Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
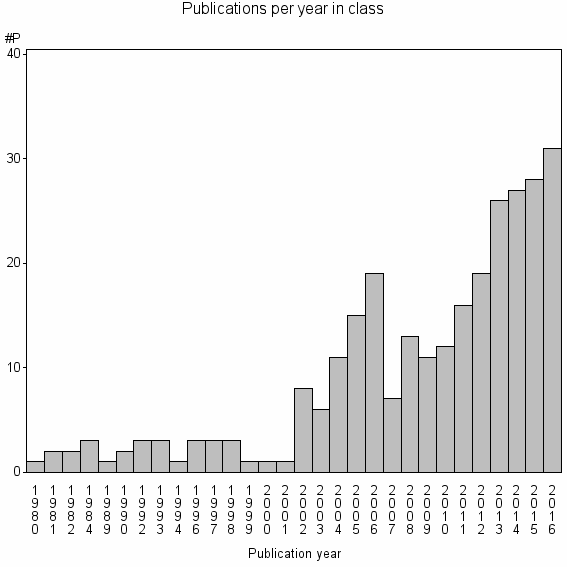
| 25529 | 279 | 30.8 | 22% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | SQL INJECTION ATTACK | authKW | 456021 | 2% | 83% | 5 |
| 2 | SQL INJECTION | authKW | 437778 | 2% | 67% | 6 |
| 3 | SOFTWARE FAULT ISOLATION | authKW | 350224 | 1% | 80% | 4 |
| 4 | MEMORY SAFETY | authKW | 335169 | 3% | 44% | 7 |
| 5 | FINITE HOMOGENEOUS MARKOV CHAIN | authKW | 328336 | 1% | 100% | 3 |
| 6 | PROBABILISTIC MEMORY SAFETY | authKW | 328336 | 1% | 100% | 3 |
| 7 | WEB APPLICATION SECURITY | authKW | 304011 | 2% | 56% | 5 |
| 8 | BUFFER OVERFLOWS | authKW | 250157 | 1% | 57% | 4 |
| 9 | APPLICATION LOGIC VULNERABILITY | authKW | 218891 | 1% | 100% | 2 |
| 10 | AUTOMATIC POOL ALLOCATION | authKW | 218891 | 1% | 100% | 2 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Software Engineering | 16690 | 56% | 0% | 157 |
| 2 | Computer Science, Hardware & Architecture | 4895 | 24% | 0% | 66 |
| 3 | Computer Science, Information Systems | 3111 | 28% | 0% | 77 |
| 4 | Computer Science, Theory & Methods | 2008 | 24% | 0% | 66 |
| 5 | Engineering, Electrical & Electronic | 205 | 18% | 0% | 50 |
| 6 | Telecommunications | 137 | 6% | 0% | 18 |
| 7 | Computer Science, Artificial Intelligence | 80 | 5% | 0% | 14 |
| 8 | Computer Science, Interdisciplinary Applications | 74 | 5% | 0% | 14 |
| 9 | Medical Informatics | 6 | 1% | 0% | 2 |
| 10 | Statistics & Probability | 4 | 1% | 0% | 4 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | BIT BLAZE GRP | 109445 | 0% | 100% | 1 |
| 2 | CIENCIA COMP DCC | 109445 | 0% | 100% | 1 |
| 3 | DISRINET GRP | 109445 | 0% | 100% | 1 |
| 4 | EDUC INFORMAT ASSURANCE SECUR CERIAS | 109445 | 0% | 100% | 1 |
| 5 | ENGD SYST ENGN | 109445 | 0% | 100% | 1 |
| 6 | FRAUD MANAGEMENT | 109445 | 0% | 100% | 1 |
| 7 | IBM AFRICA | 109445 | 0% | 100% | 1 |
| 8 | JACQUARD GRP | 109445 | 0% | 100% | 1 |
| 9 | NETWORK SECUR INFORMAT | 109445 | 0% | 100% | 1 |
| 10 | NETWORK SYST SECUR GRP | 109445 | 0% | 100% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | ACM SIGPLAN NOTICES | 29332 | 13% | 1% | 36 |
| 2 | IEEE SECURITY & PRIVACY | 17298 | 4% | 2% | 10 |
| 3 | SOFTWARE-PRACTICE & EXPERIENCE | 15009 | 6% | 1% | 18 |
| 4 | COMPUTERS & SECURITY | 13187 | 4% | 1% | 12 |
| 5 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 8179 | 2% | 1% | 6 |
| 6 | ACM TRANSACTIONS ON EMBEDDED COMPUTING SYSTEMS | 2526 | 1% | 1% | 4 |
| 7 | ACM TRANSACTIONS ON INTERNET TECHNOLOGY | 2442 | 1% | 1% | 2 |
| 8 | ACM TRANSACTIONS ON INFORMATION AND SYSTEM SECURITY | 2312 | 1% | 1% | 2 |
| 9 | ACM TRANSACTIONS ON DESIGN AUTOMATION OF ELECTRONIC SYSTEMS | 2311 | 1% | 1% | 4 |
| 10 | ACM TRANSACTIONS ON PROGRAMMING LANGUAGES AND SYSTEMS | 1875 | 1% | 0% | 4 |
Author Key Words |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | DEEPA, G , THILAGAM, PS , (2016) SECURING WEB APPLICATIONS FROM INJECTION AND LOGIC VULNERABILITIES: APPROACHES AND CHALLENGES.INFORMATION AND SOFTWARE TECHNOLOGY. VOL. 74. ISSUE . P. 160 -180 | 11 | 58% | 0 |
| 2 | PALSETIA, N , DEEPA, G , KHAN, FA , THILAGAM, PS , PAIS, AR , (2016) SECURING NATIVE XML DATABASE-DRIVEN WEB APPLICATIONS FROM XQUERY INJECTION VULNERABILITIES.JOURNAL OF SYSTEMS AND SOFTWARE. VOL. 122. ISSUE . P. 93 -109 | 9 | 69% | 0 |
| 3 | SAINI, A , GAUR, MS , LAXMI, V , CONTI, M , (2016) COLLUDING BROWSER EXTENSION ATTACK ON USER PRIVACY AND ITS IMPLICATION FOR WEB BROWSERS.COMPUTERS & SECURITY. VOL. 63. ISSUE . P. 14 -28 | 6 | 100% | 0 |
| 4 | NAGARAKATTE, S , MARTIN, MMK , ZDANCEWIC, S , (2013) HARDWARE-ENFORCED COMPREHENSIVE MEMORY SAFETY.IEEE MICRO. VOL. 33. ISSUE 3. P. 38 -47 | 6 | 100% | 3 |
| 5 | SHAR, LK , TAN, HBK , (2013) DEFEATING SQL INJECTION.COMPUTER. VOL. 46. ISSUE 3. P. 69-77 | 5 | 100% | 10 |
| 6 | KAYAALP, M , OZSOY, M , ABU GHAZALEH, N , PONOMAREV, D , (2014) EFFICIENTLY SECURING SYSTEMS FROM CODE REUSE ATTACKS.IEEE TRANSACTIONS ON COMPUTERS. VOL. 63. ISSUE 5. P. 1144 -1156 | 5 | 100% | 1 |
| 7 | BARUA, RK , SIMPSON, MS , (2013) MEMSAFE: ENSURING THE SPATIAL AND TEMPORAL MEMORY SAFETY OF C?AT RUNTIME.SOFTWARE-PRACTICE & EXPERIENCE. VOL. 43. ISSUE 1. P. 93 -128 | 8 | 44% | 10 |
| 8 | LI, XW , XUE, Y , (2014) A SURVEY ON SERVER-SIDE APPROACHES TO SECURING WEB APPLICATIONS.ACM COMPUTING SURVEYS. VOL. 46. ISSUE 4. P. - | 5 | 71% | 3 |
| 9 | DELOZIER, C , EISENBERG, R , NAGARAKATTE, S , OSERA, PM , MARTIN, MMK , ZDANCEWIC, S , (2013) IRONCLAD C PLUS PLUS A LIBRARY-AUGMENTED TYPE-SAFE SUBSET OF C PLUS.ACM SIGPLAN NOTICES. VOL. 48. ISSUE 10. P. 287-304 | 5 | 71% | 0 |
| 10 | AGAPIE, A , ANDREICA, A , CHIRA, C , GIUCLEA, M , (2014) PREDICTABILITY IN CELLULAR AUTOMATA.PLOS ONE. VOL. 9. ISSUE 10. P. - | 4 | 80% | 0 |
Classes with closest relation at Level 1 |