Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
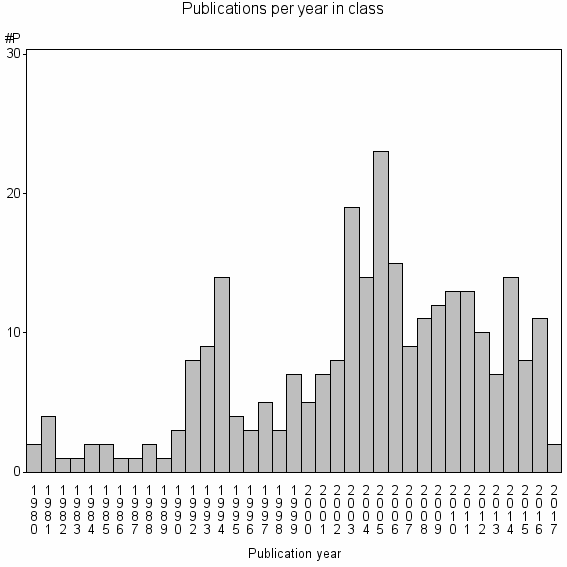
| 25699 | 274 | 18.5 | 42% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
| Cluster id | Level | Cluster label | #P |
|---|---|---|---|
| 9 | 4 | COMPUTER SCIENCE, THEORY & METHODS//COMPUTER SCIENCE, ARTIFICIAL INTELLIGENCE//COMPUTER SCIENCE, INFORMATION SYSTEMS | 1247339 |
| 295 | 3 | CRYPTOGRAPHY//COMPUTER SCIENCE, THEORY & METHODS//IEEE TRANSACTIONS ON INFORMATION THEORY | 41419 |
| 632 | 2 | AUTHENTICATION//CRYPTOGRAPHY//DIGITAL SIGNATURE | 13771 |
| 25699 | 1 | USER HIERARCHY//KEY ASSIGNMENT//CRYPTOGRAPHIC KEY ASSIGNMENT | 274 |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | USER HIERARCHY | authKW | 2690540 | 9% | 93% | 26 |
| 2 | KEY ASSIGNMENT | authKW | 2157524 | 8% | 88% | 22 |
| 3 | CRYPTOGRAPHIC KEY ASSIGNMENT | authKW | 1114426 | 4% | 100% | 10 |
| 4 | ACCESS CONTROL | authKW | 918133 | 33% | 9% | 90 |
| 5 | HIERARCHICAL ACCESS CONTROL | authKW | 509445 | 3% | 57% | 8 |
| 6 | CRYPTOGRAPHIC KEY | authKW | 464343 | 2% | 83% | 5 |
| 7 | HIERARCHICAL KEY ASSIGNMENT | authKW | 445770 | 1% | 100% | 4 |
| 8 | KEY MANAGEMENT | authKW | 410054 | 14% | 10% | 37 |
| 9 | AGENT AUTHENTICATION | authKW | 334328 | 1% | 100% | 3 |
| 10 | EFFICIENT KEY DERIVATION | authKW | 334328 | 1% | 100% | 3 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Information Systems | 7439 | 43% | 0% | 117 |
| 2 | Computer Science, Software Engineering | 1797 | 19% | 0% | 52 |
| 3 | Computer Science, Theory & Methods | 1681 | 22% | 0% | 60 |
| 4 | Computer Science, Hardware & Architecture | 1140 | 12% | 0% | 32 |
| 5 | Telecommunications | 911 | 16% | 0% | 43 |
| 6 | Computer Science, Artificial Intelligence | 539 | 12% | 0% | 33 |
| 7 | Mathematics, Applied | 302 | 14% | 0% | 39 |
| 8 | Medical Informatics | 140 | 3% | 0% | 8 |
| 9 | Engineering, Electrical & Electronic | 122 | 15% | 0% | 40 |
| 10 | Health Care Sciences & Services | 37 | 3% | 0% | 8 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | ELEC ENG INFO SCI | 111443 | 0% | 100% | 1 |
| 2 | MULTIMEDIA INTERACT EXPERIENCES GRP | 111443 | 0% | 100% | 1 |
| 3 | RD SYST DEV | 111443 | 0% | 100% | 1 |
| 4 | AUTHENTICAT COMP SECUR | 55720 | 0% | 50% | 1 |
| 5 | UAB EDUC THER EUT MUSCULOSKELETAL DI | 55720 | 0% | 50% | 1 |
| 6 | MIDS GERIATR EDUC CLIN | 37146 | 0% | 33% | 1 |
| 7 | TAIWAN INFORMAT SECUR | 29715 | 1% | 13% | 2 |
| 8 | INFORMAT MANAGEMENT | 28154 | 18% | 1% | 49 |
| 9 | DIPARTIMENTO INFORMAT PLICAZ | 26798 | 3% | 3% | 8 |
| 10 | SECUR THEORY ALGORITHM | 26606 | 1% | 6% | 4 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | COMPUTERS & SECURITY | 49371 | 8% | 2% | 23 |
| 2 | IEE PROCEEDINGS-COMPUTERS AND DIGITAL TECHNIQUES | 5879 | 2% | 1% | 6 |
| 3 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 5782 | 2% | 1% | 5 |
| 4 | ACM TRANSACTIONS ON INFORMATION AND SYSTEM SECURITY | 5301 | 1% | 2% | 3 |
| 5 | SECURITY AND COMMUNICATION NETWORKS | 5138 | 3% | 1% | 8 |
| 6 | COMPUTER STANDARDS & INTERFACES | 4386 | 3% | 1% | 7 |
| 7 | INTERNATIONAL JOURNAL OF INNOVATIVE COMPUTING INFORMATION AND CONTROL | 4332 | 4% | 0% | 10 |
| 8 | JOURNAL OF MEDICAL SYSTEMS | 3236 | 3% | 0% | 7 |
| 9 | INFORMATION SCIENCES | 2853 | 5% | 0% | 14 |
| 10 | INFORMATION PROCESSING LETTERS | 2514 | 4% | 0% | 12 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | USER HIERARCHY | 2690540 | 9% | 93% | 26 | Search USER+HIERARCHY | Search USER+HIERARCHY |
| 2 | KEY ASSIGNMENT | 2157524 | 8% | 88% | 22 | Search KEY+ASSIGNMENT | Search KEY+ASSIGNMENT |
| 3 | CRYPTOGRAPHIC KEY ASSIGNMENT | 1114426 | 4% | 100% | 10 | Search CRYPTOGRAPHIC+KEY+ASSIGNMENT | Search CRYPTOGRAPHIC+KEY+ASSIGNMENT |
| 4 | ACCESS CONTROL | 918133 | 33% | 9% | 90 | Search ACCESS+CONTROL | Search ACCESS+CONTROL |
| 5 | HIERARCHICAL ACCESS CONTROL | 509445 | 3% | 57% | 8 | Search HIERARCHICAL+ACCESS+CONTROL | Search HIERARCHICAL+ACCESS+CONTROL |
| 6 | CRYPTOGRAPHIC KEY | 464343 | 2% | 83% | 5 | Search CRYPTOGRAPHIC+KEY | Search CRYPTOGRAPHIC+KEY |
| 7 | HIERARCHICAL KEY ASSIGNMENT | 445770 | 1% | 100% | 4 | Search HIERARCHICAL+KEY+ASSIGNMENT | Search HIERARCHICAL+KEY+ASSIGNMENT |
| 8 | KEY MANAGEMENT | 410054 | 14% | 10% | 37 | Search KEY+MANAGEMENT | Search KEY+MANAGEMENT |
| 9 | AGENT AUTHENTICATION | 334328 | 1% | 100% | 3 | Search AGENT+AUTHENTICATION | Search AGENT+AUTHENTICATION |
| 10 | EFFICIENT KEY DERIVATION | 334328 | 1% | 100% | 3 | Search EFFICIENT+KEY+DERIVATION | Search EFFICIENT+KEY+DERIVATION |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | CASTIGLIONE, A , DE SANTIS, A , MASUCCI, B , (2016) KEY INDISTINGUISHABILITY VERSUS STRONG KEY INDISTINGUISHABILITY FOR HIERARCHICAL KEY ASSIGNMENT SCHEMES.IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING. VOL. 13. ISSUE 4. P. 451 -460 | 26 | 93% | 2 |
| 2 | CASTIGLIONE, A , DE SANTIS, A , MASUCCI, B , PALMIERI, F , HUANG, XY , CASTIGLIONE, A , (2017) SUPPORTING DYNAMIC UPDATES IN STORAGE CLOUDS WITH THE AKL-TAYLOR SCHEME.INFORMATION SCIENCES. VOL. 387. ISSUE . P. 56 -74 | 27 | 87% | 0 |
| 3 | CASTIGLIONE, A , DE SANTIS, A , MASUCCI, B , PALMIERI, F , CASTIGLIONE, A , HUANG, XY , (2016) CRYPTOGRAPHIC HIERARCHICAL ACCESS CONTROL FOR DYNAMIC STRUCTURES.IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY. VOL. 11. ISSUE 10. P. 2349 -2364 | 24 | 77% | 2 |
| 4 | CAFARO, M , CIVINO, R , MASUCCI, B , (2015) ON THE EQUIVALENCE OF TWO SECURITY NOTIONS FOR HIERARCHICAL KEY ASSIGNMENT SCHEMES IN THE UNCONDITIONAL SETTING.IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING. VOL. 12. ISSUE 4. P. 485 -490 | 21 | 100% | 0 |
| 5 | LO, JW , HWANG, MS , LIU, CH , (2013) A SIMPLE KEY ASSIGNMENT FOR ACCESS CONTROL BASED ON POLYNOMIAL.ARABIAN JOURNAL FOR SCIENCE AND ENGINEERING. VOL. 38. ISSUE 6. P. 1397-1403 | 15 | 100% | 0 |
| 6 | ODELU, V , DAS, AK , GOSWAMI, A , (2014) A SECURE EFFECTIVE KEY MANAGEMENT SCHEME FOR DYNAMIC ACCESS CONTROL IN A LARGE LEAF CLASS HIERARCHY.INFORMATION SCIENCES. VOL. 269. ISSUE . P. 270-285 | 14 | 88% | 6 |
| 7 | TANG, SH , LI, XY , HUANG, XY , XIANG, Y , XU, LL , (2016) ACHIEVING SIMPLE, SECURE AND EFFICIENT HIERARCHICAL ACCESS CONTROL IN CLOUD COMPUTING.IEEE TRANSACTIONS ON COMPUTERS. VOL. 65. ISSUE 7. P. 2325 -2331 | 16 | 70% | 1 |
| 8 | DE SANTIS, A , FERRARA, AL , MASUCCI, B , (2006) UNCONDITIONALLY SECURE KEY ASSIGNMENT SCHEMES.DISCRETE APPLIED MATHEMATICS. VOL. 154. ISSUE 2. P. 234-252 | 14 | 100% | 12 |
| 9 | ATENIESE, G , DE SANTIS, A , FERRARA, AL , MASUCCI, B , (2012) PROVABLY-SECURE TIME-BOUND HIERARCHICAL KEY ASSIGNMENT SCHEMES.JOURNAL OF CRYPTOLOGY. VOL. 25. ISSUE 2. P. 243 -270 | 17 | 68% | 13 |
| 10 | YEH, JH , (2009) ENFORCING NON-HIERARCHICAL ACCESS POLICIES BY HIERARCHICAL KEY ASSIGNMENT SCHEMES.INFORMATION PROCESSING LETTERS. VOL. 110. ISSUE 2. P. 46-49 | 13 | 100% | 0 |
Classes with closest relation at Level 1 |