING |
| 2 | DEVICE DRIVERS | 391467 | 3% | 50% | 9 | Search DEVICE+DRIVERS | Search DEVICE+DRIVERS |
| 3 | HYPERVISORS | 231983 | 1% | 67% | 4 | Search HYPERVISORS | Search HYPERVISORS |
| 4 | SR IOV | 217482 | 1% | 50% | 5 | Search SR+IOV | Search SR+IOV |
| 5 | VIRTUALIZATION | 216397 | 11% | 6% | 40 | Search VIRTUALIZATION | Search VIRTUALIZATION |
| 6 | HYPERVISOR | 201317 | 3% | 26% | 9 | Search HYPERVISOR | Search HYPERVISOR |
| 7 | CROSS VM COMMUNICATIONS | 173989 | 1% | 100% | 2 | Search CROSS+VM+COMMUNICATIONS | Search CROSS+VM+COMMUNICATIONS |
| 8 | DMA ATTACKS | 173989 | 1% | 100% | 2 | Search DMA+ATTACKS | Search DMA+ATTACKS |
| 9 | DRIVER ISOLATION | 173989 | 1% | 100% | 2 | Search DRIVER+ISOLATION | Search DRIVER+ISOLATION |
| 10 | HARDWARE ASSISTED PAGING | 173989 | 1% | 100% | 2 | Search HARDWARE+ASSISTED+PAGING | Search HARDWARE+ASSISTED+PAGING |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | SGANDURRA, D , LUPU, E , (2015) EVOLUTION OF ATTACKS, THREAT MODELS, AND SOLUTIONS FOR VIRTUALIZED SYSTEMS.ACM COMPUTING SURVEYS. VOL. 48. ISSUE 3. P. - | 12 | 67% | 0 |
| 2 | ASOKAN, N , EKBERG, JE , KOSTIAINEN, K , RAJAN, A , ROZAS, C , SADEGHI, AR , SCHULZ, S , WACHSMANN, C , (2014) MOBILE TRUSTED COMPUTING.PROCEEDINGS OF THE IEEE. VOL. 102. ISSUE 8. P. 1189 -1206 | 7 | 78% | 4 |
| 3 | REN, JB , QI, Y , DAI, YH , WANG, XG , SHI, Y , (2015) APPSEC: A SAFE EXECUTION ENVIRONMENT FOR SECURITY SENSITIVE APPLICATIONST.ACM SIGPLAN NOTICES. VOL. 50. ISSUE 7. P. 187 -199 | 5 | 100% | 0 |
| 4 | MA, C , YAN, D , WANG, YP , HU, SM , (2013) ADVANCED GRAPH MODEL FOR TAINTED VARIABLE TRACKING.SCIENCE CHINA-INFORMATION SCIENCES. VOL. 56. ISSUE 11. P. - | 5 | 100% | 0 |
| 5 | PEARCE, M , ZEADALLY, S , HUNT, R , (2013) VIRTUALIZATION: ISSUES, SECURITY THREATS, AND SOLUTIONS.ACM COMPUTING SURVEYS. VOL. 45. ISSUE 2. P. - | 9 | 50% | 14 |
| 6 | MA, C , ZHAO, P , HU, SM , (2012) SERIALDRIVER: IMPROVING THE RELIABILITY OF DEVICE DRIVERS THROUGH SERIALIZATION.IEEE TRANSACTIONS ON CONSUMER ELECTRONICS. VOL. 58. ISSUE 3. P. 1070 -1076 | 6 | 75% | 2 |
| 7 | CHEN, WZ , XU, L , LI, GX , XIANG, Y , (2015) A LIGHTWEIGHT VIRTUALIZATION SOLUTION FOR ANDROID DEVICES.IEEE TRANSACTIONS ON COMPUTERS. VOL. 64. ISSUE 10. P. 2741 -2751 | 4 | 100% | 3 |
| 8 | WANG, XL , LUO, TW , HU, JY , WANG, ZL , LUO, YW , (2017) EVALUATING THE IMPACTS OF HUGEPAGE ON VIRTUAL MACHINES.SCIENCE CHINA-INFORMATION SCIENCES. VOL. 60. ISSUE 1. P. - | 4 | 100% | 0 |
| 9 | WANG, Z , LI, JJ , WU, CG , YANG, DY , WANG, ZJ , HSU, WC , LI, B , GUAN, Y , (2015) HSPT: PRACTICAL IMPLEMENTATION AND EFFICIENT MANAGEMENT OF EMBEDDED SHADOW PAGE TABLES FOR CROSS-ISA SYSTEM VIRTUAL MACHINES.ACM SIGPLAN NOTICES. VOL. 50. ISSUE 7. P. 53 -64 | 4 | 100% | 0 |
| 10 | CRISWELL, J , DAUTENHAHN, N , ADVE, V , (2014) VIRTUAL GHOST: PROTECTING APPLICATIONS FROM HOSTILE OPERATING SYSTEMS.ACM SIGPLAN NOTICES. VOL. 49. ISSUE 4. P. 81 -96 | 4 | 100% | 1 |
Classes with closest relation at Level 1 |