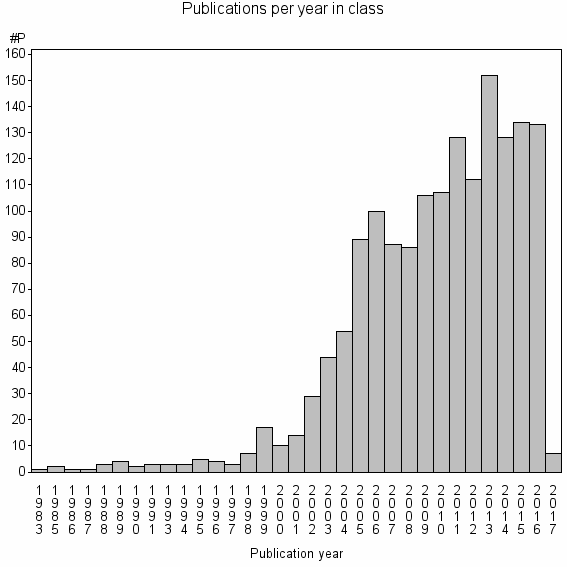
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 5759 | 1579 | 25.8 | 34% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
| Cluster id | Level | Cluster label | #P |
|---|---|---|---|
| 9 | 4 | COMPUTER SCIENCE, THEORY & METHODS//COMPUTER SCIENCE, ARTIFICIAL INTELLIGENCE//COMPUTER SCIENCE, INFORMATION SYSTEMS | 1247339 |
| 295 | 3 | CRYPTOGRAPHY//COMPUTER SCIENCE, THEORY & METHODS//IEEE TRANSACTIONS ON INFORMATION THEORY | 41419 |
| 632 | 2 | AUTHENTICATION//CRYPTOGRAPHY//DIGITAL SIGNATURE | 13771 |
| 5759 | 1 | KEY MANAGEMENT//GROUP KEY MANAGEMENT//KEY PREDISTRIBUTION | 1579 |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | KEY MANAGEMENT | authKW | 1297457 | 10% | 42% | 158 |
| 2 | GROUP KEY MANAGEMENT | authKW | 1045787 | 4% | 81% | 67 |
| 3 | KEY PREDISTRIBUTION | authKW | 934415 | 4% | 79% | 61 |
| 4 | BROADCAST ENCRYPTION | authKW | 461366 | 3% | 47% | 51 |
| 5 | SECURE GROUP COMMUNICATION | authKW | 439629 | 2% | 63% | 36 |
| 6 | SECURE MULTICAST | authKW | 421098 | 2% | 78% | 28 |
| 7 | KEY DISTRIBUTION | authKW | 338038 | 3% | 32% | 55 |
| 8 | WIRELESS SENSOR NETWORKS | authKW | 328588 | 22% | 5% | 344 |
| 9 | BROADCAST AUTHENTICATION | authKW | 309959 | 1% | 70% | 23 |
| 10 | SECURE DATA AGGREGATION | authKW | 294118 | 1% | 89% | 17 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Telecommunications | 64715 | 53% | 0% | 843 |
| 2 | Computer Science, Information Systems | 56425 | 49% | 0% | 772 |
| 3 | Computer Science, Hardware & Architecture | 12650 | 16% | 0% | 254 |
| 4 | Computer Science, Theory & Methods | 11333 | 24% | 0% | 373 |
| 5 | Engineering, Electrical & Electronic | 4328 | 32% | 0% | 502 |
| 6 | Computer Science, Software Engineering | 3230 | 11% | 0% | 171 |
| 7 | Instruments & Instrumentation | 343 | 5% | 0% | 86 |
| 8 | Computer Science, Artificial Intelligence | 183 | 3% | 0% | 54 |
| 9 | Computer Science, Interdisciplinary Applications | 167 | 3% | 0% | 54 |
| 10 | Electrochemistry | 141 | 3% | 0% | 50 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | COMP NETWORKING OURCES | 58010 | 0% | 100% | 3 |
| 2 | BEIJING ENGN MASS LANGUAGE INFORMAT PROC | 44195 | 0% | 57% | 4 |
| 3 | MANAGEMENT SCI ENGINEER | 43506 | 0% | 75% | 3 |
| 4 | SECURE INFORMAT SYST | 40323 | 1% | 16% | 13 |
| 5 | ADV KREONET SERV | 38673 | 0% | 100% | 2 |
| 6 | BACKBONE NETWORK TEAM | 38673 | 0% | 100% | 2 |
| 7 | UNESCO CHAIR DATA PRIVACY | 31985 | 1% | 14% | 12 |
| 8 | PENINSULA COMP INFORMAT TECHNOL | 30934 | 0% | 40% | 4 |
| 9 | BEIJING MUNICIPAL COMMISS EDUC | 23002 | 1% | 12% | 10 |
| 10 | COMP NETWORKS INFORMAT SECUR | 22616 | 1% | 10% | 12 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | SECURITY AND COMMUNICATION NETWORKS | 74316 | 5% | 5% | 73 |
| 2 | INTERNATIONAL JOURNAL OF DISTRIBUTED SENSOR NETWORKS | 59358 | 6% | 3% | 90 |
| 3 | AD HOC NETWORKS | 37760 | 3% | 4% | 50 |
| 4 | ACM TRANSACTIONS ON SENSOR NETWORKS | 31556 | 2% | 6% | 27 |
| 5 | COMPUTER COMMUNICATIONS | 12656 | 3% | 1% | 54 |
| 6 | AD HOC & SENSOR WIRELESS NETWORKS | 10754 | 1% | 3% | 16 |
| 7 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 10261 | 1% | 3% | 16 |
| 8 | IET INFORMATION SECURITY | 10124 | 1% | 4% | 13 |
| 9 | JOURNAL OF SENSORS | 8613 | 1% | 2% | 19 |
| 10 | LECTURE NOTES IN COMPUTER SCIENCE | 7413 | 12% | 0% | 187 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | KEY MANAGEMENT | 1297457 | 10% | 42% | 158 | Search KEY+MANAGEMENT | Search KEY+MANAGEMENT |
| 2 | GROUP KEY MANAGEMENT | 1045787 | 4% | 81% | 67 | Search GROUP+KEY+MANAGEMENT | Search GROUP+KEY+MANAGEMENT |
| 3 | KEY PREDISTRIBUTION | 934415 | 4% | 79% | 61 | Search KEY+PREDISTRIBUTION | Search KEY+PREDISTRIBUTION |
| 4 | BROADCAST ENCRYPTION | 461366 | 3% | 47% | 51 | Search BROADCAST+ENCRYPTION | Search BROADCAST+ENCRYPTION |
| 5 | SECURE GROUP COMMUNICATION | 439629 | 2% | 63% | 36 | Search SECURE+GROUP+COMMUNICATION | Search SECURE+GROUP+COMMUNICATION |
| 6 | SECURE MULTICAST | 421098 | 2% | 78% | 28 | Search SECURE+MULTICAST | Search SECURE+MULTICAST |
| 7 | KEY DISTRIBUTION | 338038 | 3% | 32% | 55 | Search KEY+DISTRIBUTION | Search KEY+DISTRIBUTION |
| 8 | WIRELESS SENSOR NETWORKS | 328588 | 22% | 5% | 344 | Search WIRELESS+SENSOR+NETWORKS | Search WIRELESS+SENSOR+NETWORKS |
| 9 | BROADCAST AUTHENTICATION | 309959 | 1% | 70% | 23 | Search BROADCAST+AUTHENTICATION | Search BROADCAST+AUTHENTICATION |
| 10 | SECURE DATA AGGREGATION | 294118 | 1% | 89% | 17 | Search SECURE+DATA+AGGREGATION | Search SECURE+DATA+AGGREGATION |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | NARANJO, JAM , CASADO, LG , (2013) AN UPDATED VIEW ON CENTRALIZED SECURE GROUP COMMUNICATIONS.LOGIC JOURNAL OF THE IGPL. VOL. 21. ISSUE 4. P. 659-670 | 21 | 95% | 0 |
| 2 | CHEN, YR , TZENG, WG , (2017) GROUP KEY MANAGEMENT WITH EFFICIENT REKEY MECHANISM: A SEMI-STATEFUL APPROACH FOR OUT-OF-SYNCHRONIZED MEMBERS.COMPUTER COMMUNICATIONS. VOL. 98. ISSUE . P. 31 -42 | 23 | 79% | 0 |
| 3 | CHEIKHROUHOU, O , (2016) SECURE GROUP COMMUNICATION IN WIRELESS SENSOR NETWORKS: A SURVEY.JOURNAL OF NETWORK AND COMPUTER APPLICATIONS. VOL. 61. ISSUE . P. 115 -132 | 19 | 79% | 2 |
| 4 | DAGHIGHI, B , KIAH, MLM , SHAMSHIRBAND, S , IQBAL, S , ASGHARI, P , (2015) KEY MANAGEMENT PARADIGM FOR MOBILE SECURE GROUP COMMUNICATIONS: ISSUES, SOLUTIONS, AND CHALLENGES.COMPUTER COMMUNICATIONS. VOL. 72. ISSUE . P. 1 -16 | 27 | 63% | 2 |
| 5 | PARMAR, K , JINWALA, DC , (2016) CONCEALED DATA AGGREGATION IN WIRELESS SENSOR NETWORKS: A COMPREHENSIVE SURVEY.COMPUTER NETWORKS. VOL. 103. ISSUE . P. 207 -227 | 30 | 54% | 0 |
| 6 | DAGHIGHI, B , KIAH, LM , SHAMSHIRBAND, S , REHMAN, MHU , (2015) TOWARD SECURE GROUP COMMUNICATION IN WIRELESS MOBILE ENVIRONMENTS: ISSUES, SOLUTIONS, AND CHALLENGES.JOURNAL OF NETWORK AND COMPUTER APPLICATIONS. VOL. 50. ISSUE . P. 1 -14 | 26 | 59% | 3 |
| 7 | GANDINO, F , FERRERO, R , REBAUDENGO, M , (2017) A KEY DISTRIBUTION SCHEME FOR MOBILE WIRELESS SENSOR NETWORKS: Q-S-COMPOSITE.IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY. VOL. 12. ISSUE 1. P. 34 -47 | 19 | 79% | 0 |
| 8 | PATERSON, MB , STINSON, DR , (2014) A UNIFIED APPROACH TO COMBINATORIAL KEY PREDISTRIBUTION SCHEMES FOR SENSOR NETWORKS.DESIGNS CODES AND CRYPTOGRAPHY. VOL. 71. ISSUE 3. P. 433-457 | 15 | 100% | 5 |
| 9 | TANG, SH , XU, LL , LIU, N , HUANG, XY , DING, JT , YANG, ZM , (2014) PROVABLY SECURE GROUP KEY MANAGEMENT APPROACH BASED UPON HYPER-SPHERE.IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS. VOL. 25. ISSUE 12. P. 3253 -3263 | 19 | 79% | 1 |
| 10 | CONTI, M , WILLEMSEN, J , CRISPO, B , (2013) PROVIDING SOURCE LOCATION PRIVACY IN WIRELESS SENSOR NETWORKS: A SURVEY.IEEE COMMUNICATIONS SURVEYS AND TUTORIALS. VOL. 15. ISSUE 3. P. 1238 -1280 | 26 | 51% | 23 |
Classes with closest relation at Level 1 |