Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
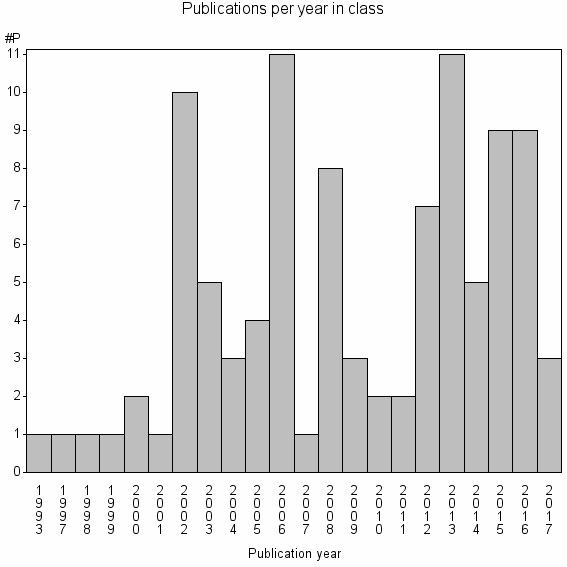
| 35245 | 100 | 24.3 | 19% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | DOMAIN NAME SYSTEM DNS | authKW | 880136 | 7% | 41% | 7 |
| 2 | DOMAIN NAME SYSTEM | authKW | 575469 | 7% | 27% | 7 |
| 3 | MALICIOUS DOMAIN DETECTION | authKW | 407140 | 2% | 67% | 2 |
| 4 | AND COMMAND AND CONTROL | authKW | 305356 | 1% | 100% | 1 |
| 5 | ATTACK RESILIENCY | authKW | 305356 | 1% | 100% | 1 |
| 6 | AUTHORITATIVE DNS RECORDS | authKW | 305356 | 1% | 100% | 1 |
| 7 | CLOUD THREAT S | address | 305356 | 1% | 100% | 1 |
| 8 | CONFIGURATIONS ERRORS | authKW | 305356 | 1% | 100% | 1 |
| 9 | CONNECTION MANAGEMENT PROTOCOL | authKW | 305356 | 1% | 100% | 1 |
| 10 | DAY IN THE LIFE OF THE INTERNET | authKW | 305356 | 1% | 100% | 1 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Information Systems | 3740 | 50% | 0% | 50 |
| 2 | Telecommunications | 2281 | 40% | 0% | 40 |
| 3 | Computer Science, Hardware & Architecture | 1378 | 21% | 0% | 21 |
| 4 | Computer Science, Software Engineering | 404 | 15% | 0% | 15 |
| 5 | Engineering, Electrical & Electronic | 259 | 31% | 0% | 31 |
| 6 | Computer Science, Theory & Methods | 206 | 13% | 0% | 13 |
| 7 | Computer Science, Artificial Intelligence | 195 | 12% | 0% | 12 |
| 8 | International Relations | 81 | 4% | 0% | 4 |
| 9 | Communication | 52 | 3% | 0% | 3 |
| 10 | Computer Science, Cybernetics | 42 | 2% | 0% | 2 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | CLOUD THREAT S | 305356 | 1% | 100% | 1 |
| 2 | ELASTICA | 305356 | 1% | 100% | 1 |
| 3 | HOPKINS INTERNETWORKING HINRG GRP | 305356 | 1% | 100% | 1 |
| 4 | IND DEV BOARD | 305356 | 1% | 100% | 1 |
| 5 | INFORMAT ETH | 305356 | 1% | 100% | 1 |
| 6 | PROGRAM TELECOMMUN | 305356 | 1% | 100% | 1 |
| 7 | SCI TECHNOL 4285 | 305356 | 1% | 100% | 1 |
| 8 | SURFNET BV | 305356 | 1% | 100% | 1 |
| 9 | COMMUN DISTRIBUTED SYST GRP | 152677 | 1% | 50% | 1 |
| 10 | UBIQUITOUS NETWORKED SYST UBINES | 152677 | 1% | 50% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | ACM SIGCOMM COMPUTER COMMUNICATION REVIEW | 30539 | 11% | 1% | 11 |
| 2 | ACM TRANSACTIONS ON INTERNET TECHNOLOGY | 15347 | 3% | 2% | 3 |
| 3 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 5708 | 3% | 1% | 3 |
| 4 | IEEE NETWORK | 2988 | 3% | 0% | 3 |
| 5 | INTERNATIONAL JOURNAL OF CRITICAL INFRASTRUCTURE PROTECTION | 2195 | 1% | 1% | 1 |
| 6 | COMPUTER NETWORKS | 2042 | 5% | 0% | 5 |
| 7 | IEEE SECURITY & PRIVACY | 1929 | 2% | 0% | 2 |
| 8 | INDEX ON CENSORSHIP | 1588 | 1% | 1% | 1 |
| 9 | JOURNAL OF HIGH SPEED NETWORKS | 1452 | 1% | 0% | 1 |
| 10 | SPACE AND CULTURE | 1445 | 1% | 0% | 1 |
Author Key Words |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | WANG, Z , (2012) ANALYSIS OF FLOODING DOS ATTACKS UTILIZING DNS NAME ERROR QUERIES.KSII TRANSACTIONS ON INTERNET AND INFORMATION SYSTEMS. VOL. 6. ISSUE 10. P. 2750 -2763 | 5 | 83% | 1 |
| 2 | WANG, Z , WANG, R , (2013) OPTIMIZING DNS SERVER SELECTION.APPLIED MATHEMATICS & INFORMATION SCIENCES. VOL. 7. ISSUE 6. P. 2233 -2240 | 4 | 100% | 2 |
| 3 | GAO, HY , YEGNESWARAN, V , JIANG, J , CHEN, Y , PORRAS, P , GHOSH, S , DUAN, HX , (2016) REEXAMINING DNS FROM A GLOBAL RECURSIVE RESOLVER PERSPECTIVE.IEEE-ACM TRANSACTIONS ON NETWORKING. VOL. 24. ISSUE 1. P. 43 -57 | 3 | 100% | 1 |
| 4 | KOC, Y , JAMAKOVIC, A , GIJSEN, B , (2012) A GLOBAL REFERENCE MODEL OF THE DOMAIN NAME SYSTEM.INTERNATIONAL JOURNAL OF CRITICAL INFRASTRUCTURE PROTECTION. VOL. 5. ISSUE 3-4. P. 108-117 | 3 | 100% | 2 |
| 5 | SHUE, CA , KALAFUT, AJ , (2013) RESOLVERS REVEALED: CHARACTERIZING DNS RESOLVERS AND THEIR CLIENTS.ACM TRANSACTIONS ON INTERNET TECHNOLOGY. VOL. 12. ISSUE 4. P. - | 4 | 67% | 0 |
| 6 | SHANG, H , WILLS, CE , (2006) PIGGYBACKING RELATED DOMAIN NAMES TO IMPROVE DNS PERFORMANCE.COMPUTER NETWORKS. VOL. 50. ISSUE 11. P. 1733 -1748 | 3 | 100% | 6 |
| 7 | VAN RIJSWIJK-DEIJ, R , JONKER, M , SPEROTTO, A , PRAS, A , (2016) A HIGH-PERFORMANCE, SCALABLE INFRASTRUCTURE FOR LARGE-SCALE ACTIVE DNS MEASUREMENTS.IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS. VOL. 34. ISSUE 6. P. 1877 -1888 | 3 | 75% | 0 |
| 8 | SOOD, AK , ZEADALLY, S , (2016) DRIVE-BY DOWNLOAD ATTACKS A COMPARATIVE STUDY.IT PROFESSIONAL. VOL. 18. ISSUE 5. P. 18 -25 | 2 | 100% | 0 |
| 9 | HMOOD, HS , LI, ZT , ABDULWAHID, HK , ZHANG, Y , (2015) ADAPTIVE CACHING APPROACH TO PREVENT DNS CACHE POISONING ATTACK.COMPUTER JOURNAL. VOL. 58. ISSUE 4. P. 973 -985 | 2 | 100% | 0 |
| 10 | GAO, HY , YEGNESWARAN, V , CHEN, Y , PORRAS, P , GHOSH, S , JIANG, J , DUAN, HX , (2013) AN EMPIRICAL REEXAMINATION OF GLOBAL DNS BEHAVIOR.ACM SIGCOMM COMPUTER COMMUNICATION REVIEW. VOL. 43. ISSUE 4. P. 267-278 | 2 | 100% | 4 |
Classes with closest relation at Level 1 |