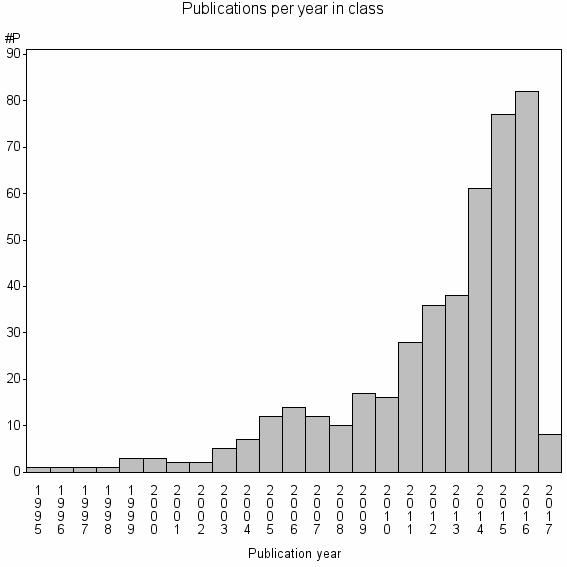
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 21011 | 437 | 32.0 | 25% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
| Cluster id | Level | Cluster label | #P |
|---|---|---|---|
| 9 | 4 | COMPUTER SCIENCE, THEORY & METHODS//COMPUTER SCIENCE, ARTIFICIAL INTELLIGENCE//COMPUTER SCIENCE, INFORMATION SYSTEMS | 1247339 |
| 20 | 3 | COMPUTER SCIENCE, INFORMATION SYSTEMS//COMPUTER SCIENCE, THEORY & METHODS//COMPUTER SCIENCE, SOFTWARE ENGINEERING | 118625 |
| 1591 | 2 | COMPUTERS & SECURITY//DIGITAL INVESTIGATION//INTRUSION DETECTION | 7195 |
| 21011 | 1 | MALWARE DETECTION//MALWARE//ANDROID SECURITY | 437 |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | MALWARE DETECTION | authKW | 2146496 | 11% | 64% | 48 |
| 2 | MALWARE | authKW | 1117913 | 12% | 31% | 52 |
| 3 | ANDROID SECURITY | authKW | 924800 | 3% | 88% | 15 |
| 4 | MALWARE ANALYSIS | authKW | 655058 | 3% | 63% | 15 |
| 5 | ANDROID MALWARE | authKW | 537488 | 2% | 77% | 10 |
| 6 | SMARTPHONE SECURITY | authKW | 529563 | 3% | 63% | 12 |
| 7 | ANDROID | authKW | 494415 | 11% | 15% | 46 |
| 8 | MALWARE CLASSIFICATION | authKW | 489118 | 2% | 100% | 7 |
| 9 | MOBILE MALWARE | authKW | 465820 | 2% | 67% | 10 |
| 10 | DYNAMIC MALWARE ANALYSIS | authKW | 279496 | 1% | 100% | 4 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Information Systems | 18452 | 53% | 0% | 232 |
| 2 | Computer Science, Software Engineering | 7185 | 30% | 0% | 130 |
| 3 | Telecommunications | 3724 | 25% | 0% | 108 |
| 4 | Computer Science, Hardware & Architecture | 3573 | 16% | 0% | 71 |
| 5 | Computer Science, Theory & Methods | 3185 | 24% | 0% | 104 |
| 6 | Computer Science, Artificial Intelligence | 505 | 9% | 0% | 41 |
| 7 | Engineering, Electrical & Electronic | 380 | 19% | 0% | 84 |
| 8 | Computer Science, Interdisciplinary Applications | 203 | 6% | 0% | 28 |
| 9 | Engineering, General | 30 | 3% | 0% | 11 |
| 10 | Operations Research & Management Science | 15 | 2% | 0% | 8 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | DEUT TELECOM S | 139748 | 0% | 100% | 2 |
| 2 | ENTERPRISE RISK SERV | 139748 | 0% | 100% | 2 |
| 3 | COMP SECUR COSEC | 78605 | 1% | 38% | 3 |
| 4 | ACCOUNTING FINANCE INFORMAT SYST BUSINESS | 69874 | 0% | 100% | 1 |
| 5 | AVERT S | 69874 | 0% | 100% | 1 |
| 6 | CHAIR IT SECUR | 69874 | 0% | 100% | 1 |
| 7 | CIDRE TEAM | 69874 | 0% | 100% | 1 |
| 8 | CSE ECE | 69874 | 0% | 100% | 1 |
| 9 | CYBER SECUR S | 69874 | 0% | 100% | 1 |
| 10 | DIGITAL VACCINE | 69874 | 0% | 100% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | COMPUTERS & SECURITY | 63719 | 8% | 3% | 33 |
| 2 | SECURITY AND COMMUNICATION NETWORKS | 36752 | 6% | 2% | 27 |
| 3 | DIGITAL INVESTIGATION | 27501 | 3% | 3% | 13 |
| 4 | IEEE SECURITY & PRIVACY | 24847 | 3% | 2% | 15 |
| 5 | IET INFORMATION SECURITY | 17560 | 2% | 3% | 9 |
| 6 | IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY | 12646 | 4% | 1% | 16 |
| 7 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 11749 | 2% | 2% | 9 |
| 8 | INTERNATIONAL JOURNAL OF INFORMATION SECURITY | 8753 | 1% | 2% | 6 |
| 9 | PERVASIVE AND MOBILE COMPUTING | 6471 | 2% | 1% | 7 |
| 10 | COMPUTER | 3256 | 3% | 0% | 12 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | MALWARE DETECTION | 2146496 | 11% | 64% | 48 | Search MALWARE+DETECTION | Search MALWARE+DETECTION |
| 2 | MALWARE | 1117913 | 12% | 31% | 52 | Search MALWARE | Search MALWARE |
| 3 | ANDROID SECURITY | 924800 | 3% | 88% | 15 | Search ANDROID+SECURITY | Search ANDROID+SECURITY |
| 4 | MALWARE ANALYSIS | 655058 | 3% | 63% | 15 | Search MALWARE+ANALYSIS | Search MALWARE+ANALYSIS |
| 5 | ANDROID MALWARE | 537488 | 2% | 77% | 10 | Search ANDROID+MALWARE | Search ANDROID+MALWARE |
| 6 | SMARTPHONE SECURITY | 529563 | 3% | 63% | 12 | Search SMARTPHONE+SECURITY | Search SMARTPHONE+SECURITY |
| 7 | ANDROID | 494415 | 11% | 15% | 46 | Search ANDROID | Search ANDROID |
| 8 | MALWARE CLASSIFICATION | 489118 | 2% | 100% | 7 | Search MALWARE+CLASSIFICATION | Search MALWARE+CLASSIFICATION |
| 9 | MOBILE MALWARE | 465820 | 2% | 67% | 10 | Search MOBILE+MALWARE | Search MOBILE+MALWARE |
| 10 | DYNAMIC MALWARE ANALYSIS | 279496 | 1% | 100% | 4 | Search DYNAMIC+MALWARE+ANALYSIS | Search DYNAMIC+MALWARE+ANALYSIS |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | FEIZOLLAH, A , ANUAR, NB , SALLEH, R , WAHAB, AWA , (2015) A REVIEW ON FEATURE SELECTION IN MOBILE MALWARE DETECTION.DIGITAL INVESTIGATION. VOL. 13. ISSUE . P. 22 -37 | 14 | 74% | 6 |
| 2 | NISSIM, N , COHEN, A , GLEZER, C , ELOVICI, Y , (2015) DETECTION OF MALICIOUS PDF FILES AND DIRECTIONS FOR ENHANCEMENTS: A STATE-OF-THE ART SURVEY.COMPUTERS & SECURITY. VOL. 48. ISSUE . P. 246 -266 | 11 | 85% | 1 |
| 3 | FARUKI, P , BHARMAL, A , LAXMI, V , GANMOOR, V , GAUR, MS , CONTI, M , RAJARAJAN, M , (2015) ANDROID SECURITY: A SURVEY OF ISSUES, MALWARE PENETRATION, AND DEFENSES.IEEE COMMUNICATIONS SURVEYS AND TUTORIALS. VOL. 17. ISSUE 2. P. 998 -1022 | 7 | 100% | 14 |
| 4 | NISSIM, N , MOSKOVITCH, R , BARAD, O , ROKACH, L , ELOVICI, Y , (2016) ALDROID: EFFICIENT UPDATE OF ANDROID ANTI-VIRUS SOFTWARE USING DESIGNATED ACTIVE LEARNING METHODS.KNOWLEDGE AND INFORMATION SYSTEMS. VOL. 49. ISSUE 3. P. 795 -833 | 12 | 71% | 0 |
| 5 | SUFATRIO , TAN, DJJ , CHUA, TW , THING, VLL , (2015) SECURING ANDROID: A SURVEY, TAXONOMY, AND CHALLENGES.ACM COMPUTING SURVEYS. VOL. 47. ISSUE 4. P. - | 10 | 77% | 2 |
| 6 | LA POLLA, M , MARTINELLI, F , SGANDURRA, D , (2013) A SURVEY ON SECURITY FOR MOBILE DEVICES.IEEE COMMUNICATIONS SURVEYS AND TUTORIALS. VOL. 15. ISSUE 1. P. 446 -471 | 10 | 59% | 69 |
| 7 | SUAREZ-TANGIL, G , TAPIADOR, JE , LOMBARDI, F , DI PIETRO, R , (2016) ALTERDROID: DIFFERENTIAL FAULT ANALYSIS OF OBFUSCATED SMARTPHONE MALWARE.IEEE TRANSACTIONS ON MOBILE COMPUTING. VOL. 15. ISSUE 4. P. 789 -802 | 8 | 89% | 0 |
| 8 | MIAO, QG , LIU, JC , CAO, Y , SONG, JF , (2016) MALWARE DETECTION USING BILAYER BEHAVIOR ABSTRACTION AND IMPROVED ONE-CLASS SUPPORT VECTOR MACHINES.INTERNATIONAL JOURNAL OF INFORMATION SECURITY. VOL. 15. ISSUE 4. P. 361 -379 | 9 | 75% | 0 |
| 9 | GHIASI, M , SAMI, A , SALEHI, Z , (2015) DYNAMIC VSA: A FRAMEWORK FOR MALWARE DETECTION BASED ON REGISTER CONTENTS.ENGINEERING APPLICATIONS OF ARTIFICIAL INTELLIGENCE. VOL. 44. ISSUE . P. 111 -122 | 6 | 100% | 3 |
| 10 | AB RAZAK, MF , ANUAR, NB , SALLEH, R , FIRDAUS, A , (2016) THE RISE OF "MALWARE": BIBLIOMETRIC ANALYSIS OF MALWARE STUDY.JOURNAL OF NETWORK AND COMPUTER APPLICATIONS. VOL. 75. ISSUE . P. 58 -76 | 17 | 35% | 0 |
Classes with closest relation at Level 1 |