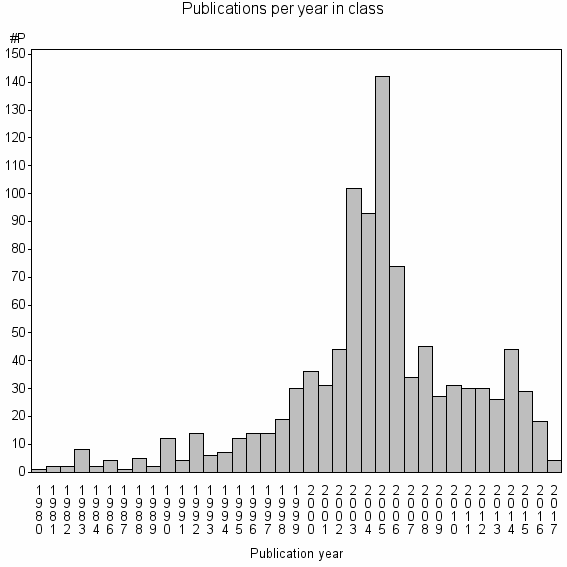
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 11223 | 999 | 25.0 | 29% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
| Cluster id | Level | Cluster label | #P |
|---|---|---|---|
| 9 | 4 | COMPUTER SCIENCE, THEORY & METHODS//COMPUTER SCIENCE, ARTIFICIAL INTELLIGENCE//COMPUTER SCIENCE, INFORMATION SYSTEMS | 1247339 |
| 295 | 3 | CRYPTOGRAPHY//COMPUTER SCIENCE, THEORY & METHODS//IEEE TRANSACTIONS ON INFORMATION THEORY | 41419 |
| 632 | 2 | AUTHENTICATION//CRYPTOGRAPHY//DIGITAL SIGNATURE | 13771 |
| 11223 | 1 | SECURITY PROTOCOLS//FAIR EXCHANGE//CRYPTOGRAPHIC PROTOCOLS | 999 |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | SECURITY PROTOCOLS | authKW | 1223937 | 9% | 46% | 87 |
| 2 | FAIR EXCHANGE | authKW | 573151 | 4% | 51% | 37 |
| 3 | CRYPTOGRAPHIC PROTOCOLS | authKW | 558454 | 6% | 30% | 60 |
| 4 | NON REPUDIATION | authKW | 447207 | 3% | 43% | 34 |
| 5 | SECURITY PROTOCOL ANALYSIS | authKW | 225062 | 1% | 82% | 9 |
| 6 | CERTIFIED E MAIL | authKW | 195609 | 1% | 80% | 8 |
| 7 | DOLEV YAO MODEL | authKW | 187205 | 1% | 88% | 7 |
| 8 | SECURE ELECTRONIC COMMERCE | authKW | 177825 | 1% | 73% | 8 |
| 9 | AUTHENTICATION PROTOCOLS | authKW | 176315 | 2% | 38% | 15 |
| 10 | SPI CALCULUS | authKW | 166403 | 1% | 78% | 7 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Theory & Methods | 42794 | 57% | 0% | 566 |
| 2 | Computer Science, Software Engineering | 18850 | 32% | 0% | 318 |
| 3 | Computer Science, Information Systems | 12793 | 30% | 0% | 295 |
| 4 | Computer Science, Hardware & Architecture | 3963 | 11% | 0% | 114 |
| 5 | Telecommunications | 1893 | 12% | 0% | 120 |
| 6 | Logic | 1466 | 3% | 0% | 27 |
| 7 | Computer Science, Artificial Intelligence | 1057 | 9% | 0% | 90 |
| 8 | Engineering, Electrical & Electronic | 286 | 12% | 0% | 123 |
| 9 | Computer Science, Interdisciplinary Applications | 104 | 3% | 0% | 34 |
| 10 | Mathematics, Applied | 80 | 5% | 0% | 49 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | LSV | 75460 | 3% | 10% | 25 |
| 2 | IST INFORMAT TELEMAT | 66099 | 2% | 14% | 15 |
| 3 | LOG SECUR | 61129 | 0% | 100% | 2 |
| 4 | PROSECCO | 61129 | 0% | 100% | 2 |
| 5 | TEAM LILAC | 61129 | 0% | 100% | 2 |
| 6 | UGBS | 55014 | 0% | 60% | 3 |
| 7 | LOG COMPUTAT | 45844 | 0% | 50% | 3 |
| 8 | IST PLICAZ TELEMAT | 40751 | 0% | 67% | 2 |
| 9 | LORIA INRIA | 40751 | 0% | 67% | 2 |
| 10 | UMR 8643 | 40179 | 1% | 12% | 11 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | LECTURE NOTES IN COMPUTER SCIENCE | 51913 | 39% | 0% | 387 |
| 2 | INTERNATIONAL JOURNAL OF INFORMATION SECURITY | 27233 | 2% | 6% | 16 |
| 3 | JOURNAL OF AUTOMATED REASONING | 11115 | 2% | 2% | 16 |
| 4 | ACM TRANSACTIONS ON INFORMATION AND SYSTEM SECURITY | 10335 | 1% | 4% | 8 |
| 5 | FORMAL ASPECTS OF COMPUTING | 9585 | 1% | 3% | 11 |
| 6 | INTERNATIONAL FEDERATION FOR INFORMATION PROCESSING | 9401 | 0% | 15% | 2 |
| 7 | JOURNAL OF LOGIC AND ALGEBRAIC PROGRAMMING | 7462 | 1% | 3% | 9 |
| 8 | COMPUTERS & SECURITY | 7371 | 2% | 1% | 17 |
| 9 | ELECTRONIC COMMERCE RESEARCH | 6034 | 1% | 3% | 6 |
| 10 | COMPUTER STANDARDS & INTERFACES | 5512 | 2% | 1% | 15 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | SECURITY PROTOCOLS | 1223937 | 9% | 46% | 87 | Search SECURITY+PROTOCOLS | Search SECURITY+PROTOCOLS |
| 2 | FAIR EXCHANGE | 573151 | 4% | 51% | 37 | Search FAIR+EXCHANGE | Search FAIR+EXCHANGE |
| 3 | CRYPTOGRAPHIC PROTOCOLS | 558454 | 6% | 30% | 60 | Search CRYPTOGRAPHIC+PROTOCOLS | Search CRYPTOGRAPHIC+PROTOCOLS |
| 4 | NON REPUDIATION | 447207 | 3% | 43% | 34 | Search NON+REPUDIATION | Search NON+REPUDIATION |
| 5 | SECURITY PROTOCOL ANALYSIS | 225062 | 1% | 82% | 9 | Search SECURITY+PROTOCOL+ANALYSIS | Search SECURITY+PROTOCOL+ANALYSIS |
| 6 | CERTIFIED E MAIL | 195609 | 1% | 80% | 8 | Search CERTIFIED+E+MAIL | Search CERTIFIED+E+MAIL |
| 7 | DOLEV YAO MODEL | 187205 | 1% | 88% | 7 | Search DOLEV+YAO+MODEL | Search DOLEV+YAO+MODEL |
| 8 | SECURE ELECTRONIC COMMERCE | 177825 | 1% | 73% | 8 | Search SECURE+ELECTRONIC+COMMERCE | Search SECURE+ELECTRONIC+COMMERCE |
| 9 | AUTHENTICATION PROTOCOLS | 176315 | 2% | 38% | 15 | Search AUTHENTICATION+PROTOCOLS | Search AUTHENTICATION+PROTOCOLS |
| 10 | SPI CALCULUS | 166403 | 1% | 78% | 7 | Search SPI+CALCULUS | Search SPI+CALCULUS |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | CORTIER, V , KREMER, S , WARINSCHI, B , (2011) A SURVEY OF SYMBOLIC METHODS IN COMPUTATIONAL ANALYSIS OF CRYPTOGRAPHIC SYSTEMS.JOURNAL OF AUTOMATED REASONING. VOL. 46. ISSUE 3-4. P. 225-259 | 32 | 94% | 12 |
| 2 | SATTARZADEH, B , FALLAH, MS , (2015) AUTOMATED TYPE-BASED ANALYSIS OF INJECTIVE AGREEMENT IN THE PRESENCE OF COMPROMISED PRINCIPALS.JOURNAL OF LOGICAL AND ALGEBRAIC METHODS IN PROGRAMMING. VOL. 84. ISSUE 5. P. 576 -610 | 21 | 88% | 0 |
| 3 | AVALLE, M , PIRONTI, A , SISTO, R , (2014) FORMAL VERIFICATION OF SECURITY PROTOCOL IMPLEMENTATIONS: A SURVEY.FORMAL ASPECTS OF COMPUTING. VOL. 26. ISSUE 1. P. 99 -123 | 16 | 73% | 5 |
| 4 | BASIN, D , CALEIRO, C , RAMOS, J , VIGANO, L , (2011) DISTRIBUTED TEMPORAL LOGIC FOR THE ANALYSIS OF SECURITY PROTOCOL MODELS.THEORETICAL COMPUTER SCIENCE. VOL. 412. ISSUE 31. P. 4007 -4043 | 16 | 80% | 1 |
| 5 | AVANESOV, T , CHEVALIER, Y , RUSINOWITCH, M , TURUANI, M , (2017) SATISFIABILITY OF GENERAL INTRUDER CONSTRAINTS WITH AND WITHOUT A SET CONSTRUCTOR.JOURNAL OF SYMBOLIC COMPUTATION. VOL. 80. ISSUE . P. 27 -61 | 11 | 100% | 0 |
| 6 | BAUDET, M , CORTIER, V , KREMER, S , (2009) COMPUTATIONALLY SOUND IMPLEMENTATIONS OF EQUATIONAL THEORIES AGAINST PASSIVE ADVERSARIES.INFORMATION AND COMPUTATION. VOL. 207. ISSUE 4. P. 496 -520 | 14 | 88% | 4 |
| 7 | KAHLER, D , KUSTERS, R , WILKE, T , (2010) DECIDING STRATEGY PROPERTIES OF CONTRACT-SIGNING PROTOCOLS.ACM TRANSACTIONS ON COMPUTATIONAL LOGIC. VOL. 11. ISSUE 3. P. - | 12 | 100% | 0 |
| 8 | CHEVALIER, Y , RUSINOWITCH, M , (2008) HIERARCHICAL COMBINATION OF INTRUDER THEORIES.INFORMATION AND COMPUTATION. VOL. 206. ISSUE 2-4. P. 352 -377 | 14 | 88% | 4 |
| 9 | BACKES, M , CERVESATO, I , JAGGARD, AD , SCEDROV, A , TSAY, JK , (2011) CRYPTOGRAPHICALLY SOUND SECURITY PROOFS FOR BASIC AND PUBLIC-KEY KERBEROS.INTERNATIONAL JOURNAL OF INFORMATION SECURITY. VOL. 10. ISSUE 2. P. 107 -134 | 13 | 87% | 4 |
| 10 | PERMPOONTANALARP, Y , SORNKHOM, P , (2014) ON-THE-FLY TRACE GENERATION APPROACH TO THE SECURITY ANALYSIS OF CRYPTOGRAPHIC PROTOCOLS: COLOURED PETRI NETS-BASED METHOD.FUNDAMENTA INFORMATICAE. VOL. 130. ISSUE 4. P. 423 -466 | 13 | 81% | 0 |
Classes with closest relation at Level 1 |