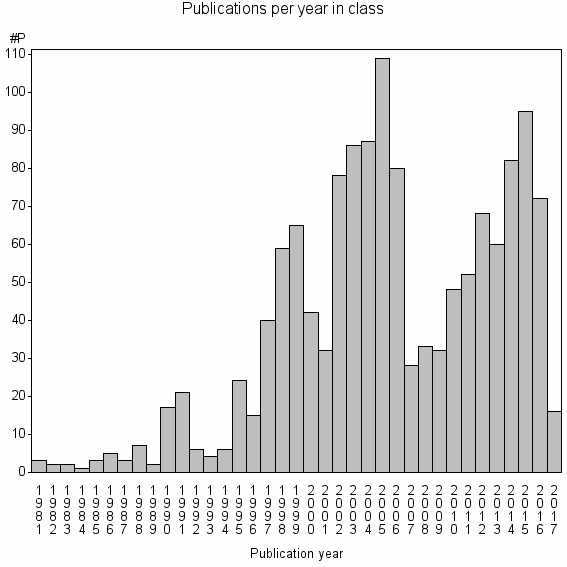
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 7292 | 1385 | 19.7 | 33% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
| Cluster id | Level | Cluster label | #P |
|---|---|---|---|
| 9 | 4 | COMPUTER SCIENCE, THEORY & METHODS//COMPUTER SCIENCE, ARTIFICIAL INTELLIGENCE//COMPUTER SCIENCE, INFORMATION SYSTEMS | 1247339 |
| 295 | 3 | CRYPTOGRAPHY//COMPUTER SCIENCE, THEORY & METHODS//IEEE TRANSACTIONS ON INFORMATION THEORY | 41419 |
| 2473 | 2 | BLOCK CIPHER//STREAM CIPHER//BOOLEAN FUNCTIONS | 3978 |
| 7292 | 1 | BLOCK CIPHER//DIFFERENTIAL CRYPTANALYSIS//HASH FUNCTION | 1385 |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | BLOCK CIPHER | authKW | 3885364 | 20% | 63% | 281 |
| 2 | DIFFERENTIAL CRYPTANALYSIS | authKW | 1041670 | 5% | 71% | 67 |
| 3 | HASH FUNCTION | authKW | 841894 | 9% | 32% | 120 |
| 4 | LINEAR CRYPTANALYSIS | authKW | 839565 | 4% | 73% | 52 |
| 5 | CRYPTANALYSIS | authKW | 478433 | 10% | 16% | 134 |
| 6 | RELATED KEY ATTACK | authKW | 475112 | 2% | 86% | 25 |
| 7 | IMPOSSIBLE DIFFERENTIAL CRYPTANALYSIS | authKW | 352728 | 1% | 100% | 16 |
| 8 | MODES OF OPERATION | authKW | 334146 | 2% | 63% | 24 |
| 9 | MESSAGE AUTHENTICATION CODE | authKW | 319985 | 2% | 48% | 30 |
| 10 | INDIFFERENTIABILITY | authKW | 310013 | 1% | 94% | 15 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Theory & Methods | 66311 | 60% | 0% | 829 |
| 2 | Computer Science, Information Systems | 21171 | 32% | 0% | 446 |
| 3 | Computer Science, Hardware & Architecture | 10027 | 15% | 0% | 212 |
| 4 | Computer Science, Software Engineering | 9597 | 19% | 0% | 270 |
| 5 | Engineering, Electrical & Electronic | 2330 | 26% | 0% | 354 |
| 6 | Mathematics, Applied | 1632 | 15% | 0% | 203 |
| 7 | Telecommunications | 1036 | 8% | 0% | 108 |
| 8 | History & Philosophy of Science | 361 | 2% | 0% | 26 |
| 9 | COMPUTER APPLICATIONS & CYBERNETICS | 70 | 0% | 0% | 3 |
| 10 | Computer Science, Artificial Intelligence | 35 | 2% | 0% | 27 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | ESAT COSIC | 222269 | 2% | 46% | 22 |
| 2 | CIST | 219807 | 3% | 21% | 48 |
| 3 | COSIC | 171627 | 2% | 27% | 29 |
| 4 | NTT SECURE PLATFORM S | 111751 | 1% | 30% | 17 |
| 5 | INFORMAT SECUR TECHNOL | 93330 | 2% | 18% | 24 |
| 6 | IAIK | 74392 | 1% | 38% | 9 |
| 7 | ELECT ENGN ESAT COSIC | 70544 | 0% | 80% | 4 |
| 8 | ESAT SCD COSIC | 68669 | 1% | 35% | 9 |
| 9 | INFORMAT SECUR GRP | 68265 | 2% | 11% | 28 |
| 10 | COMP INFORMAT MATH | 66137 | 0% | 100% | 3 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | JOURNAL OF CRYPTOLOGY | 238970 | 5% | 16% | 69 |
| 2 | CRYPTOLOGIA | 125220 | 2% | 23% | 25 |
| 3 | LECTURE NOTES IN COMPUTER SCIENCE | 81589 | 41% | 1% | 571 |
| 4 | IET INFORMATION SECURITY | 53625 | 2% | 9% | 28 |
| 5 | IEICE TRANSACTIONS ON FUNDAMENTALS OF ELECTRONICS COMMUNICATIONS AND COMPUTER SCIENCES | 53528 | 10% | 2% | 139 |
| 6 | DESIGNS CODES AND CRYPTOGRAPHY | 35838 | 4% | 3% | 53 |
| 7 | CRYPTOGRAPHY AND COMMUNICATIONS-DISCRETE-STRUCTURES BOOLEAN FUNCTIONS AND SEQUENCES | 20592 | 1% | 8% | 12 |
| 8 | SECURITY AND COMMUNICATION NETWORKS | 12433 | 2% | 2% | 28 |
| 9 | INTERNATIONAL JOURNAL OF INFORMATION SECURITY | 7662 | 1% | 3% | 10 |
| 10 | INFORMATION PROCESSING LETTERS | 6067 | 3% | 1% | 42 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | BLOCK CIPHER | 3885364 | 20% | 63% | 281 | Search BLOCK+CIPHER | Search BLOCK+CIPHER |
| 2 | DIFFERENTIAL CRYPTANALYSIS | 1041670 | 5% | 71% | 67 | Search DIFFERENTIAL+CRYPTANALYSIS | Search DIFFERENTIAL+CRYPTANALYSIS |
| 3 | HASH FUNCTION | 841894 | 9% | 32% | 120 | Search HASH+FUNCTION | Search HASH+FUNCTION |
| 4 | LINEAR CRYPTANALYSIS | 839565 | 4% | 73% | 52 | Search LINEAR+CRYPTANALYSIS | Search LINEAR+CRYPTANALYSIS |
| 5 | CRYPTANALYSIS | 478433 | 10% | 16% | 134 | Search CRYPTANALYSIS | Search CRYPTANALYSIS |
| 6 | RELATED KEY ATTACK | 475112 | 2% | 86% | 25 | Search RELATED+KEY+ATTACK | Search RELATED+KEY+ATTACK |
| 7 | IMPOSSIBLE DIFFERENTIAL CRYPTANALYSIS | 352728 | 1% | 100% | 16 | Search IMPOSSIBLE+DIFFERENTIAL+CRYPTANALYSIS | Search IMPOSSIBLE+DIFFERENTIAL+CRYPTANALYSIS |
| 8 | MODES OF OPERATION | 334146 | 2% | 63% | 24 | Search MODES+OF+OPERATION | Search MODES+OF+OPERATION |
| 9 | MESSAGE AUTHENTICATION CODE | 319985 | 2% | 48% | 30 | Search MESSAGE+AUTHENTICATION+CODE | Search MESSAGE+AUTHENTICATION+CODE |
| 10 | INDIFFERENTIABILITY | 310013 | 1% | 94% | 15 | Search INDIFFERENTIABILITY | Search INDIFFERENTIABILITY |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | ANDREEVA, E , MENNINK, B , PRENEEL, B , (2015) OPEN PROBLEMS IN HASH FUNCTION SECURITY.DESIGNS CODES AND CRYPTOGRAPHY. VOL. 77. ISSUE 2-3. P. 611 -631 | 31 | 100% | 2 |
| 2 | KIM, J , PHAN, RCW , (2009) ADVANCED DIFFERENTIAL-STYLE CRYPTANALYSIS OF THE NSA'S SKIPJACK BLOCK CIPHER.CRYPTOLOGIA. VOL. 33. ISSUE 3. P. 246 -270 | 29 | 100% | 4 |
| 3 | VAUDENAY, S , (2003) DECORRELATION: A THEORY FOR BLOCK CIPHER SECURITY.JOURNAL OF CRYPTOLOGY. VOL. 16. ISSUE 4. P. 249 -286 | 28 | 97% | 57 |
| 4 | LEE, DG , KIM, J , SUNG, J , LEE, YS , RHO, S , (2010) CRYPTANALYSIS OF BLOCK-WISE STREAM CIPHERS SUITABLE FOR THE PROTECTION OF MULTIMEDIA AND UBIQUITOUS SYSTEMS.TELECOMMUNICATION SYSTEMS. VOL. 44. ISSUE 3-4. P. 297 -306 | 23 | 100% | 2 |
| 5 | CHAKRABORTY, D , SARKAR, P , (2016) ON MODES OF OPERATIONS OF A BLOCK CIPHER FOR AUTHENTICATION AND AUTHENTICATED ENCRYPTION.CRYPTOGRAPHY AND COMMUNICATIONS-DISCRETE-STRUCTURES BOOLEAN FUNCTIONS AND SEQUENCES. VOL. 8. ISSUE 4. P. 455 -511 | 20 | 95% | 0 |
| 6 | JOYE, M , PHAN, RCW , RAZALI, E , SUNG, J , KIM, J , (2011) NOTIONS AND RELATIONS FOR RKA-SECURE PERMUTATION AND FUNCTION FAMILIES.DESIGNS CODES AND CRYPTOGRAPHY. VOL. 60. ISSUE 1. P. 15 -35 | 22 | 96% | 0 |
| 7 | GAURAVARAM, P , KNUDSEN, LR , (2012) SECURITY ANALYSIS OF RANDOMIZE-HASH-THEN-SIGN DIGITAL SIGNATURES.JOURNAL OF CRYPTOLOGY. VOL. 25. ISSUE 4. P. 748 -779 | 21 | 95% | 2 |
| 8 | SARKAR, P , (2010) PSEUDO-RANDOM FUNCTIONS AND PARALLELIZABLE MODES OF OPERATIONS OF A BLOCK CIPHER.IEEE TRANSACTIONS ON INFORMATION THEORY. VOL. 57. ISSUE 8. P. 4025 -4037 | 20 | 100% | 8 |
| 9 | SARKAR, P , (2014) MODES OF OPERATIONS FOR ENCRYPTION AND AUTHENTICATION USING STREAM CIPHERS SUPPORTING AN INITIALISATION VECTOR.CRYPTOGRAPHY AND COMMUNICATIONS-DISCRETE-STRUCTURES BOOLEAN FUNCTIONS AND SEQUENCES. VOL. 6. ISSUE 3. P. 189 -231 | 19 | 95% | 3 |
| 10 | LI, RL , LI, C , SU, JS , SUN, B , (2013) SECURITY EVALUATION OF MISTY STRUCTURE WITH SPN ROUND FUNCTION.COMPUTERS & MATHEMATICS WITH APPLICATIONS. VOL. 65. ISSUE 9. P. 1264 -1279 | 19 | 100% | 0 |
Classes with closest relation at Level 1 |