Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
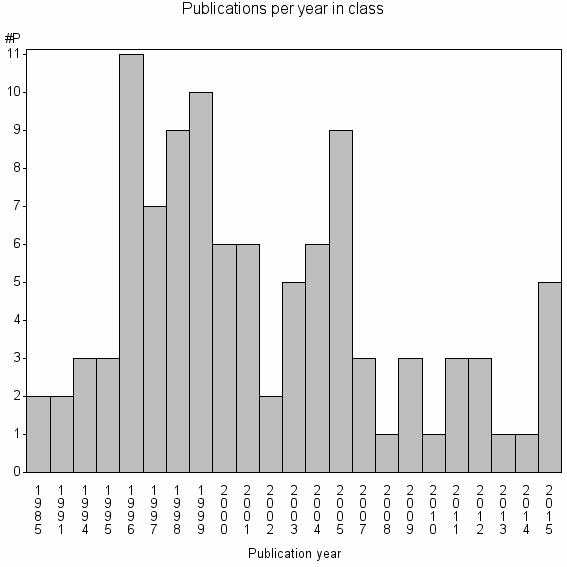
| 35134 | 102 | 20.2 | 23% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
| Cluster id | Level | Cluster label | #P |
|---|---|---|---|
| 9 | 4 | COMPUTER SCIENCE, THEORY & METHODS//COMPUTER SCIENCE, ARTIFICIAL INTELLIGENCE//COMPUTER SCIENCE, INFORMATION SYSTEMS | 1247339 |
| 295 | 3 | CRYPTOGRAPHY//COMPUTER SCIENCE, THEORY & METHODS//IEEE TRANSACTIONS ON INFORMATION THEORY | 41419 |
| 632 | 2 | AUTHENTICATION//CRYPTOGRAPHY//DIGITAL SIGNATURE | 13771 |
| 35134 | 1 | SUBLIMINAL CHANNEL//KEY ESCROW//HBEREICH ANGEW INFORMAT | 102 |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | SUBLIMINAL CHANNEL | authKW | 2806572 | 15% | 63% | 15 |
| 2 | KEY ESCROW | authKW | 831566 | 10% | 28% | 10 |
| 3 | HBEREICH ANGEW INFORMAT | address | 399157 | 2% | 67% | 2 |
| 4 | ACTIVE ATTACK DETECTABILITY | authKW | 299369 | 1% | 100% | 1 |
| 5 | ADV MOBILE TELECOMM | address | 299369 | 1% | 100% | 1 |
| 6 | ADVANCED THRESHOLD SCHEME | authKW | 299369 | 1% | 100% | 1 |
| 7 | AUCTIONS WITH CLOSED BIDS | authKW | 299369 | 1% | 100% | 1 |
| 8 | COHERENTIST JUSTIFICATION | authKW | 299369 | 1% | 100% | 1 |
| 9 | COLLISION RESISTANT FUNCTION | authKW | 299369 | 1% | 100% | 1 |
| 10 | COMMERCIAL KEY ESCROW | authKW | 299369 | 1% | 100% | 1 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Theory & Methods | 2069 | 39% | 0% | 40 |
| 2 | Computer Science, Information Systems | 1775 | 34% | 0% | 35 |
| 3 | Computer Science, Hardware & Architecture | 508 | 13% | 0% | 13 |
| 4 | Computer Science, Software Engineering | 293 | 13% | 0% | 13 |
| 5 | Philosophy | 91 | 5% | 0% | 5 |
| 6 | Engineering, Electrical & Electronic | 82 | 19% | 0% | 19 |
| 7 | Telecommunications | 77 | 8% | 0% | 8 |
| 8 | Computer Science, Artificial Intelligence | 42 | 6% | 0% | 6 |
| 9 | Computer Science, Interdisciplinary Applications | 39 | 6% | 0% | 6 |
| 10 | Mathematics, Applied | 28 | 8% | 0% | 8 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | HBEREICH ANGEW INFORMAT | 399157 | 2% | 67% | 2 |
| 2 | ADV MOBILE TELECOMM | 299369 | 1% | 100% | 1 |
| 3 | ECCALS | 299369 | 1% | 100% | 1 |
| 4 | PROJECT TEAM 4 | 299369 | 1% | 100% | 1 |
| 5 | ELECT PAYMENT TEAM | 149683 | 1% | 50% | 1 |
| 6 | GMD FIT | 99788 | 1% | 33% | 1 |
| 7 | GRP GOVT LAW | 74841 | 1% | 25% | 1 |
| 8 | MANAGEMENT SCI ENGINEER | 74841 | 1% | 25% | 1 |
| 9 | CRYPTOG COMP NETWORK SECUR | 70436 | 2% | 12% | 2 |
| 10 | TITR | 59872 | 1% | 20% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | COMPUTERS & SECURITY | 9022 | 6% | 1% | 6 |
| 2 | WIRTSCHAFTSINFORMATIK | 3854 | 3% | 0% | 3 |
| 3 | LECTURE NOTES IN COMPUTER SCIENCE | 3041 | 29% | 0% | 30 |
| 4 | ELECTRONIC COMMERCE RESEARCH AND APPLICATIONS | 2480 | 2% | 0% | 2 |
| 5 | FUTURE GENERATION COMPUTER SYSTEMS-THE INTERNATIONAL JOURNAL OF ESCIENCE | 2268 | 4% | 0% | 4 |
| 6 | AUSTRALIAN JOURNAL OF EDUCATION | 2127 | 2% | 0% | 2 |
| 7 | COMMUNICATIONS OF THE ACM | 1135 | 4% | 0% | 4 |
| 8 | ELECTRONICS AND COMMUNICATIONS IN JAPAN PART III-FUNDAMENTAL ELECTRONIC SCIENCE | 1001 | 2% | 0% | 2 |
| 9 | INTERNATIONAL JOURNAL OF COMPUTER MATHEMATICS | 674 | 3% | 0% | 3 |
| 10 | MINDS AND MACHINES | 609 | 1% | 0% | 1 |
Author Key Words |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | RANTOS, K , MITCHELL, CJ , (2005) MATCHING KEY RECOVERY MECHANISMS TO BUSINESS REQUIREMENTS.COMPUTERS & SECURITY. VOL. 24. ISSUE 3. P. 232-245 | 7 | 100% | 1 |
| 2 | LIN, DR , WANG, CI , ZHANG, ZK , GUAN, DJ , (2010) A DIGITAL SIGNATURE WITH MULTIPLE SUBLIMINAL CHANNELS AND ITS APPLICATIONS.COMPUTERS & MATHEMATICS WITH APPLICATIONS. VOL. 60. ISSUE 2. P. 276 -284 | 9 | 64% | 3 |
| 3 | WU, CK , VARADHARAJAN, V , (1999) BOOLEAN PERMUTATION-BASED KEY ESCROW.COMPUTERS & ELECTRICAL ENGINEERING. VOL. 25. ISSUE 4. P. 291 -304 | 7 | 100% | 1 |
| 4 | KANYAMEE, K , SATHITWIRIYAWONG, C , (2014) HIGH-AVAILABILITY DECENTRALIZED CRYPTOGRAPHIC MULTI-AGENT KEY RECOVERY.INTERNATIONAL ARAB JOURNAL OF INFORMATION TECHNOLOGY. VOL. 11. ISSUE 1. P. 52-58 | 4 | 100% | 1 |
| 5 | WU, CK , VARADHARAJAN, V , (2000) PUBLIC KEY CRYPTOSYSTEMS BASED ON BOOLEAN PERMUTATIONS AND THEIR APPLICATIONS.INTERNATIONAL JOURNAL OF COMPUTER MATHEMATICS. VOL. 74. ISSUE 2. P. 167 -184 | 7 | 78% | 3 |
| 6 | POHL, H , CERNY, D , (1998) UNTERNEHMENSINTERNE SCHLUSSEL-ARCHIVE (KEY RECOVERY CENTER).WIRTSCHAFTSINFORMATIK. VOL. 40. ISSUE 5. P. 443-446 | 5 | 100% | 0 |
| 7 | HOYLE, MP , MITCHELL, CJ , (1998) ON SOLUTIONS TO THE KEY ESCROW PROBLEM.STATE OF THE ART IN APPLIED CRYPTOGRAPHY. VOL. 1528. ISSUE . P. 277-306 | 5 | 100% | 0 |
| 8 | KIM, S , LEE, I , MAMBO, M , PARK, S , (1999) ON THE DIFFICULTY OF KEY RECOVERY SYSTEMS.INFORMATION SECURITY, PROCEEDINGS. VOL. 1729. ISSUE . P. 207 -224 | 9 | 50% | 0 |
| 9 | YEN, SM , (2001) PRACTICAL KEY RECOVERY SCHEMES.INFORMATION SECURITY AND PRIVACY, PROCEEDINGS. VOL. 2119. ISSUE . P. 104 -114 | 5 | 83% | 0 |
| 10 | KIM, JB , SONG, M , HWANG, CS , LEE, S , (2008) FASIREC: A FAST SESSION RECOVERY SCHEME FOR LARGE-SCALE VPNS USING IPSEC.JOURNAL OF INFORMATION SCIENCE AND ENGINEERING. VOL. 24. ISSUE 5. P. 1329 -1346 | 3 | 100% | 0 |
Classes with closest relation at Level 1 |