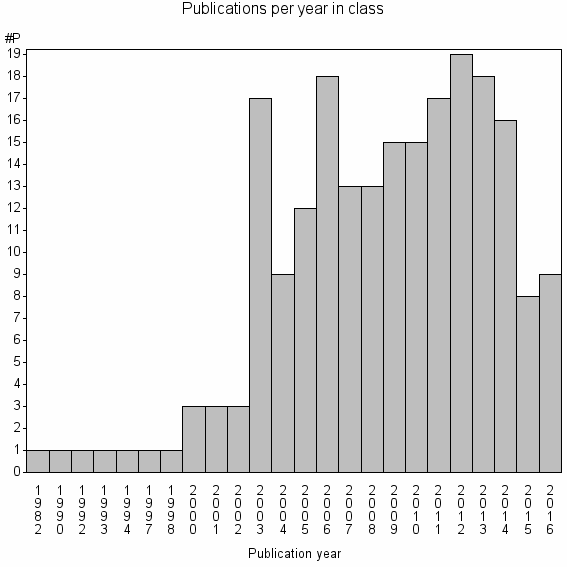
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 28047 | 215 | 22.5 | 20% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | HIMALIS | authKW | 568100 | 2% | 100% | 4 |
| 2 | FUTURE NETWORK | authKW | 443825 | 2% | 63% | 5 |
| 3 | NEW GENERATION NETWORK | authKW | 340853 | 3% | 40% | 6 |
| 4 | SINGLE SIGN ON | authKW | 293201 | 4% | 26% | 8 |
| 5 | BEYOND WEB | authKW | 284050 | 1% | 100% | 2 |
| 6 | NCE UFRJ COMP | address | 284050 | 1% | 100% | 2 |
| 7 | TRUSTED PERSONAL DEVICE | authKW | 284050 | 1% | 100% | 2 |
| 8 | IDENTITY MANAGEMENT | authKW | 270784 | 7% | 13% | 15 |
| 9 | ID LOCATOR SPLIT | authKW | 252485 | 2% | 44% | 4 |
| 10 | INFORMAT COMMUN ENGN DIIC | address | 206577 | 2% | 36% | 4 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Software Engineering | 4625 | 34% | 0% | 73 |
| 2 | Computer Science, Information Systems | 4301 | 37% | 0% | 79 |
| 3 | Telecommunications | 3038 | 32% | 0% | 68 |
| 4 | Computer Science, Theory & Methods | 2983 | 33% | 0% | 70 |
| 5 | Computer Science, Hardware & Architecture | 1664 | 16% | 0% | 34 |
| 6 | Engineering, Electrical & Electronic | 117 | 16% | 0% | 34 |
| 7 | Computer Science, Interdisciplinary Applications | 48 | 5% | 0% | 10 |
| 8 | Computer Science, Artificial Intelligence | 31 | 4% | 0% | 8 |
| 9 | Public Administration | 13 | 1% | 0% | 2 |
| 10 | Information Science & Library Science | 12 | 1% | 0% | 3 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | NCE UFRJ COMP | 284050 | 1% | 100% | 2 |
| 2 | INFORMAT COMMUN ENGN DIIC | 206577 | 2% | 36% | 4 |
| 3 | ABT INFORMAT WIRT AFT MANAGEMENT | 142025 | 0% | 100% | 1 |
| 4 | ABT IPE | 142025 | 0% | 100% | 1 |
| 5 | ADV COMMUNITY INFORMAT SYST ACIS GRP | 142025 | 0% | 100% | 1 |
| 6 | AREA INFORMAT SYST SECUR | 142025 | 0% | 100% | 1 |
| 7 | FUTURE NETWORKS GRP | 142025 | 0% | 100% | 1 |
| 8 | IDENT MANAGEMENT AREA | 142025 | 0% | 100% | 1 |
| 9 | IT AVEIRO | 142025 | 0% | 100% | 1 |
| 10 | KURENTO ORG INITIAT | 142025 | 0% | 100% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | IEEE SECURITY & PRIVACY | 37953 | 6% | 2% | 13 |
| 2 | CHINA COMMUNICATIONS | 16573 | 6% | 1% | 13 |
| 3 | IEEE INTERNET COMPUTING | 12299 | 4% | 1% | 9 |
| 4 | COMPUTER SYSTEMS SCIENCE AND ENGINEERING | 9277 | 3% | 1% | 7 |
| 5 | INTERNATIONAL JOURNAL OF INFORMATION SECURITY | 4448 | 1% | 1% | 3 |
| 6 | COMPUTERS & SECURITY | 4274 | 3% | 1% | 6 |
| 7 | COMPUTER | 3732 | 4% | 0% | 9 |
| 8 | LECTURE NOTES IN COMPUTER SCIENCE | 2536 | 19% | 0% | 40 |
| 9 | JOURNAL OF UNIVERSAL COMPUTER SCIENCE | 2058 | 2% | 0% | 5 |
| 10 | IEEE COMMUNICATIONS MAGAZINE | 2046 | 4% | 0% | 8 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | HIMALIS | 568100 | 2% | 100% | 4 | Search HIMALIS | Search HIMALIS |
| 2 | FUTURE NETWORK | 443825 | 2% | 63% | 5 | Search FUTURE+NETWORK | Search FUTURE+NETWORK |
| 3 | NEW GENERATION NETWORK | 340853 | 3% | 40% | 6 | Search NEW+GENERATION+NETWORK | Search NEW+GENERATION+NETWORK |
| 4 | SINGLE SIGN ON | 293201 | 4% | 26% | 8 | Search SINGLE+SIGN+ON | Search SINGLE+SIGN+ON |
| 5 | BEYOND WEB | 284050 | 1% | 100% | 2 | Search BEYOND+WEB | Search BEYOND+WEB |
| 6 | TRUSTED PERSONAL DEVICE | 284050 | 1% | 100% | 2 | Search TRUSTED+PERSONAL+DEVICE | Search TRUSTED+PERSONAL+DEVICE |
| 7 | IDENTITY MANAGEMENT | 270784 | 7% | 13% | 15 | Search IDENTITY+MANAGEMENT | Search IDENTITY+MANAGEMENT |
| 8 | ID LOCATOR SPLIT | 252485 | 2% | 44% | 4 | Search ID+LOCATOR+SPLIT | Search ID+LOCATOR+SPLIT |
| 9 | AUTHENTICATION AND AUTHORIZATION INFRASTRUCTURE | 189365 | 1% | 67% | 2 | Search AUTHENTICATION+AND+AUTHORIZATION+INFRASTRUCTURE | Search AUTHENTICATION+AND+AUTHORIZATION+INFRASTRUCTURE |
| 10 | EDUROAM | 189365 | 1% | 67% | 2 | Search EDUROAM | Search EDUROAM |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | BELTRAN, V , BERTIN, E , (2015) UNIFIED COMMUNICATIONS AS A SERVICE AND WEBRTC: AN IDENTITY-CENTRIC PERSPECTIVE.COMPUTER COMMUNICATIONS. VOL. 68. ISSUE . P. 73 -82 | 6 | 86% | 0 |
| 2 | NEPAL, S , ZIC, J , LIU, DX , JANG, JL , (2011) A MOBILE AND PORTABLE TRUSTED COMPUTING PLATFORM.EURASIP JOURNAL ON WIRELESS COMMUNICATIONS AND NETWORKING. VOL. . ISSUE . P. 1 -19 | 6 | 86% | 1 |
| 3 | MENDEZ, AP , LOPEZ, RM , MILIAN, GL , (2016) PROVIDING EFFICIENT SSO TO CLOUD SERVICE ACCESS IN AAA-BASED IDENTITY FEDERATIONS.FUTURE GENERATION COMPUTER SYSTEMS-THE INTERNATIONAL JOURNAL OF ESCIENCE. VOL. 58. ISSUE . P. 13 -28 | 6 | 75% | 0 |
| 4 | TORMO, GD , MILLAN, GL , PEREZ, GM , (2013) DEFINITION OF AN ADVANCED IDENTITY MANAGEMENT INFRASTRUCTURE.INTERNATIONAL JOURNAL OF INFORMATION SECURITY. VOL. 12. ISSUE 3. P. 173-200 | 8 | 57% | 1 |
| 5 | CHA, SC , CHANG, HM , (2012) EFFICIENT CONSISTENCY ACHIEVEMENT OF FEDERATED IDENTITY AND ACCESS MANAGEMENT BASED ON A NOVEL SELF-ADAPTABLE APPROACH.IEICE TRANSACTIONS ON INFORMATION AND SYSTEMS. VOL. E95D. ISSUE 2. P. 577-587 | 6 | 75% | 0 |
| 6 | ZHAO, GS , BA, ZJ , WANG, XM , ZHANG, F , HUANG, CQ , TANG, Y , (2016) CONSTRUCTING AUTHENTICATION WEB IN CLOUD COMPUTING.SECURITY AND COMMUNICATION NETWORKS. VOL. 9. ISSUE 15. P. 2843 -2860 | 6 | 67% | 0 |
| 7 | MARTINEZ-JULIA, P , SKARMETA, AF , (2014) EMPOWERING SECURITY AND MOBILITY IN FUTURE NETWORKS WITH AN IDENTITY-BASED CONTROL PLANE.IEICE TRANSACTIONS ON COMMUNICATIONS. VOL. E97B. ISSUE 12. P. 2571 -2582 | 5 | 71% | 0 |
| 8 | SCHLAGER, C , NOWEY, T , (2006) TOWARDS A RISK MANAGEMENT PERSPECTIVE ON AAIS.TRUST, PRIVACY, AND SECURITY IN DIGITAL BUSINESS, PROCEEDINGS. VOL. 4083. ISSUE . P. 41-50 | 5 | 83% | 2 |
| 9 | POURSALIDIS, V , NIKOLAOU, C , (2007) TOWARDS A PERSON-CENTRIC IDENTITY MANAGEMENT INFRASTRUCTURE (IMI).COMPUTER SYSTEMS SCIENCE AND ENGINEERING. VOL. 22. ISSUE 5. P. 255 -266 | 4 | 100% | 1 |
| 10 | HE, JS , ZHANG, R , (2005) TOWARDS A FORMAL FRAMEWORK FOR DISTRIBUTED IDENTITY MANAGEMENT.WEB TECHNOLOGIES RESEARCH AND DEVELOPMENT - APWEB 2005. VOL. 3399. ISSUE . P. 913-924 | 5 | 83% | 0 |
Classes with closest relation at Level 1 |