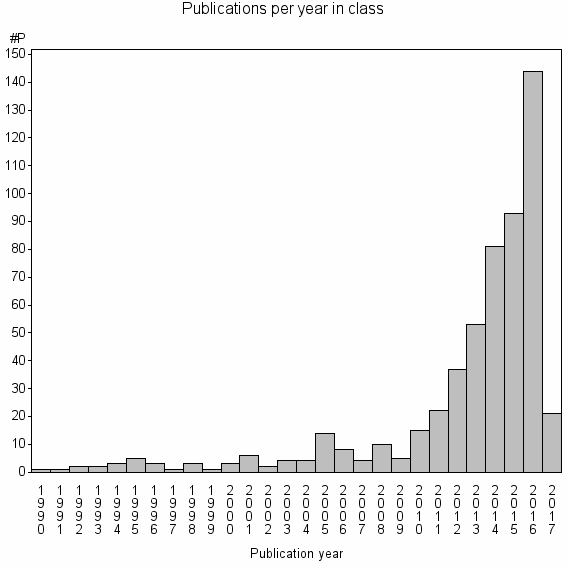
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 18526 | 548 | 31.4 | 36% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
| Cluster id | Level | Cluster label | #P |
|---|---|---|---|
| 9 | 4 | COMPUTER SCIENCE, THEORY & METHODS//COMPUTER SCIENCE, ARTIFICIAL INTELLIGENCE//COMPUTER SCIENCE, INFORMATION SYSTEMS | 1247339 |
| 295 | 3 | CRYPTOGRAPHY//COMPUTER SCIENCE, THEORY & METHODS//IEEE TRANSACTIONS ON INFORMATION THEORY | 41419 |
| 632 | 2 | AUTHENTICATION//CRYPTOGRAPHY//DIGITAL SIGNATURE | 13771 |
| 18526 | 1 | CLOUD STORAGE//PROVABLE DATA POSSESSION//PUBLIC AUDITING | 548 |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | CLOUD STORAGE | authKW | 1037151 | 11% | 32% | 59 |
| 2 | PROVABLE DATA POSSESSION | authKW | 1013093 | 4% | 91% | 20 |
| 3 | PUBLIC AUDITING | authKW | 617208 | 2% | 92% | 12 |
| 4 | DEDUPLICATION | authKW | 573096 | 4% | 43% | 24 |
| 5 | CLOUD SECURITY | authKW | 464949 | 4% | 38% | 22 |
| 6 | PROOF OF OWNERSHIP | authKW | 410301 | 2% | 82% | 9 |
| 7 | CLOUD COMPUTING | authKW | 404115 | 26% | 5% | 145 |
| 8 | SECURE OUTSOURCING | authKW | 324187 | 1% | 73% | 8 |
| 9 | PROOF OF RETRIEVABILITY | authKW | 303363 | 1% | 78% | 7 |
| 10 | STORAGE SECURITY | authKW | 282076 | 2% | 56% | 9 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Information Systems | 19594 | 49% | 0% | 268 |
| 2 | Computer Science, Theory & Methods | 7308 | 32% | 0% | 175 |
| 3 | Computer Science, Software Engineering | 6606 | 26% | 0% | 140 |
| 4 | Computer Science, Hardware & Architecture | 6514 | 20% | 0% | 107 |
| 5 | Telecommunications | 4782 | 25% | 0% | 137 |
| 6 | Engineering, Electrical & Electronic | 997 | 26% | 0% | 145 |
| 7 | Computer Science, Artificial Intelligence | 309 | 7% | 0% | 37 |
| 8 | Computer Science, Interdisciplinary Applications | 152 | 5% | 0% | 28 |
| 9 | Medical Informatics | 12 | 1% | 0% | 4 |
| 10 | Engineering, General | 3 | 1% | 0% | 6 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | SOCIAL SECUR IT MANAGEMENT | 111441 | 0% | 100% | 2 |
| 2 | BEIJING INTERNET SECUR TECHNOL | 99054 | 1% | 44% | 4 |
| 3 | JIANGSU ENGN NETWORK MONITORING | 95822 | 3% | 10% | 17 |
| 4 | HIGH ASSURANCE SOFTWARE HAS | 74292 | 0% | 67% | 2 |
| 5 | IT AUDITING UNIT | 74292 | 0% | 67% | 2 |
| 6 | STATE INTEGRATED SERV NETWORKS ISN | 69421 | 2% | 14% | 9 |
| 7 | BIG DATA TECHNOL SMART CITY | 55720 | 0% | 100% | 1 |
| 8 | BJUT INFORMAT TECHNOL | 55720 | 0% | 100% | 1 |
| 9 | CERIAS EDUC INFORMAT ASSURANCE SECUR | 55720 | 0% | 100% | 1 |
| 10 | CHAIR BUSINESS INFORMAT ESP SOCIAL MEDIA DATA S | 55720 | 0% | 100% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | ACM TRANSACTIONS ON STORAGE | 50637 | 2% | 9% | 10 |
| 2 | JOURNAL OF INTERNET TECHNOLOGY | 40803 | 5% | 3% | 26 |
| 3 | SECURITY AND COMMUNICATION NETWORKS | 17713 | 4% | 2% | 21 |
| 4 | IEEE TRANSACTIONS ON SERVICES COMPUTING | 12696 | 2% | 3% | 9 |
| 5 | IEEE SECURITY & PRIVACY | 10646 | 2% | 2% | 11 |
| 6 | CLUSTER COMPUTING-THE JOURNAL OF NETWORKS SOFTWARE TOOLS AND APPLICATIONS | 9721 | 2% | 2% | 11 |
| 7 | IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS | 8950 | 4% | 1% | 24 |
| 8 | IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY | 8856 | 3% | 1% | 15 |
| 9 | JOURNAL OF AMBIENT INTELLIGENCE AND HUMANIZED COMPUTING | 8136 | 1% | 2% | 7 |
| 10 | CHINA COMMUNICATIONS | 7525 | 3% | 1% | 14 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | CLOUD STORAGE | 1037151 | 11% | 32% | 59 | Search CLOUD+STORAGE | Search CLOUD+STORAGE |
| 2 | PROVABLE DATA POSSESSION | 1013093 | 4% | 91% | 20 | Search PROVABLE+DATA+POSSESSION | Search PROVABLE+DATA+POSSESSION |
| 3 | PUBLIC AUDITING | 617208 | 2% | 92% | 12 | Search PUBLIC+AUDITING | Search PUBLIC+AUDITING |
| 4 | DEDUPLICATION | 573096 | 4% | 43% | 24 | Search DEDUPLICATION | Search DEDUPLICATION |
| 5 | CLOUD SECURITY | 464949 | 4% | 38% | 22 | Search CLOUD+SECURITY | Search CLOUD+SECURITY |
| 6 | PROOF OF OWNERSHIP | 410301 | 2% | 82% | 9 | Search PROOF+OF+OWNERSHIP | Search PROOF+OF+OWNERSHIP |
| 7 | CLOUD COMPUTING | 404115 | 26% | 5% | 145 | Search CLOUD+COMPUTING | Search CLOUD+COMPUTING |
| 8 | SECURE OUTSOURCING | 324187 | 1% | 73% | 8 | Search SECURE+OUTSOURCING | Search SECURE+OUTSOURCING |
| 9 | PROOF OF RETRIEVABILITY | 303363 | 1% | 78% | 7 | Search PROOF+OF+RETRIEVABILITY | Search PROOF+OF+RETRIEVABILITY |
| 10 | STORAGE SECURITY | 282076 | 2% | 56% | 9 | Search STORAGE+SECURITY | Search STORAGE+SECURITY |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | ABO-ALIAN, A , BADR, NL , TOLBA, MF , (2017) INTEGRITY AS A SERVICE FOR REPLICATED DATA ON THE CLOUD.CONCURRENCY AND COMPUTATION-PRACTICE & EXPERIENCE. VOL. 29. ISSUE 4. P. - | 21 | 88% | 0 |
| 2 | SOOKHAK, M , GANI, A , KHAN, MK , BUYYA, R , (2017) DYNAMIC REMOTE DATA AUDITING FOR SECURING BIG DATA STORAGE IN CLOUD COMPUTING.INFORMATION SCIENCES. VOL. 380. ISSUE . P. 101 -116 | 13 | 42% | 4 |
| 3 | GARG, N , BAWA, S , (2016) COMPARATIVE ANALYSIS OF CLOUD DATA INTEGRITY AUDITING PROTOCOLS.JOURNAL OF NETWORK AND COMPUTER APPLICATIONS. VOL. 66. ISSUE . P. 17 -32 | 16 | 94% | 0 |
| 4 | YAN, H , LI, JG , HAN, JG , ZHANG, YC , (2017) A NOVEL EFFICIENT REMOTE DATA POSSESSION CHECKING PROTOCOL IN CLOUD STORAGE.IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY. VOL. 12. ISSUE 1. P. 78 -88 | 16 | 80% | 0 |
| 5 | HE, DB , WANG, HQ , ZHANG, JH , WANG, LN , (2017) INSECURITY OF AN IDENTITY-BASED PUBLIC AUDITING PROTOCOL FOR THE OUTSOURCED DATA IN CLOUD STORAGE.INFORMATION SCIENCES. VOL. 375. ISSUE . P. 48 -53 | 14 | 88% | 0 |
| 6 | ALI, M , KHAN, SU , VASILAKOS, AV , (2015) SECURITY IN CLOUD COMPUTING: OPPORTUNITIES AND CHALLENGES.INFORMATION SCIENCES. VOL. 305. ISSUE . P. 357 -383 | 18 | 39% | 51 |
| 7 | YU, J , REN, K , WANG, C , (2016) ENABLING CLOUD STORAGE AUDITING WITH VERIFIABLE OUTSOURCING OF KEY UPDATES.IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY. VOL. 11. ISSUE 6. P. 1362 -1375 | 14 | 82% | 0 |
| 8 | ZHANG, JH , DONG, QC , (2016) EFFICIENT ID-BASED PUBLIC AUDITING FOR THE OUTSOURCED DATA IN CLOUD STORAGE.INFORMATION SCIENCES. VOL. 343. ISSUE . P. 1 -14 | 13 | 72% | 3 |
| 9 | YU, Y , XUE, L , AU, MH , SUSILO, W , NI, JB , ZHANG, YF , VASILAKOS, AV , SHEN, J , (2016) CLOUD DATA INTEGRITY CHECKING WITH AN IDENTITY-BASED AUDITING MECHANISM FROM RSA.FUTURE GENERATION COMPUTER SYSTEMS-THE INTERNATIONAL JOURNAL OF ESCIENCE. VOL. 62. ISSUE . P. 85 -91 | 9 | 90% | 4 |
| 10 | WANG, HQ , HE, DB , TANG, SH , (2016) IDENTITY-BASED PROXY-ORIENTED DATA UPLOADING AND REMOTE DATA INTEGRITY CHECKING IN PUBLIC CLOUD.IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY. VOL. 11. ISSUE 6. P. 1165 -1176 | 11 | 73% | 4 |
Classes with closest relation at Level 1 |