Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
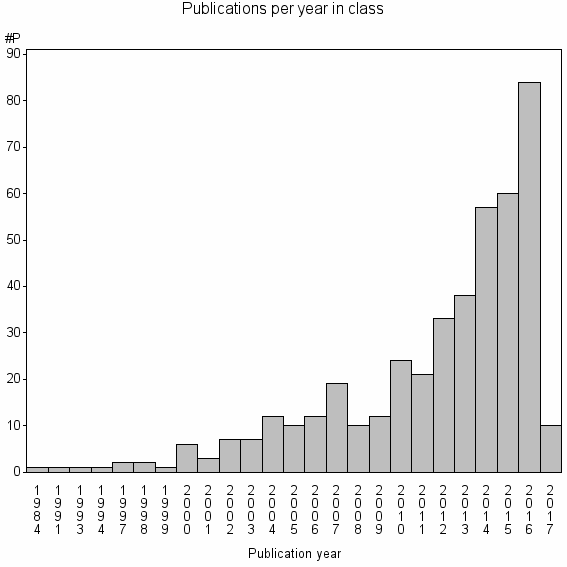
| 21091 | 434 | 26.8 | 39% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
| Cluster id | Level | Cluster label | #P |
|---|---|---|---|
| 9 | 4 | COMPUTER SCIENCE, THEORY & METHODS//COMPUTER SCIENCE, ARTIFICIAL INTELLIGENCE//COMPUTER SCIENCE, INFORMATION SYSTEMS | 1247339 |
| 295 | 3 | CRYPTOGRAPHY//COMPUTER SCIENCE, THEORY & METHODS//IEEE TRANSACTIONS ON INFORMATION THEORY | 41419 |
| 2473 | 2 | BLOCK CIPHER//STREAM CIPHER//BOOLEAN FUNCTIONS | 3978 |
| 21091 | 1 | HARDWARE SECURITY//PHYSICAL UNCLONABLE FUNCTION//HARDWARE TROJAN | 434 |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | HARDWARE SECURITY | authKW | 2010930 | 12% | 56% | 51 |
| 2 | PHYSICAL UNCLONABLE FUNCTION | authKW | 1827372 | 7% | 84% | 31 |
| 3 | HARDWARE TROJAN | authKW | 1709671 | 6% | 90% | 27 |
| 4 | PHYSICAL UNCLONABLE FUNCTION PUF | authKW | 811170 | 3% | 82% | 14 |
| 5 | IP PROTECTION | authKW | 719551 | 3% | 68% | 15 |
| 6 | INTELLECTUAL PROPERTY PROTECTION IPP | authKW | 639608 | 2% | 91% | 10 |
| 7 | HARDWARE TROJAN DETECTION | authKW | 633213 | 2% | 100% | 9 |
| 8 | INTELLECTUAL PROPERTY IP PROTECTION | authKW | 500315 | 2% | 89% | 8 |
| 9 | SCAN BASED ATTACK | authKW | 492499 | 2% | 100% | 7 |
| 10 | HARDWARE METERING | authKW | 422142 | 1% | 100% | 6 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Hardware & Architecture | 31677 | 48% | 0% | 208 |
| 2 | Engineering, Electrical & Electronic | 6635 | 71% | 0% | 308 |
| 3 | Computer Science, Theory & Methods | 2218 | 20% | 0% | 87 |
| 4 | Computer Science, Software Engineering | 1479 | 14% | 0% | 60 |
| 5 | Computer Science, Information Systems | 1239 | 14% | 0% | 62 |
| 6 | Computer Science, Interdisciplinary Applications | 822 | 12% | 0% | 53 |
| 7 | Telecommunications | 88 | 4% | 0% | 19 |
| 8 | Nanoscience & Nanotechnology | 11 | 3% | 0% | 12 |
| 9 | Physics, Applied | 5 | 6% | 0% | 24 |
| 10 | Engineering, Manufacturing | 2 | 1% | 0% | 3 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | AD T COMP EMBEDDED SYST ACES | 70357 | 0% | 100% | 1 |
| 2 | ASSURANCE ENGN | 70357 | 0% | 100% | 1 |
| 3 | BUSINESS DEV GOVT RELAT | 70357 | 0% | 100% | 1 |
| 4 | CHAIR SECUR INFORMAT TECHNOL | 70357 | 0% | 100% | 1 |
| 5 | COMP SCI TELECOMMUN IMAGE PROC | 70357 | 0% | 100% | 1 |
| 6 | COSIC COMP SECUR IND CRYPTOG | 70357 | 0% | 100% | 1 |
| 7 | CRISSP ABU DHABI | 70357 | 0% | 100% | 1 |
| 8 | CRYPTOL COMP SECUR LOCCS | 70357 | 0% | 100% | 1 |
| 9 | DESIGN FOR EXCELLENCE | 70357 | 0% | 100% | 1 |
| 10 | DFX | 70357 | 0% | 100% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY | 50997 | 7% | 2% | 32 |
| 2 | IEEE DESIGN & TEST | 44231 | 2% | 6% | 10 |
| 3 | JOURNAL OF ELECTRONIC TESTING-THEORY AND APPLICATIONS | 40818 | 6% | 2% | 25 |
| 4 | IEEE TRANSACTIONS ON COMPUTER-AIDED DESIGN OF INTEGRATED CIRCUITS AND SYSTEMS | 32012 | 11% | 1% | 47 |
| 5 | IEEE TRANSACTIONS ON EMERGING TOPICS IN COMPUTING | 28128 | 2% | 5% | 8 |
| 6 | IEEE TRANSACTIONS ON VERY LARGE SCALE INTEGRATION (VLSI) SYSTEMS | 16259 | 6% | 1% | 28 |
| 7 | IEEE DESIGN & TEST OF COMPUTERS | 13972 | 3% | 1% | 14 |
| 8 | IET COMPUTERS AND DIGITAL TECHNIQUES | 10383 | 2% | 2% | 8 |
| 9 | ACM TRANSACTIONS ON DESIGN AUTOMATION OF ELECTRONIC SYSTEMS | 7530 | 2% | 1% | 9 |
| 10 | MICROPROCESSORS AND MICROSYSTEMS | 6792 | 3% | 1% | 13 |
Author Key Words |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | ZHANG, JL , QU, G , LV, YQ , ZHOU, Q , (2014) A SURVEY ON SILICON PUFS AND RECENT ADVANCES IN RING OSCILLATOR PUFS.JOURNAL OF COMPUTER SCIENCE AND TECHNOLOGY. VOL. 29. ISSUE 4. P. 664 -678 | 24 | 96% | 7 |
| 2 | COLOMBIER, B , BOSSUET, L , (2014) SURVEY OF HARDWARE PROTECTION OF DESIGN DATA FOR INTEGRATED CIRCUITS AND INTELLECTUAL PROPERTIES.IET COMPUTERS AND DIGITAL TECHNIQUES. VOL. 8. ISSUE 6. P. 274 -287 | 17 | 94% | 2 |
| 3 | LIANG, W , LIAO, B , LONG, J , JIANG, Y , PENG, L , (2016) STUDY ON PUF BASED SECURE PROTECTION FOR IC DESIGN.MICROPROCESSORS AND MICROSYSTEMS. VOL. 45. ISSUE . P. 56 -66 | 19 | 76% | 0 |
| 4 | BHUNIA, S , HSIAO, MS , BANGA, M , NARASIMHAN, S , (2014) HARDWARE TROJAN ATTACKS: THREAT ANALYSIS AND COUNTERMEASURES.PROCEEDINGS OF THE IEEE. VOL. 102. ISSUE 8. P. 1229 -1247 | 15 | 75% | 37 |
| 5 | GUIN, U , HUANG, K , DIMASE, D , CARULLI, JM , TEHRANIPOOR, M , MAKRIS, Y , (2014) COUNTERFEIT INTEGRATED CIRCUITS: A RISING THREAT IN THE GLOBAL SEMICONDUCTOR SUPPLY CHAIN.PROCEEDINGS OF THE IEEE. VOL. 102. ISSUE 8. P. 1207 -1228 | 16 | 76% | 18 |
| 6 | WU, TF , GANESAN, K , HU, YA , WONG, HSP , WONG, S , MITRA, S , (2016) TPAD: HARDWARE TROJAN PREVENTION AND DETECTION FOR TRUSTED INTEGRATED CIRCUITS.IEEE TRANSACTIONS ON COMPUTER-AIDED DESIGN OF INTEGRATED CIRCUITS AND SYSTEMS. VOL. 35. ISSUE 4. P. 521 -534 | 18 | 69% | 1 |
| 7 | ROSTAMI, M , KOUSHANFAR, F , KARRI, R , (2014) A PRIMER ON HARDWARE SECURITY: MODELS, METHODS, AND METRICS.PROCEEDINGS OF THE IEEE. VOL. 102. ISSUE 8. P. 1283 -1295 | 16 | 67% | 33 |
| 8 | LV, YQ , ZHOU, Q , CAI, YC , QU, G , (2014) TRUSTED INTEGRATED CIRCUITS: THE PROBLEM AND CHALLENGES.JOURNAL OF COMPUTER SCIENCE AND TECHNOLOGY. VOL. 29. ISSUE 5. P. 918 -928 | 16 | 84% | 1 |
| 9 | LONG, J , ZHANG, DF , ZUO, C , DUAN, JJ , HUANG, WH , (2016) A ROBUST LOW-OVERHEAD WATERMARKING FOR FIELD AUTHENTICATION OF INTELLECTUAL PROPERTY CORES.COMPUTER SCIENCE AND INFORMATION SYSTEMS. VOL. 13. ISSUE 2. P. 609 -622 | 14 | 88% | 0 |
| 10 | ZHANG, JL , LIN, YP , LYU, YQ , QU, G , (2015) A PUF-FSM BINDING SCHEME FOR FPGA IP PROTECTION AND PAY-PER-DEVICE LICENSING.IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY. VOL. 10. ISSUE 6. P. 1137 -1150 | 12 | 92% | 7 |
Classes with closest relation at Level 1 |