Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
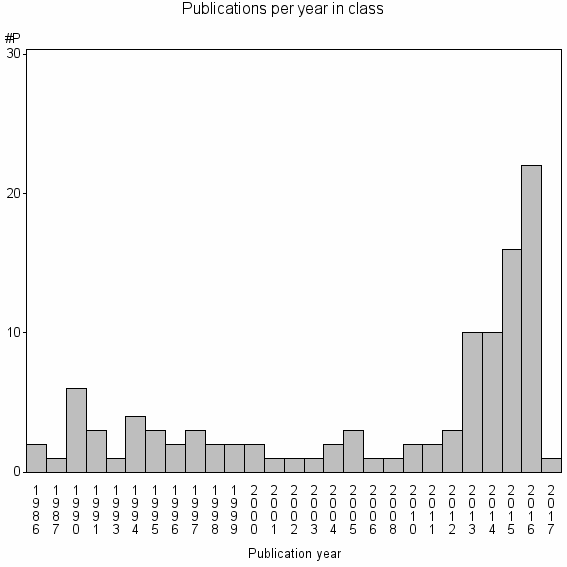
| 34697 | 107 | 27.8 | 23% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | SOCIAL NETWORK SECURITY | authKW | 856139 | 3% | 100% | 3 |
| 2 | INTERACTION ORIENTED | authKW | 570759 | 2% | 100% | 2 |
| 3 | SOCIAL BOT | authKW | 570759 | 2% | 100% | 2 |
| 4 | SPAMMER | authKW | 380505 | 2% | 67% | 2 |
| 5 | ANOMALOUS ACCOUNT DETECTION | authKW | 285380 | 1% | 100% | 1 |
| 6 | AUTOMATED SOCIAL ENGINEERING | authKW | 285380 | 1% | 100% | 1 |
| 7 | BLOG BOT | authKW | 285380 | 1% | 100% | 1 |
| 8 | BOTS DETECTION | authKW | 285380 | 1% | 100% | 1 |
| 9 | CAPEK | authKW | 285380 | 1% | 100% | 1 |
| 10 | CHIP GENERATOR | authKW | 285380 | 1% | 100% | 1 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Information Systems | 2568 | 40% | 0% | 43 |
| 2 | Computer Science, Software Engineering | 1559 | 28% | 0% | 30 |
| 3 | Computer Science, Hardware & Architecture | 1048 | 18% | 0% | 19 |
| 4 | Computer Science, Theory & Methods | 523 | 20% | 0% | 21 |
| 5 | Computer Science, Cybernetics | 259 | 5% | 0% | 5 |
| 6 | Computer Science, Artificial Intelligence | 251 | 13% | 0% | 14 |
| 7 | Telecommunications | 243 | 13% | 0% | 14 |
| 8 | Engineering, Electrical & Electronic | 98 | 20% | 0% | 21 |
| 9 | Ergonomics | 39 | 2% | 0% | 2 |
| 10 | Ethics | 30 | 2% | 0% | 2 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | CIFRE PROGRAM | 285380 | 1% | 100% | 1 |
| 2 | LSUB | 285380 | 1% | 100% | 1 |
| 3 | OPERATING SYST CHAIR | 285380 | 1% | 100% | 1 |
| 4 | SECURE COMMUN COMP SYST | 285380 | 1% | 100% | 1 |
| 5 | SNT CRITIX | 285380 | 1% | 100% | 1 |
| 6 | CHIP GENERATOR GRP | 142689 | 1% | 50% | 1 |
| 7 | WIRELESS SYST RD | 142689 | 1% | 50% | 1 |
| 8 | SENAC | 95125 | 1% | 33% | 1 |
| 9 | SYSNET | 95125 | 1% | 33% | 1 |
| 10 | COMMUN MEDIA FILM | 71343 | 1% | 25% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | COMPUTERS & SECURITY | 8600 | 6% | 1% | 6 |
| 2 | IEEE INTELLIGENT SYSTEMS | 6460 | 4% | 1% | 4 |
| 3 | ACM TRANSACTIONS ON THE WEB | 5973 | 2% | 1% | 2 |
| 4 | COMPUTING & CONTROL ENGINEERING JOURNAL | 4353 | 2% | 1% | 2 |
| 5 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 2369 | 2% | 0% | 2 |
| 6 | HUMAN STUDIES | 1852 | 2% | 0% | 2 |
| 7 | SECURITY AND COMMUNICATION NETWORKS | 1850 | 3% | 0% | 3 |
| 8 | SPACE AND CULTURE | 1351 | 1% | 0% | 1 |
| 9 | ACM TRANSACTIONS ON KNOWLEDGE DISCOVERY FROM DATA | 1284 | 1% | 0% | 1 |
| 10 | COMPUTER NETWORKS | 1219 | 4% | 0% | 4 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | SOCIAL NETWORK SECURITY | 856139 | 3% | 100% | 3 | Search SOCIAL+NETWORK+SECURITY | Search SOCIAL+NETWORK+SECURITY |
| 2 | INTERACTION ORIENTED | 570759 | 2% | 100% | 2 | Search INTERACTION+ORIENTED | Search INTERACTION+ORIENTED |
| 3 | SOCIAL BOT | 570759 | 2% | 100% | 2 | Search SOCIAL+BOT | Search SOCIAL+BOT |
| 4 | SPAMMER | 380505 | 2% | 67% | 2 | Search SPAMMER | Search SPAMMER |
| 5 | ANOMALOUS ACCOUNT DETECTION | 285380 | 1% | 100% | 1 | Search ANOMALOUS+ACCOUNT+DETECTION | Search ANOMALOUS+ACCOUNT+DETECTION |
| 6 | AUTOMATED SOCIAL ENGINEERING | 285380 | 1% | 100% | 1 | Search AUTOMATED+SOCIAL+ENGINEERING | Search AUTOMATED+SOCIAL+ENGINEERING |
| 7 | BLOG BOT | 285380 | 1% | 100% | 1 | Search BLOG+BOT | Search BLOG+BOT |
| 8 | BOTS DETECTION | 285380 | 1% | 100% | 1 | Search BOTS+DETECTION | Search BOTS+DETECTION |
| 9 | CAPEK | 285380 | 1% | 100% | 1 | Search CAPEK | Search CAPEK |
| 10 | CHIP GENERATOR | 285380 | 1% | 100% | 1 | Search CHIP+GENERATOR | Search CHIP+GENERATOR |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | SHEN, H , MA, FL , ZHANG, XC , ZONG, LL , LIU, XY , LIANG, WX , (2017) DISCOVERING SOCIAL SPAMMERS FROM MULTIPLE VIEWS0.NEUROCOMPUTING. VOL. 225. ISSUE . P. 49 -57 | 7 | 78% | 0 |
| 2 | CRESCI, S , DI PIETRO, R , PETROCCHI, M , SPOGNARDI, A , TESCONI, M , (2015) FAME FOR SALE: EFFICIENT DETECTION OF FAKE TWITTER FOLLOWERS.DECISION SUPPORT SYSTEMS. VOL. 80. ISSUE . P. 56 -71 | 7 | 58% | 3 |
| 3 | CRESCI, S , DI PIETRO, R , PETROCCHI, M , SPOGNARDI, A , TESCONI, M , (2016) DNA-INSPIRED ONLINE BEHAVIORAL MODELING AND ITS APPLICATION TO SPAMBOT DETECTION.IEEE INTELLIGENT SYSTEMS. VOL. 31. ISSUE 5. P. 58 -64 | 5 | 71% | 0 |
| 4 | HE, YK , ZHANG, GY , WU, J , LI, Q , (2016) UNDERSTANDING A PROSPECTIVE APPROACH TO DESIGNING MALICIOUS SOCIAL BOTS.SECURITY AND COMMUNICATION NETWORKS. VOL. 9. ISSUE 13. P. 2157 -2172 | 7 | 50% | 0 |
| 5 | YANG, W , DONG, GZ , WANG, W , HU, YX , SHEN, GW , YU, M , (2015) A NOVEL APPROACH FOR BOTS DETECTION IN SINA MICROBLOG.JOURNAL OF COMPUTATIONAL AND THEORETICAL NANOSCIENCE. VOL. 12. ISSUE 7. P. 1420 -1425 | 3 | 100% | 0 |
| 6 | BISSETT, A , (2000) SOME HUMAN DIMENSIONS OF COMPUTER VIRUS CREATION AND INFECTION.INTERNATIONAL JOURNAL OF HUMAN-COMPUTER STUDIES. VOL. 52. ISSUE 5. P. 899-913 | 6 | 67% | 9 |
| 7 | PIOTROWSKI, JA , (2000) BUILDING A MODEL OF A USEFUL TURING MACHINE.COMPUTERS & MATHEMATICS WITH APPLICATIONS. VOL. 39. ISSUE 1-2. P. 127 -143 | 4 | 100% | 0 |
| 8 | JI, YD , HE, YK , JIANG, XY , CAO, J , LI, Q , (2016) COMBATING THE EVASION MECHANISMS OF SOCIAL BOTS.COMPUTERS & SECURITY. VOL. 58. ISSUE . P. 230 -249 | 6 | 43% | 0 |
| 9 | THIMBLEBY, H , ANDERSON, S , CAIRNS, P , (1998) A FRAMEWORK FOR MODELLING TROJANS AND COMPUTER VIRUS INFECTION.COMPUTER JOURNAL. VOL. 41. ISSUE 7. P. 444-458 | 7 | 54% | 26 |
| 10 | SHUANG, K , SU, S , (2014) PAIDD: A HYBRID P2P-BASED ARCHITECTURE FOR IMPROVING DATA DISTRIBUTION IN SOCIAL NETWORKS.SCIENCE CHINA-INFORMATION SCIENCES. VOL. 57. ISSUE 4. P. - | 3 | 75% | 1 |
Classes with closest relation at Level 1 |