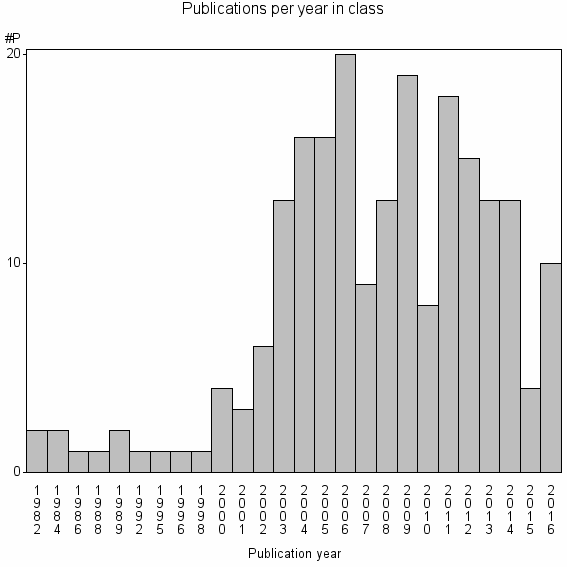
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 28189 | 212 | 26.1 | 21% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | TRUST NEGOTIATION | authKW | 1843641 | 8% | 80% | 16 |
| 2 | AUTOMATED TRUST NEGOTIATION | authKW | 1024247 | 4% | 89% | 8 |
| 3 | SOFTWARE TRUSTWORTHINESS | authKW | 600144 | 2% | 83% | 5 |
| 4 | DISTRIBUTED PROVING | authKW | 288070 | 1% | 100% | 2 |
| 5 | TRUST NEGOTIATIONS | authKW | 288070 | 1% | 100% | 2 |
| 6 | TRUSTED SOFTWARE | authKW | 288070 | 1% | 100% | 2 |
| 7 | TRUSTWORTHINESS ATTRIBUTES | authKW | 288070 | 1% | 100% | 2 |
| 8 | DOMAIN SOFTWARE | authKW | 192045 | 1% | 67% | 2 |
| 9 | ACCESS CONTROL THROUGH CURRENCY | authKW | 144035 | 0% | 100% | 1 |
| 10 | ACCOUNTING AUDIT | authKW | 144035 | 0% | 100% | 1 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Information Systems | 5186 | 41% | 0% | 86 |
| 2 | Computer Science, Theory & Methods | 2853 | 32% | 0% | 68 |
| 3 | Computer Science, Software Engineering | 1997 | 23% | 0% | 48 |
| 4 | Telecommunications | 1996 | 26% | 0% | 55 |
| 5 | Computer Science, Hardware & Architecture | 1688 | 16% | 0% | 34 |
| 6 | COMPUTER APPLICATIONS & CYBERNETICS | 217 | 1% | 0% | 2 |
| 7 | Engineering, Electrical & Electronic | 209 | 20% | 0% | 43 |
| 8 | Computer Science, Artificial Intelligence | 174 | 8% | 0% | 17 |
| 9 | Medical Informatics | 42 | 2% | 0% | 4 |
| 10 | Information Science & Library Science | 38 | 2% | 0% | 5 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | AGCY IND CANADA | 144035 | 0% | 100% | 1 |
| 2 | AUTOMAT COMMAND | 144035 | 0% | 100% | 1 |
| 3 | CERIAS COMP SCI | 144035 | 0% | 100% | 1 |
| 4 | DBSEC | 144035 | 0% | 100% | 1 |
| 5 | DIPARTIMENTO SCI CULTURA POLIT INFORAZ | 144035 | 0% | 100% | 1 |
| 6 | ERICSSON TECHNOL INNOVAT UNIT | 144035 | 0% | 100% | 1 |
| 7 | IT LAW | 144035 | 0% | 100% | 1 |
| 8 | LAAS CNRS 7 | 144035 | 0% | 100% | 1 |
| 9 | PROGRAM NETWORK SECUR MANAGEMENT | 144035 | 0% | 100% | 1 |
| 10 | SECUR SECRETARIAL SERV | 144035 | 0% | 100% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | ACM TRANSACTIONS ON INFORMATION AND SYSTEM SECURITY | 12186 | 2% | 2% | 4 |
| 2 | COMPUTER STANDARDS & INTERFACES | 7412 | 4% | 1% | 8 |
| 3 | INTERNATIONAL JOURNAL OF INFORMATION SECURITY | 4511 | 1% | 1% | 3 |
| 4 | FRONTIERS OF COMPUTER SCIENCE | 3479 | 1% | 1% | 3 |
| 5 | IEEE COMMUNICATIONS MAGAZINE | 3247 | 5% | 0% | 10 |
| 6 | PEER-TO-PEER NETWORKING AND APPLICATIONS | 3243 | 1% | 1% | 3 |
| 7 | INTERNATIONAL JOURNAL OF WEB SERVICES RESEARCH | 2981 | 1% | 1% | 2 |
| 8 | CHINESE JOURNAL OF ELECTRONICS | 2796 | 3% | 0% | 7 |
| 9 | DATA PROCESSING | 2716 | 0% | 2% | 1 |
| 10 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 2689 | 1% | 1% | 3 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | TRUST NEGOTIATION | 1843641 | 8% | 80% | 16 | Search TRUST+NEGOTIATION | Search TRUST+NEGOTIATION |
| 2 | AUTOMATED TRUST NEGOTIATION | 1024247 | 4% | 89% | 8 | Search AUTOMATED+TRUST+NEGOTIATION | Search AUTOMATED+TRUST+NEGOTIATION |
| 3 | SOFTWARE TRUSTWORTHINESS | 600144 | 2% | 83% | 5 | Search SOFTWARE+TRUSTWORTHINESS | Search SOFTWARE+TRUSTWORTHINESS |
| 4 | DISTRIBUTED PROVING | 288070 | 1% | 100% | 2 | Search DISTRIBUTED+PROVING | Search DISTRIBUTED+PROVING |
| 5 | TRUST NEGOTIATIONS | 288070 | 1% | 100% | 2 | Search TRUST+NEGOTIATIONS | Search TRUST+NEGOTIATIONS |
| 6 | TRUSTED SOFTWARE | 288070 | 1% | 100% | 2 | Search TRUSTED+SOFTWARE | Search TRUSTED+SOFTWARE |
| 7 | TRUSTWORTHINESS ATTRIBUTES | 288070 | 1% | 100% | 2 | Search TRUSTWORTHINESS+ATTRIBUTES | Search TRUSTWORTHINESS+ATTRIBUTES |
| 8 | DOMAIN SOFTWARE | 192045 | 1% | 67% | 2 | Search DOMAIN+SOFTWARE | Search DOMAIN+SOFTWARE |
| 9 | ACCESS CONTROL THROUGH CURRENCY | 144035 | 0% | 100% | 1 | Search ACCESS+CONTROL+THROUGH+CURRENCY | Search ACCESS+CONTROL+THROUGH+CURRENCY |
| 10 | ACCOUNTING AUDIT | 144035 | 0% | 100% | 1 | Search ACCOUNTING+AUDIT | Search ACCOUNTING+AUDIT |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | MANA, A , KOSHUTANSKI, H , PEREZ, EJ , (2012) A TRUST NEGOTIATION BASED SECURITY FRAMEWORK FOR SERVICE PROVISIONING IN LOAD-BALANCING CLUSTERS.COMPUTERS & SECURITY. VOL. 31. ISSUE 1. P. 4 -25 | 8 | 89% | 2 |
| 2 | KOSHUTANSKI, H , LAZOUSKI, A , MARTINELLI, F , MORI, P , (2009) ENHANCING GRID SECURITY BY FINE-GRAINED BEHAVIORAL CONTROL AND NEGOTIATION-BASED AUTHORIZATION.INTERNATIONAL JOURNAL OF INFORMATION SECURITY. VOL. 8. ISSUE 4. P. 291 -314 | 10 | 56% | 3 |
| 3 | KOSHUTANSKI, H , MANA, A , (2010) INTEROPERABLE SEMANTIC ACCESS CONTROL FOR HIGHLY DYNAMIC COALITIONS.SECURITY AND COMMUNICATION NETWORKS. VOL. 3. ISSUE 6. P. 565 -594 | 10 | 53% | 4 |
| 4 | LIU, XX , TANG, SH , HUANG, Q , YU, ZW , (2013) AN ONTOLOGY-BASED APPROACH TO AUTOMATED TRUST NEGOTIATION.COMPUTER STANDARDS & INTERFACES. VOL. 36. ISSUE 1. P. 219-230 | 6 | 67% | 2 |
| 5 | KAPITSAKI, GM , (2013) CONSUMER PRIVACY ENFORCEMENT IN CONTEXT-AWARE WEB SERVICES.INTERNATIONAL JOURNAL OF WEB SERVICES RESEARCH. VOL. 10. ISSUE 3. P. 24-41 | 4 | 100% | 0 |
| 6 | SQUICCIARINI, AC , PACI, F , BERTINO, E , (2011) TRUST ESTABLISHMENT IN THE FORMATION OF VIRTUAL ORGANIZATIONS.COMPUTER STANDARDS & INTERFACES. VOL. 33. ISSUE 1. P. 13-23 | 4 | 100% | 6 |
| 7 | YU, DG , CHEN, N , (2014) AN AUTOMATED TRUST NEGOTIATION MODEL BASED ON IMPROVED COLOURED TIMED PETRI NET.INTERNATIONAL JOURNAL OF SENSOR NETWORKS. VOL. 16. ISSUE 2. P. 61 -69 | 4 | 80% | 0 |
| 8 | LIU, BL , GE, F , XIAO, F , (2010) A PEER-TO-PEER FRAMEWORK FOR ACCELERATING TRUST ESTABLISHMENT IN AUTOMATED TRUST NEGOTIATION.JOURNAL OF INTERNET TECHNOLOGY. VOL. 11. ISSUE 5. P. 643-650 | 4 | 80% | 2 |
| 9 | LIU, XX , TANG, SH , CHEN, SQ , (2016) A DESCRIPTION LOGIC-BASED POLICY COMPLIANCE CHECKER FOR TRUST NEGOTIATION.PEER-TO-PEER NETWORKING AND APPLICATIONS. VOL. 9. ISSUE 2. P. 372 -383 | 4 | 67% | 0 |
| 10 | MOWBRAY, M , PEARSON, S , SHEN, Y , (2012) ENHANCING PRIVACY IN CLOUD COMPUTING VIA POLICY-BASED OBFUSCATION.JOURNAL OF SUPERCOMPUTING. VOL. 61. ISSUE 2. P. 267 -291 | 5 | 56% | 5 |
Classes with closest relation at Level 1 |