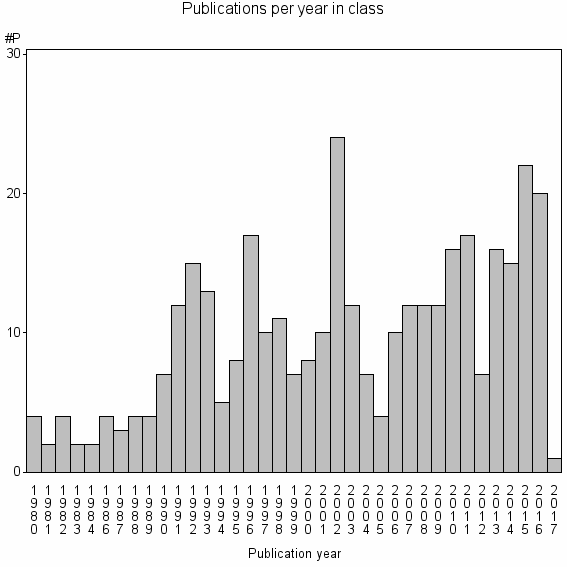
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 23071 | 359 | 38.8 | 33% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
| Cluster id | Level | Cluster label | #P |
|---|---|---|---|
| 1 | 4 | ECONOMICS//EDUCATION & EDUCATIONAL RESEARCH//PSYCHOL | 3876184 |
| 310 | 3 | INFORMATION SCIENCE & LIBRARY SCIENCE//INFORMATION & MANAGEMENT//GOVERNMENT INFORMATION QUARTERLY | 40167 |
| 2745 | 2 | INFORMATION PRIVACY//PRIVACY//PRIVACY CONCERN | 3226 |
| 23071 | 1 | CYBERLOAFING//CYBERSLACKING//NON WORK RELATED COMPUTING | 359 |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | CYBERLOAFING | authKW | 1749717 | 7% | 86% | 24 |
| 2 | CYBERSLACKING | authKW | 773235 | 3% | 91% | 10 |
| 3 | NON WORK RELATED COMPUTING | authKW | 425280 | 1% | 100% | 5 |
| 4 | INTERNET MISUSE | authKW | 255168 | 1% | 100% | 3 |
| 5 | PERSONAL USE OF THE INTERNET | authKW | 255168 | 1% | 100% | 3 |
| 6 | PERSONAL WEB USAGE | authKW | 255168 | 1% | 100% | 3 |
| 7 | EMPLOYEE MONITORING | authKW | 191375 | 1% | 75% | 3 |
| 8 | COMPUTERIZED PERFORMANCE MONITORING | authKW | 170112 | 1% | 100% | 2 |
| 9 | CYBERDEVIANCY | authKW | 170112 | 1% | 100% | 2 |
| 10 | CYBERLOAFING ANTECEDENTS | authKW | 170112 | 1% | 100% | 2 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Industrial Relations & Labor | 4763 | 10% | 0% | 35 |
| 2 | Psychology, Applied | 4263 | 17% | 0% | 62 |
| 3 | Management | 3888 | 23% | 0% | 82 |
| 4 | Ergonomics | 2442 | 8% | 0% | 28 |
| 5 | Business | 1996 | 14% | 0% | 50 |
| 6 | Information Science & Library Science | 1243 | 9% | 0% | 34 |
| 7 | Ethics | 970 | 6% | 0% | 20 |
| 8 | Law | 821 | 9% | 0% | 33 |
| 9 | Communication | 679 | 6% | 0% | 20 |
| 10 | Public Administration | 526 | 4% | 0% | 15 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | CURSO SISTEMAS INTERNET | 85056 | 0% | 100% | 1 |
| 2 | EXPT PSYCHOL INTERNET SCI | 85056 | 0% | 100% | 1 |
| 3 | FR ARBEITS ORG PSYCHOL | 85056 | 0% | 100% | 1 |
| 4 | GRP PESQUISA GESTAO TECNOL SEGURANCA INFORMACAO | 85056 | 0% | 100% | 1 |
| 5 | GTSEG | 85056 | 0% | 100% | 1 |
| 6 | LIFELONG LEARNING TEACHER EDUC | 85056 | 0% | 100% | 1 |
| 7 | LIVERPOOL ADV POLICING STUDIES | 85056 | 0% | 100% | 1 |
| 8 | LOCAL GOVT FED CREDIT UNION FELLOWS PROGRAM | 85056 | 0% | 100% | 1 |
| 9 | MANAGEMENT MKT INFORMAT SYST SCI | 85056 | 0% | 100% | 1 |
| 10 | MANAGEMENT SK SUPEX FELLOW | 85056 | 0% | 100% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | NEW TECHNOLOGY WORK AND EMPLOYMENT | 30885 | 3% | 3% | 11 |
| 2 | CYBERPSYCHOLOGY & BEHAVIOR | 14403 | 3% | 1% | 12 |
| 3 | COMPUTERS IN HUMAN BEHAVIOR | 9902 | 6% | 1% | 23 |
| 4 | EMPLOYEE RELATIONS LAW JOURNAL | 9211 | 2% | 2% | 6 |
| 5 | WORKFORCE | 8829 | 1% | 3% | 4 |
| 6 | LABOR LAW JOURNAL | 4538 | 2% | 1% | 6 |
| 7 | JOURNAL OF BUSINESS ETHICS | 4349 | 5% | 0% | 18 |
| 8 | COMMUNICATIONS OF THE ACM | 3950 | 4% | 0% | 14 |
| 9 | HUMAN RESOURCE MANAGEMENT REVIEW | 3710 | 1% | 1% | 4 |
| 10 | IEEE TECHNOLOGY AND SOCIETY MAGAZINE | 3536 | 1% | 1% | 4 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | CYBERLOAFING | 1749717 | 7% | 86% | 24 | Search CYBERLOAFING | Search CYBERLOAFING |
| 2 | CYBERSLACKING | 773235 | 3% | 91% | 10 | Search CYBERSLACKING | Search CYBERSLACKING |
| 3 | NON WORK RELATED COMPUTING | 425280 | 1% | 100% | 5 | Search NON+WORK+RELATED+COMPUTING | Search NON+WORK+RELATED+COMPUTING |
| 4 | INTERNET MISUSE | 255168 | 1% | 100% | 3 | Search INTERNET+MISUSE | Search INTERNET+MISUSE |
| 5 | PERSONAL USE OF THE INTERNET | 255168 | 1% | 100% | 3 | Search PERSONAL+USE+OF+THE+INTERNET | Search PERSONAL+USE+OF+THE+INTERNET |
| 6 | PERSONAL WEB USAGE | 255168 | 1% | 100% | 3 | Search PERSONAL+WEB+USAGE | Search PERSONAL+WEB+USAGE |
| 7 | EMPLOYEE MONITORING | 191375 | 1% | 75% | 3 | Search EMPLOYEE+MONITORING | Search EMPLOYEE+MONITORING |
| 8 | COMPUTERIZED PERFORMANCE MONITORING | 170112 | 1% | 100% | 2 | Search COMPUTERIZED+PERFORMANCE+MONITORING | Search COMPUTERIZED+PERFORMANCE+MONITORING |
| 9 | CYBERDEVIANCY | 170112 | 1% | 100% | 2 | Search CYBERDEVIANCY | Search CYBERDEVIANCY |
| 10 | CYBERLOAFING ANTECEDENTS | 170112 | 1% | 100% | 2 | Search CYBERLOAFING+ANTECEDENTS | Search CYBERLOAFING+ANTECEDENTS |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | AKBULUT, Y , DURSUN, OO , DONMEZ, O , SAHIN, YL , (2016) IN SEARCH OF A MEASURE TO INVESTIGATE CYBERLOAFING IN EDUCATIONAL SETTINGS.COMPUTERS IN HUMAN BEHAVIOR. VOL. 55. ISSUE . P. 616 -625 | 23 | 53% | 2 |
| 2 | SHEIKH, A , ATASHGAH, MS , ADIBZADEGAN, M , (2015) THE ANTECEDENTS OF CYBERLOAFING: A CASE STUDY IN AN IRANIAN COPPER INDUSTRY.COMPUTERS IN HUMAN BEHAVIOR. VOL. 51. ISSUE . P. 172 -179 | 21 | 64% | 2 |
| 3 | CROUSE, J , LAROSE, R , VITAK, J , (2011) PERSONAL INTERNET USE AT WORK: UNDERSTANDING CYBERSLACKING.COMPUTERS IN HUMAN BEHAVIOR. VOL. 27. ISSUE 5. P. 1751 -1759 | 18 | 72% | 38 |
| 4 | WEST, JP , BOWMAN, JS , (2016) ELECTRONIC SURVEILLANCE AT WORK: AN ETHICAL ANALYSIS.ADMINISTRATION & SOCIETY. VOL. 48. ISSUE 5. P. 628 -651 | 14 | 88% | 0 |
| 5 | RAHIMNIA, F , MAZIDI, ARK , (2015) FUNCTIONS OF CONTROL MECHANISMS IN MITIGATING WORKPLACE LOAFING; EVIDENCE FROM AN ISLAMIC SOCIETY.COMPUTERS IN HUMAN BEHAVIOR. VOL. 48. ISSUE . P. 671 -681 | 20 | 49% | 2 |
| 6 | MCNALL, LA , STANTON, JM , (2011) PRIVATE EYES ARE WATCHING YOU: REACTIONS TO LOCATION SENSING TECHNOLOGIES.JOURNAL OF BUSINESS AND PSYCHOLOGY. VOL. 26. ISSUE 3. P. 299 -309 | 15 | 71% | 3 |
| 7 | ALDER, GS , SCHMINKE, M , NOEL, TW , KUENZI, M , (2008) EMPLOYEE REACTIONS TO INTERNET MONITORING: THE MODERATING ROLE OF ETHICAL ORIENTATION.JOURNAL OF BUSINESS ETHICS. VOL. 80. ISSUE 3. P. 481 -498 | 21 | 54% | 7 |
| 8 | PAGE, D , (2015) TEACHERS' PERSONAL WEB USE AT WORK.BEHAVIOUR & INFORMATION TECHNOLOGY. VOL. 34. ISSUE 5. P. 443 -453 | 20 | 48% | 1 |
| 9 | BLANCHARD, AL , HENLE, CA , (2008) CORRELATES OF DIFFERENT FORMS OF CYBERLOAFING: THE ROLE OF NORMS AND EXTERNAL LOCUS OF CONTROL.COMPUTERS IN HUMAN BEHAVIOR. VOL. 24. ISSUE 3. P. 1067-1084 | 16 | 59% | 47 |
| 10 | ANDREASSEN, CS , TORSHEIM, T , PALLESEN, S , (2014) PREDICTORS OF USE OF SOCIAL NETWORK SITES AT WORK - A SPECIFIC TYPE OF CYBERLOAFING.JOURNAL OF COMPUTER-MEDIATED COMMUNICATION. VOL. 19. ISSUE 4. P. 906 -921 | 17 | 49% | 8 |
Classes with closest relation at Level 1 |