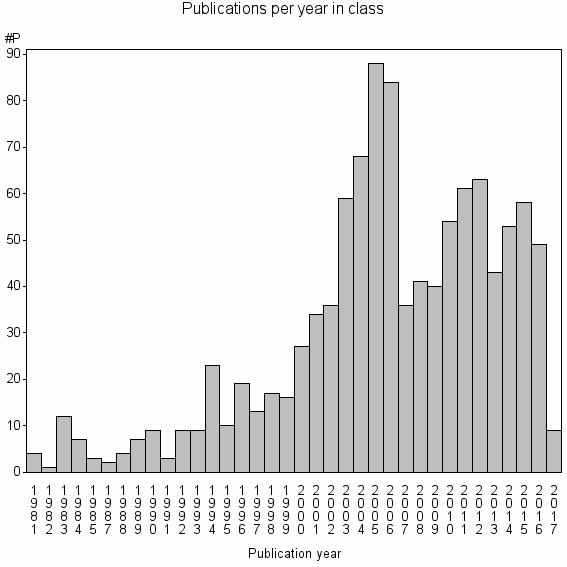
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 10353 | 1071 | 24.6 | 22% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | ACCESS CONTROL | authKW | 1278682 | 20% | 21% | 210 |
| 2 | RBAC | authKW | 1269254 | 6% | 70% | 64 |
| 3 | ROLE BASED ACCESS CONTROL | authKW | 719888 | 5% | 51% | 50 |
| 4 | XACML | authKW | 410028 | 2% | 55% | 26 |
| 5 | ACCESS CONTROL MODEL | authKW | 320724 | 1% | 75% | 15 |
| 6 | ROLE MINING | authKW | 273686 | 1% | 80% | 12 |
| 7 | AUTHORIZATION | authKW | 267865 | 4% | 21% | 44 |
| 8 | CONTROLLED QUERY EVALUATION | authKW | 256586 | 1% | 100% | 9 |
| 9 | SEPARATION OF DUTY | authKW | 215596 | 1% | 69% | 11 |
| 10 | SECURE INTEROPERATION | authKW | 202733 | 1% | 89% | 8 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Information Systems | 41042 | 51% | 0% | 542 |
| 2 | Computer Science, Theory & Methods | 23226 | 41% | 0% | 434 |
| 3 | Computer Science, Software Engineering | 17993 | 30% | 0% | 322 |
| 4 | Computer Science, Hardware & Architecture | 6119 | 14% | 0% | 146 |
| 5 | Computer Science, Artificial Intelligence | 2284 | 13% | 0% | 134 |
| 6 | Telecommunications | 1060 | 9% | 0% | 95 |
| 7 | Computer Science, Interdisciplinary Applications | 289 | 5% | 0% | 54 |
| 8 | Engineering, Electrical & Electronic | 265 | 12% | 0% | 125 |
| 9 | Logic | 140 | 1% | 0% | 9 |
| 10 | Medical Informatics | 44 | 1% | 0% | 10 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | CERIAS | 64769 | 1% | 15% | 15 |
| 2 | NESTOR | 64145 | 0% | 75% | 3 |
| 3 | COMPETENCE IT SECUR | 57019 | 0% | 100% | 2 |
| 4 | COORDINAMENTO PROGETTI INTERSETTORIALI | 57019 | 0% | 100% | 2 |
| 5 | INTERNET TECHNOL PLICAT | 57019 | 0% | 100% | 2 |
| 6 | MULTIMEDIA SERV SECUR CERTIFICAT | 57019 | 0% | 100% | 2 |
| 7 | INFORMAT EC | 57015 | 0% | 50% | 4 |
| 8 | MATHS COMP | 57011 | 1% | 33% | 6 |
| 9 | SECUR ENGN FUTURE COMP | 38011 | 0% | 67% | 2 |
| 10 | ADVANCE NETWORKING | 28510 | 0% | 100% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | ACM TRANSACTIONS ON INFORMATION AND SYSTEM SECURITY | 94234 | 2% | 13% | 25 |
| 2 | COMPUTERS & SECURITY | 57284 | 5% | 4% | 49 |
| 3 | INTERNATIONAL JOURNAL OF INFORMATION SECURITY | 57174 | 2% | 8% | 24 |
| 4 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 23670 | 2% | 4% | 20 |
| 5 | LECTURE NOTES IN COMPUTER SCIENCE | 19688 | 23% | 0% | 248 |
| 6 | IEEE TRANSACTIONS ON KNOWLEDGE AND DATA ENGINEERING | 7393 | 3% | 1% | 28 |
| 7 | COMPUTER STANDARDS & INTERFACES | 5850 | 1% | 1% | 16 |
| 8 | DATA & KNOWLEDGE ENGINEERING | 4523 | 1% | 1% | 14 |
| 9 | INTERNATIONAL JOURNAL OF COOPERATIVE INFORMATION SYSTEMS | 4083 | 1% | 2% | 7 |
| 10 | COMPUTER SYSTEMS SCIENCE AND ENGINEERING | 3787 | 1% | 1% | 10 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | ACCESS CONTROL | 1278682 | 20% | 21% | 210 | Search ACCESS+CONTROL | Search ACCESS+CONTROL |
| 2 | RBAC | 1269254 | 6% | 70% | 64 | Search RBAC | Search RBAC |
| 3 | ROLE BASED ACCESS CONTROL | 719888 | 5% | 51% | 50 | Search ROLE+BASED+ACCESS+CONTROL | Search ROLE+BASED+ACCESS+CONTROL |
| 4 | XACML | 410028 | 2% | 55% | 26 | Search XACML | Search XACML |
| 5 | ACCESS CONTROL MODEL | 320724 | 1% | 75% | 15 | Search ACCESS+CONTROL+MODEL | Search ACCESS+CONTROL+MODEL |
| 6 | ROLE MINING | 273686 | 1% | 80% | 12 | Search ROLE+MINING | Search ROLE+MINING |
| 7 | AUTHORIZATION | 267865 | 4% | 21% | 44 | Search AUTHORIZATION | Search AUTHORIZATION |
| 8 | CONTROLLED QUERY EVALUATION | 256586 | 1% | 100% | 9 | Search CONTROLLED+QUERY+EVALUATION | Search CONTROLLED+QUERY+EVALUATION |
| 9 | SEPARATION OF DUTY | 215596 | 1% | 69% | 11 | Search SEPARATION+OF+DUTY | Search SEPARATION+OF+DUTY |
| 10 | SECURE INTEROPERATION | 202733 | 1% | 89% | 8 | Search SECURE+INTEROPERATION | Search SECURE+INTEROPERATION |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | MITRA, B , SURAL, S , VAIDYA, J , ATLURI, V , (2016) A SURVEY OF ROLE MINING.ACM COMPUTING SURVEYS. VOL. 48. ISSUE 4. P. - | 16 | 80% | 1 |
| 2 | MIRABI, M , IBRAHIM, H , FATHI, L , UDZIR, NI , MAMAT, A , (2015) A DYNAMIC COMPRESSED ACCESSIBILITY MAP FOR SECURE XML QUERYING AND UPDATING.JOURNAL OF INFORMATION SCIENCE AND ENGINEERING. VOL. 31. ISSUE 1. P. 59 -93 | 14 | 93% | 0 |
| 3 | FATIMA, A , GHAZI, Y , SHIBLI, MA , ABASSI, AG , (2016) TOWARDS ATTRIBUTE-CENTRIC ACCESS CONTROL: AN ABAC VERSUS RBAC ARGUMENT.SECURITY AND COMMUNICATION NETWORKS. VOL. 9. ISSUE 16. P. 3152 -3166 | 12 | 92% | 0 |
| 4 | BEN FADHEL, A , BIANCULLI, D , BRIAND, L , (2015) A COMPREHENSIVE MODELING FRAMEWORK FOR ROLE-BASED ACCESS CONTROL POLICIES.JOURNAL OF SYSTEMS AND SOFTWARE. VOL. 107. ISSUE . P. 110 -126 | 12 | 75% | 0 |
| 5 | LU, JF , JOSHI, JBD , JIN, L , LIU, YD , (2015) TOWARDS COMPLEXITY ANALYSIS OF USER AUTHORIZATION QUERY PROBLEM IN RBAC.COMPUTERS & SECURITY. VOL. 48. ISSUE . P. 116 -130 | 9 | 100% | 0 |
| 6 | LUO, B , LEE, D , LEE, WC , LIU, P , (2011) QFILTER: REWRITING INSECURE XML QUERIES TO SECURE ONES USING NON-DETERMINISTIC FINITE AUTOMATA.VLDB JOURNAL. VOL. 20. ISSUE 3. P. 397-415 | 9 | 100% | 4 |
| 7 | MITRA, B , SURAL, S , VAIDYA, J , ATLURI, V , (2016) MINING TEMPORAL ROLES USING MANY-VALUED CONCEPTS.COMPUTERS & SECURITY. VOL. 60. ISSUE . P. 79 -94 | 9 | 90% | 0 |
| 8 | ARKOUDAS, K , CHADHA, R , CHIANG, J , (2014) SOPHISTICATED ACCESS CONTROL VIA SMT AND LOGICAL FRAMEWORKS.ACM TRANSACTIONS ON INFORMATION AND SYSTEM SECURITY. VOL. 16. ISSUE 4. P. - | 10 | 83% | 1 |
| 9 | BISKUP, J , WEIBERT, T , (2008) KEEPING SECRETS IN INCOMPLETE DATABASES.INTERNATIONAL JOURNAL OF INFORMATION SECURITY. VOL. 7. ISSUE 3. P. 199 -217 | 10 | 91% | 6 |
| 10 | GOUGLIDIS, A , MAVRIDIS, I , HU, VC , (2014) SECURITY POLICY VERIFICATION FOR MULTI-DOMAINS IN CLOUD SYSTEMS.INTERNATIONAL JOURNAL OF INFORMATION SECURITY. VOL. 13. ISSUE 2. P. 97 -111 | 9 | 82% | 5 |
Classes with closest relation at Level 1 |