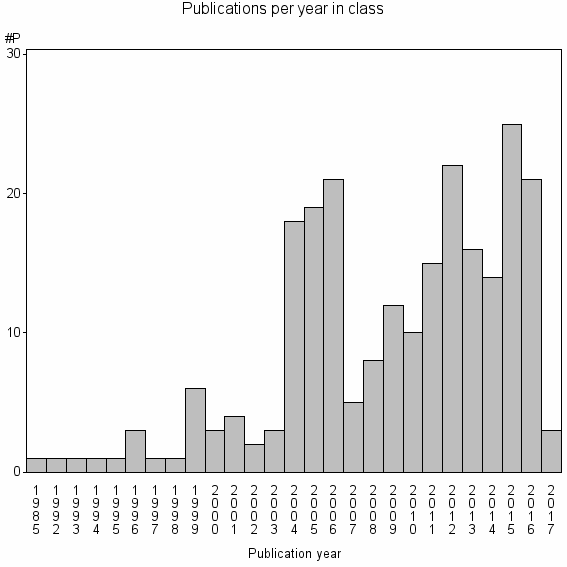
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 27112 | 237 | 29.0 | 26% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
| Cluster id | Level | Cluster label | #P |
|---|---|---|---|
| 9 | 4 | COMPUTER SCIENCE, THEORY & METHODS//COMPUTER SCIENCE, ARTIFICIAL INTELLIGENCE//COMPUTER SCIENCE, INFORMATION SYSTEMS | 1247339 |
| 20 | 3 | COMPUTER SCIENCE, INFORMATION SYSTEMS//COMPUTER SCIENCE, THEORY & METHODS//COMPUTER SCIENCE, SOFTWARE ENGINEERING | 118625 |
| 1591 | 2 | COMPUTERS & SECURITY//DIGITAL INVESTIGATION//INTRUSION DETECTION | 7195 |
| 27112 | 1 | ATTACK GRAPH//SECURITY METRICS//MTTSF | 237 |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | ATTACK GRAPH | authKW | 979852 | 7% | 45% | 17 |
| 2 | SECURITY METRICS | authKW | 488224 | 5% | 32% | 12 |
| 3 | MTTSF | authKW | 386523 | 1% | 100% | 3 |
| 4 | NETWORK HARDENING | authKW | 386523 | 1% | 100% | 3 |
| 5 | EMC APPROACH | authKW | 257682 | 1% | 100% | 2 |
| 6 | INFORMATION SECURITY EVALUATION | authKW | 257682 | 1% | 100% | 2 |
| 7 | SPACE BORNE COMPUTING | authKW | 257682 | 1% | 100% | 2 |
| 8 | INTRUSION TOLERANCE | authKW | 176868 | 4% | 15% | 9 |
| 9 | NETWORK RISK | authKW | 171787 | 1% | 67% | 2 |
| 10 | ACCIDENTAL FAULT | authKW | 128841 | 0% | 100% | 1 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Information Systems | 6669 | 43% | 0% | 103 |
| 2 | Computer Science, Software Engineering | 5167 | 34% | 0% | 81 |
| 3 | Computer Science, Hardware & Architecture | 3854 | 23% | 0% | 54 |
| 4 | Computer Science, Theory & Methods | 3631 | 34% | 0% | 81 |
| 5 | Telecommunications | 736 | 15% | 0% | 36 |
| 6 | Computer Science, Artificial Intelligence | 173 | 8% | 0% | 18 |
| 7 | Engineering, Electrical & Electronic | 133 | 16% | 0% | 38 |
| 8 | Computer Science, Interdisciplinary Applications | 78 | 5% | 0% | 13 |
| 9 | Robotics | 16 | 1% | 0% | 2 |
| 10 | Engineering, General | 16 | 3% | 0% | 6 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | ADV CONTROL SIMULAT | 128841 | 0% | 100% | 1 |
| 2 | AREA CYBERSECUR DISTRIBUTED SYST | 128841 | 0% | 100% | 1 |
| 3 | AUTHENTICAT SERV | 128841 | 0% | 100% | 1 |
| 4 | CIVIL MANAGEMENT ENGN | 128841 | 0% | 100% | 1 |
| 5 | DEV DEPENDABLE COMP TECHNOL | 128841 | 0% | 100% | 1 |
| 6 | DPTO ENG COMP SIST DIGITAIS | 128841 | 0% | 100% | 1 |
| 7 | GT ARC | 128841 | 0% | 100% | 1 |
| 8 | INESCC SYST COMP ENGN COIMBRA PORTUGAL | 128841 | 0% | 100% | 1 |
| 9 | KETI | 128841 | 0% | 100% | 1 |
| 10 | PROJECT SYST | 128841 | 0% | 100% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 68541 | 7% | 3% | 16 |
| 2 | IEEE SECURITY & PRIVACY | 20367 | 4% | 2% | 10 |
| 3 | COMPUTERS & SECURITY | 8730 | 4% | 1% | 9 |
| 4 | JOURNAL OF NETWORK AND SYSTEMS MANAGEMENT | 7434 | 2% | 1% | 4 |
| 5 | INTERNATIONAL JOURNAL OF CRITICAL INFRASTRUCTURE PROTECTION | 3704 | 1% | 1% | 2 |
| 6 | IET INFORMATION SECURITY | 3595 | 1% | 1% | 3 |
| 7 | LECTURE NOTES IN COMPUTER SCIENCE | 2532 | 18% | 0% | 42 |
| 8 | JOURNAL OF NETWORK AND COMPUTER APPLICATIONS | 1876 | 2% | 0% | 5 |
| 9 | INTERNATIONAL JOURNAL OF INFORMATION SECURITY | 1792 | 1% | 1% | 2 |
| 10 | JOURNAL OF SUPERCOMPUTING | 1508 | 2% | 0% | 5 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | ATTACK GRAPH | 979852 | 7% | 45% | 17 | Search ATTACK+GRAPH | Search ATTACK+GRAPH |
| 2 | SECURITY METRICS | 488224 | 5% | 32% | 12 | Search SECURITY+METRICS | Search SECURITY+METRICS |
| 3 | MTTSF | 386523 | 1% | 100% | 3 | Search MTTSF | Search MTTSF |
| 4 | NETWORK HARDENING | 386523 | 1% | 100% | 3 | Search NETWORK+HARDENING | Search NETWORK+HARDENING |
| 5 | EMC APPROACH | 257682 | 1% | 100% | 2 | Search EMC+APPROACH | Search EMC+APPROACH |
| 6 | INFORMATION SECURITY EVALUATION | 257682 | 1% | 100% | 2 | Search INFORMATION+SECURITY+EVALUATION | Search INFORMATION+SECURITY+EVALUATION |
| 7 | SPACE BORNE COMPUTING | 257682 | 1% | 100% | 2 | Search SPACE+BORNE+COMPUTING | Search SPACE+BORNE+COMPUTING |
| 8 | INTRUSION TOLERANCE | 176868 | 4% | 15% | 9 | Search INTRUSION+TOLERANCE | Search INTRUSION+TOLERANCE |
| 9 | NETWORK RISK | 171787 | 1% | 67% | 2 | Search NETWORK+RISK | Search NETWORK+RISK |
| 10 | ACCIDENTAL FAULT | 128841 | 0% | 100% | 1 | Search ACCIDENTAL+FAULT | Search ACCIDENTAL+FAULT |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | DOHI, T , UEMURA, T , (2012) AN ADAPTIVE MODE CONTROL ALGORITHM OF A SCALABLE INTRUSION TOLERANT ARCHITECTURE.JOURNAL OF COMPUTER AND SYSTEM SCIENCES. VOL. 78. ISSUE 6. P. 1751 -1774 | 8 | 89% | 3 |
| 2 | HARATY, RA , ZBIB, M , MASUD, M , (2016) DATA DAMAGE ASSESSMENT AND RECOVERY ALGORITHM FROM MALICIOUS ATTACKS IN HEALTHCARE DATA SHARING SYSTEMS.PEER-TO-PEER NETWORKING AND APPLICATIONS. VOL. 9. ISSUE 5. P. 812 -823 | 5 | 100% | 0 |
| 3 | BOPCHE, GS , MEHTRE, BM , (2017) GRAPH SIMILARITY METRICS FOR ASSESSING TEMPORAL CHANGES IN ATTACK SURFACE OF DYNAMIC NETWORKS.COMPUTERS & SECURITY. VOL. 64. ISSUE . P. 16 -43 | 9 | 50% | 0 |
| 4 | WANG, LY , JAJODIA, S , SINGHAL, A , CHENG, PS , NOEL, S , (2014) K-ZERO DAY SAFETY: A NETWORK SECURITY METRIC FOR MEASURING THE RISK OF UNKNOWN VULNERABILITIES.IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING. VOL. 11. ISSUE 1. P. 30-44 | 6 | 67% | 16 |
| 5 | BARIK, MS , SENGUPTA, A , MAZUMDAR, C , (2016) ATTACK GRAPH GENERATION AND ANALYSIS TECHNIQUES.DEFENCE SCIENCE JOURNAL. VOL. 66. ISSUE 6. P. 559 -567 | 5 | 83% | 0 |
| 6 | UEMURA, T , DOHI, T , KAIO, N , (2010) AVAILABILITY ANALYSIS OF AN INTRUSION TOLERANT DISTRIBUTED SERVER SYSTEM WITH PREVENTIVE MAINTENANCE.IEEE TRANSACTIONS ON RELIABILITY. VOL. 59. ISSUE 1. P. 18 -29 | 6 | 75% | 3 |
| 7 | UEMURA, T , DOHI, T , KAIO, N , (2010) DEPENDABILITY ANALYSIS OF A SCALABLE INTRUSION TOLERANT ARCHITECTURE WITH TWO DETECTION MODES.JOURNAL OF INTERNET TECHNOLOGY. VOL. 11. ISSUE 2. P. 289 -298 | 6 | 75% | 1 |
| 8 | ALMOHRI, HMJ , WATSON, LT , YAO, DF , OU, XM , (2016) SECURITY OPTIMIZATION OF DYNAMIC NETWORKS WITH PROBABILISTIC GRAPH MODELING AND LINEAR PROGRAMMING.IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING. VOL. 13. ISSUE 4. P. 474 -487 | 5 | 71% | 0 |
| 9 | WINDELBERG, M , (2016) OBJECTIVES FOR MANAGING CYBER SUPPLY CHAIN RISK.INTERNATIONAL JOURNAL OF CRITICAL INFRASTRUCTURE PROTECTION. VOL. 12. ISSUE . P. 4 -11 | 4 | 80% | 1 |
| 10 | HOLM, H , SHAHZAD, K , BUSCHLE, M , EKSTEDT, M , (2015) (PCYSEMOL)-CY-2: PREDICTIVE, PROBABILISTIC CYBER SECURITY MODELING LANGUAGE.IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING. VOL. 12. ISSUE 6. P. 626 -639 | 6 | 55% | 1 |
Classes with closest relation at Level 1 |