Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
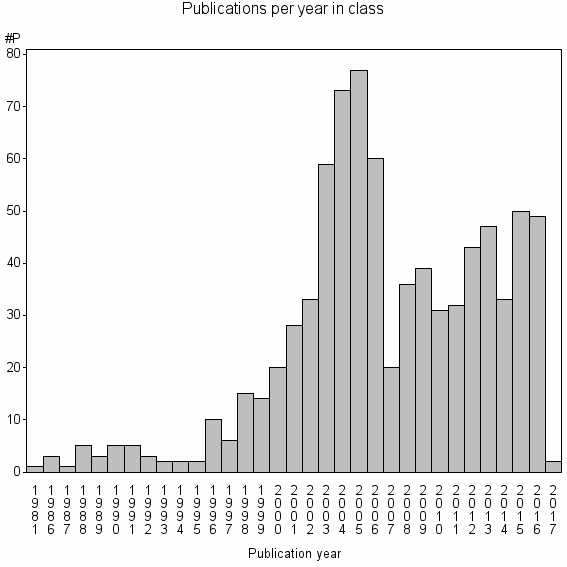
| 13842 | 809 | 25.4 | 28% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
| Cluster id | Level | Cluster label | #P |
|---|---|---|---|
| 9 | 4 | COMPUTER SCIENCE, THEORY & METHODS//COMPUTER SCIENCE, ARTIFICIAL INTELLIGENCE//COMPUTER SCIENCE, INFORMATION SYSTEMS | 1247339 |
| 295 | 3 | CRYPTOGRAPHY//COMPUTER SCIENCE, THEORY & METHODS//IEEE TRANSACTIONS ON INFORMATION THEORY | 41419 |
| 632 | 2 | AUTHENTICATION//CRYPTOGRAPHY//DIGITAL SIGNATURE | 13771 |
| 13842 | 1 | ELECTRONIC VOTING//MIX NET//ANONYMOUS COMMUNICATION | 809 |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | ELECTRONIC VOTING | authKW | 1140890 | 6% | 66% | 46 |
| 2 | MIX NET | authKW | 718915 | 2% | 95% | 20 |
| 3 | ANONYMOUS COMMUNICATION | authKW | 598879 | 4% | 55% | 29 |
| 4 | E VOTING | authKW | 554598 | 3% | 64% | 23 |
| 5 | RECEIPT FREENESS | authKW | 452918 | 1% | 100% | 12 |
| 6 | MIX NETWORKS | authKW | 424603 | 2% | 75% | 15 |
| 7 | ANONYMITY | authKW | 325749 | 11% | 9% | 91 |
| 8 | INTERNET VOTING | authKW | 269588 | 1% | 71% | 10 |
| 9 | ONION ROUTING | authKW | 209675 | 1% | 56% | 10 |
| 10 | HYBRID MIX | authKW | 188716 | 1% | 100% | 5 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Theory & Methods | 26159 | 49% | 0% | 399 |
| 2 | Computer Science, Information Systems | 19404 | 40% | 0% | 325 |
| 3 | Computer Science, Hardware & Architecture | 7197 | 17% | 0% | 137 |
| 4 | Computer Science, Software Engineering | 5554 | 19% | 0% | 157 |
| 5 | Telecommunications | 2030 | 14% | 0% | 111 |
| 6 | Engineering, Electrical & Electronic | 1149 | 24% | 0% | 192 |
| 7 | Computer Science, Interdisciplinary Applications | 665 | 8% | 0% | 67 |
| 8 | Information Science & Library Science | 201 | 3% | 0% | 22 |
| 9 | Computer Science, Artificial Intelligence | 200 | 5% | 0% | 38 |
| 10 | Computer Science, Cybernetics | 40 | 1% | 0% | 6 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | CYBER SECUR GRP | 56612 | 0% | 50% | 3 |
| 2 | COMP SCI INFORMAT 4 | 50323 | 0% | 67% | 2 |
| 3 | NTT S | 47171 | 1% | 25% | 5 |
| 4 | AACHEN TRAFF | 37743 | 0% | 100% | 1 |
| 5 | CALIF PATH PROGRAM TRANSPORTAT STUDIES | 37743 | 0% | 100% | 1 |
| 6 | CH ELE OCOMMUN | 37743 | 0% | 100% | 1 |
| 7 | COMP SCI SYST SECUR GRP | 37743 | 0% | 100% | 1 |
| 8 | COMP THEORY SOFTWARE | 37743 | 0% | 100% | 1 |
| 9 | CONTEXT AWARE COMP GRP | 37743 | 0% | 100% | 1 |
| 10 | CRYPTOG SECUR PRIVACY | 37743 | 0% | 100% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | LECTURE NOTES IN COMPUTER SCIENCE | 29296 | 32% | 0% | 262 |
| 2 | ACM TRANSACTIONS ON INFORMATION AND SYSTEM SECURITY | 28734 | 1% | 6% | 12 |
| 3 | IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY | 24016 | 4% | 2% | 30 |
| 4 | INTERNATIONAL JOURNAL OF INFORMATION SECURITY | 18914 | 1% | 4% | 12 |
| 5 | COMPUTERS & SECURITY | 16691 | 3% | 2% | 23 |
| 6 | IEEE SECURITY & PRIVACY | 15257 | 2% | 3% | 16 |
| 7 | IEICE TRANSACTIONS ON FUNDAMENTALS OF ELECTRONICS COMMUNICATIONS AND COMPUTER SCIENCES | 6453 | 5% | 0% | 37 |
| 8 | SECURITY AND COMMUNICATION NETWORKS | 6106 | 2% | 1% | 15 |
| 9 | IET INFORMATION SECURITY | 5730 | 1% | 2% | 7 |
| 10 | COMMUNICATIONS OF THE ACM | 4315 | 3% | 1% | 22 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | ELECTRONIC VOTING | 1140890 | 6% | 66% | 46 | Search ELECTRONIC+VOTING | Search ELECTRONIC+VOTING |
| 2 | MIX NET | 718915 | 2% | 95% | 20 | Search MIX+NET | Search MIX+NET |
| 3 | ANONYMOUS COMMUNICATION | 598879 | 4% | 55% | 29 | Search ANONYMOUS+COMMUNICATION | Search ANONYMOUS+COMMUNICATION |
| 4 | E VOTING | 554598 | 3% | 64% | 23 | Search E+VOTING | Search E+VOTING |
| 5 | RECEIPT FREENESS | 452918 | 1% | 100% | 12 | Search RECEIPT+FREENESS | Search RECEIPT+FREENESS |
| 6 | MIX NETWORKS | 424603 | 2% | 75% | 15 | Search MIX+NETWORKS | Search MIX+NETWORKS |
| 7 | ANONYMITY | 325749 | 11% | 9% | 91 | Search ANONYMITY | Search ANONYMITY |
| 8 | INTERNET VOTING | 269588 | 1% | 71% | 10 | Search INTERNET+VOTING | Search INTERNET+VOTING |
| 9 | ONION ROUTING | 209675 | 1% | 56% | 10 | Search ONION+ROUTING | Search ONION+ROUTING |
| 10 | HYBRID MIX | 188716 | 1% | 100% | 5 | Search HYBRID+MIX | Search HYBRID+MIX |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | PENG, K , (2011) A GENERAL AND EFFICIENT COUNTERMEASURE TO RELATION ATTACKS IN MIX-BASED E-VOTING.INTERNATIONAL JOURNAL OF INFORMATION SECURITY. VOL. 10. ISSUE 1. P. 49-60 | 19 | 83% | 4 |
| 2 | PENG, K , (2011) AN EFFICIENT SHUFFLING BASED EVOTING SCHEME.JOURNAL OF SYSTEMS AND SOFTWARE. VOL. 84. ISSUE 6. P. 906 -922 | 17 | 77% | 3 |
| 3 | MOHAMMADPOURFARD, M , DOOSTARI, MA , GHOUSHCHI, MBG , SHAKIBA, N , (2015) A NEW SECURE INTERNET VOTING PROTOCOL USING JAVA CARD 3 TECHNOLOGY AND JAVA INFORMATION FLOW CONCEPT.SECURITY AND COMMUNICATION NETWORKS. VOL. 8. ISSUE 2. P. 261 -283 | 12 | 100% | 0 |
| 4 | JARDI-CEDO, R , PUJOL-AHULLO, J , CASTELLA-ROCA, J , VIEJO, A , (2012) STUDY ON POLL-SITE VOTING AND VERIFICATION SYSTEMS.COMPUTERS & SECURITY. VOL. 31. ISSUE 8. P. 989 -1010 | 15 | 83% | 0 |
| 5 | GARCIA, DAL , (2016) A FLEXIBLE E-VOTING SCHEME FOR DEBATE TOOLS.COMPUTERS & SECURITY. VOL. 56. ISSUE . P. 50 -62 | 12 | 86% | 0 |
| 6 | SEBE, F , MIRET, JM , PUJOLAS, J , PUIGGALI, J , (2010) SIMPLE AND EFFICIENT HASH-BASED VERIFIABLE MIXING FOR REMOTE ELECTRONIC VOTING.COMPUTER COMMUNICATIONS. VOL. 33. ISSUE 6. P. 667-675 | 13 | 87% | 1 |
| 7 | WU, ZY , WU, JC , LIN, SC , WANG, C , (2014) AN ELECTRONIC VOTING MECHANISM FOR FIGHTING BRIBERY AND COERCION.JOURNAL OF NETWORK AND COMPUTER APPLICATIONS. VOL. 40. ISSUE . P. 139-150 | 11 | 92% | 1 |
| 8 | PENG, K , (2013) EFFICIENT PROOF OF BID VALIDITY WITH UNTRUSTED VERIFIER IN HOMOMORPHIC E-AUCTION.IET INFORMATION SECURITY. VOL. 7. ISSUE 1. P. 11-21 | 11 | 92% | 3 |
| 9 | PENG, K , (2013) A SHUFFLE TO ACHIEVE HIGH EFFICIENCY THROUGH PRE-COMPUTATION AND BATCH VERIFICATION.INTERNATIONAL JOURNAL OF INFORMATION SECURITY. VOL. 12. ISSUE 4. P. 337-345 | 10 | 100% | 1 |
| 10 | SYTA, E , CORRIGAN-GIBBS, H , WENG, SC , WOLINSKY, D , FORD, B , JOHNSON, A , (2014) SECURITY ANALYSIS OF ACCOUNTABLE ANONYMITY IN DISSENT.ACM TRANSACTIONS ON INFORMATION AND SYSTEM SECURITY. VOL. 17. ISSUE 1. P. - | 14 | 70% | 0 |
Classes with closest relation at Level 1 |