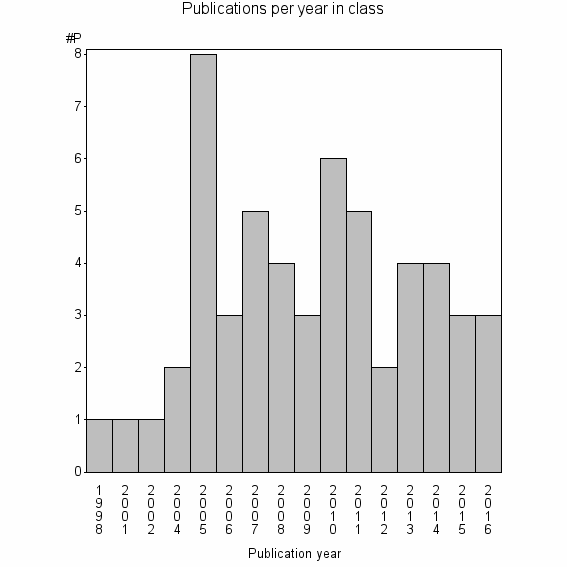
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 37532 | 55 | 17.0 | 42% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
| Cluster id | Level | Cluster label | #P |
|---|---|---|---|
| 9 | 4 | COMPUTER SCIENCE, THEORY & METHODS//COMPUTER SCIENCE, ARTIFICIAL INTELLIGENCE//COMPUTER SCIENCE, INFORMATION SYSTEMS | 1247339 |
| 295 | 3 | CRYPTOGRAPHY//COMPUTER SCIENCE, THEORY & METHODS//IEEE TRANSACTIONS ON INFORMATION THEORY | 41419 |
| 632 | 2 | AUTHENTICATION//CRYPTOGRAPHY//DIGITAL SIGNATURE | 13771 |
| 37532 | 1 | DENIABLE AUTHENTICATION//DENIABLE AUTHENTICATION PROTOCOL//E MAIL PROTOCOL | 55 |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | DENIABLE AUTHENTICATION | authKW | 5727266 | 25% | 74% | 14 |
| 2 | DENIABLE AUTHENTICATION PROTOCOL | authKW | 2220779 | 7% | 100% | 4 |
| 3 | E MAIL PROTOCOL | authKW | 1665585 | 5% | 100% | 3 |
| 4 | ELGAMAL CRYPTOGRAPHY | authKW | 1665585 | 5% | 100% | 3 |
| 5 | IMPERSONATE ATTACKS | authKW | 1110390 | 4% | 100% | 2 |
| 6 | PIM ATTACK | authKW | 1110390 | 4% | 100% | 2 |
| 7 | PERFECT FORWARD SECRECY | authKW | 908492 | 11% | 27% | 6 |
| 8 | AUTHENTICATION CONFIDENTIALITY | authKW | 555195 | 2% | 100% | 1 |
| 9 | AUTO ID S J AN | address | 555195 | 2% | 100% | 1 |
| 10 | CONCURRENT DENIABLE AUTHENTICATION | authKW | 555195 | 2% | 100% | 1 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Information Systems | 1190 | 38% | 0% | 21 |
| 2 | Telecommunications | 741 | 31% | 0% | 17 |
| 3 | Computer Science, Hardware & Architecture | 273 | 13% | 0% | 7 |
| 4 | Computer Science, Software Engineering | 266 | 16% | 0% | 9 |
| 5 | Computer Science, Theory & Methods | 184 | 16% | 0% | 9 |
| 6 | Engineering, Electrical & Electronic | 32 | 16% | 0% | 9 |
| 7 | Mathematics, Applied | 22 | 9% | 0% | 5 |
| 8 | Computer Science, Artificial Intelligence | 19 | 5% | 0% | 3 |
| 9 | Materials Science, Textiles | 14 | 2% | 0% | 1 |
| 10 | Operations Research & Management Science | 11 | 4% | 0% | 2 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | AUTO ID S J AN | 555195 | 2% | 100% | 1 |
| 2 | INFORMAT SECUR GRP ROYAL HOLLOWAY | 555195 | 2% | 100% | 1 |
| 3 | MOBILE NETWORK SECUR TECHNOL | 422999 | 7% | 19% | 4 |
| 4 | INFO SEC INFORMAT COMMUN SYST SECUR | 277596 | 2% | 50% | 1 |
| 5 | COMP NETWORKS INFORMAT SECUR | 72213 | 7% | 3% | 4 |
| 6 | KEIO | 69398 | 2% | 13% | 1 |
| 7 | LASEC | 61687 | 2% | 11% | 1 |
| 8 | INFORMAT SECUR SYST | 30842 | 2% | 6% | 1 |
| 9 | ELECT RUMENTAT TECHNOL | 15003 | 2% | 3% | 1 |
| 10 | CYBER ENGN | 10092 | 2% | 2% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | COMPUTER STANDARDS & INTERFACES | 7150 | 7% | 0% | 4 |
| 2 | FRONTIERS OF COMPUTER SCIENCE IN CHINA | 3512 | 2% | 1% | 1 |
| 3 | SCIENCE IN CHINA SERIES F-INFORMATION SCIENCES | 3119 | 4% | 0% | 2 |
| 4 | IEEE COMMUNICATIONS LETTERS | 3099 | 11% | 0% | 6 |
| 5 | SCIENCE CHINA-INFORMATION SCIENCES | 3008 | 5% | 0% | 3 |
| 6 | ENTOMOLOGICAL RESEARCH | 2237 | 2% | 0% | 1 |
| 7 | IET INFORMATION SECURITY | 1722 | 2% | 0% | 1 |
| 8 | JOURNAL OF AMBIENT INTELLIGENCE AND HUMANIZED COMPUTING | 1655 | 2% | 0% | 1 |
| 9 | SECURITY AND COMMUNICATION NETWORKS | 1601 | 4% | 0% | 2 |
| 10 | JOURNAL OF INDUSTRIAL TEXTILES | 1463 | 2% | 0% | 1 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | DENIABLE AUTHENTICATION | 5727266 | 25% | 74% | 14 | Search DENIABLE+AUTHENTICATION | Search DENIABLE+AUTHENTICATION |
| 2 | DENIABLE AUTHENTICATION PROTOCOL | 2220779 | 7% | 100% | 4 | Search DENIABLE+AUTHENTICATION+PROTOCOL | Search DENIABLE+AUTHENTICATION+PROTOCOL |
| 3 | E MAIL PROTOCOL | 1665585 | 5% | 100% | 3 | Search E+MAIL+PROTOCOL | Search E+MAIL+PROTOCOL |
| 4 | ELGAMAL CRYPTOGRAPHY | 1665585 | 5% | 100% | 3 | Search ELGAMAL+CRYPTOGRAPHY | Search ELGAMAL+CRYPTOGRAPHY |
| 5 | IMPERSONATE ATTACKS | 1110390 | 4% | 100% | 2 | Search IMPERSONATE+ATTACKS | Search IMPERSONATE+ATTACKS |
| 6 | PIM ATTACK | 1110390 | 4% | 100% | 2 | Search PIM+ATTACK | Search PIM+ATTACK |
| 7 | PERFECT FORWARD SECRECY | 908492 | 11% | 27% | 6 | Search PERFECT+FORWARD+SECRECY | Search PERFECT+FORWARD+SECRECY |
| 8 | AUTHENTICATION CONFIDENTIALITY | 555195 | 2% | 100% | 1 | Search AUTHENTICATION+CONFIDENTIALITY | Search AUTHENTICATION+CONFIDENTIALITY |
| 9 | CONCURRENT DENIABLE AUTHENTICATION | 555195 | 2% | 100% | 1 | Search CONCURRENT+DENIABLE+AUTHENTICATION | Search CONCURRENT+DENIABLE+AUTHENTICATION |
| 10 | COPTOLABRUS | 555195 | 2% | 100% | 1 | Search COPTOLABRUS | Search COPTOLABRUS |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | LI, FG , ZHONG, D , TAKAGI, T , (2016) EFFICIENT DENIABLY AUTHENTICATED ENCRYPTION AND ITS APPLICATION TO E-MAIL.IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY. VOL. 11. ISSUE 11. P. 2477 -2486 | 22 | 52% | 0 |
| 2 | YOON, EJ , YOO, KY , YEO, SS , LEE, C , (2010) ROBUST DENIABLE AUTHENTICATION PROTOCOL.WIRELESS PERSONAL COMMUNICATIONS. VOL. 55. ISSUE 1. P. 81-90 | 11 | 92% | 3 |
| 3 | LI, FG , TAKAGI, T , (2013) CRYPTANALYSIS AND IMPROVEMENT OF ROBUST DENIABLE AUTHENTICATION PROTOCOL.WIRELESS PERSONAL COMMUNICATIONS. VOL. 69. ISSUE 4. P. 1391-1398 | 9 | 90% | 1 |
| 4 | YOUN, TY , LEE, C , PARK, YH , (2011) AN EFFICIENT NON-INTERACTIVE DENIABLE AUTHENTICATION SCHEME BASED ON TRAPDOOR COMMITMENT SCHEMES.COMPUTER COMMUNICATIONS. VOL. 34. ISSUE 3. P. 353-357 | 9 | 82% | 1 |
| 5 | LU, RX , LIN, XD , CAO, ZF , QIN, LQ , LIANG, XH , (2008) A SIMPLE DENIABLE AUTHENTICATION PROTOCOL BASED ON THE DIFFIE-HELLMAN ALGORITHM.INTERNATIONAL JOURNAL OF COMPUTER MATHEMATICS. VOL. 85. ISSUE 9. P. 1315-1323 | 8 | 89% | 3 |
| 6 | WANG, B , SONG, ZX , (2009) A NON-INTERACTIVE DENIABLE AUTHENTICATION SCHEME BASED ON DESIGNATED VERIFIER PROOFS.INFORMATION SCIENCES. VOL. 179. ISSUE 6. P. 858-865 | 9 | 75% | 7 |
| 7 | SHAO, J , CAO, ZF , LU, RX , (2006) AN IMPROVED DENIABLE AUTHENTICATION PROTOCOL.NETWORKS. VOL. 48. ISSUE 4. P. 179-181 | 7 | 100% | 6 |
| 8 | TOORANI, M , (2015) CRYPTANALYSIS OF A NEW PROTOCOL OF WIDE USE FOR EMAIL WITH PERFECT FORWARD SECRECY.SECURITY AND COMMUNICATION NETWORKS. VOL. 8. ISSUE 4. P. 694 -701 | 7 | 70% | 0 |
| 9 | LU, RX , CAO, ZF , WANG, SB , BAO, HY , (2007) A NEW ID-BASED DENIABLE AUTHENTICATION PROTOCOL.INFORMATICA. VOL. 18. ISSUE 1. P. 67-78 | 7 | 70% | 2 |
| 10 | HSU, CL , CHUANG, YH , HUNG, MT , (2014) AN EFFICIENT DENIABLE AUTHENTICATION PROTOCOL FROM PAIRINGS TO PROTECT USERS' PRIVACY.CHIANG MAI JOURNAL OF SCIENCE. VOL. 41. ISSUE 5.2. P. 1384 -1391 | 4 | 100% | 0 |
Classes with closest relation at Level 1 |