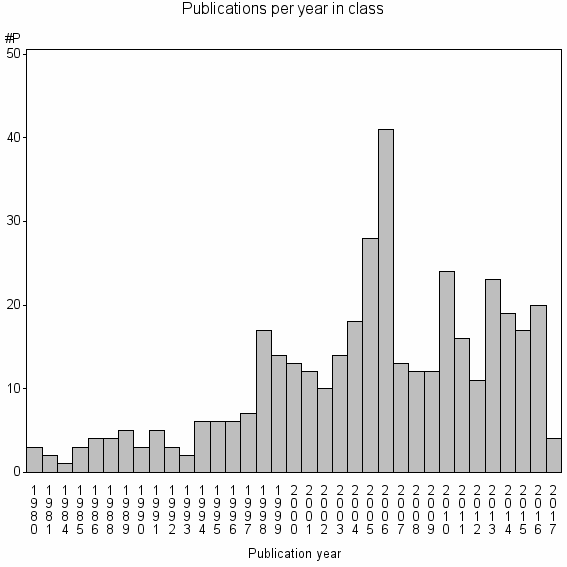
Class information for: |
Basic class information |
| Class id | #P | Avg. number of references |
Database coverage of references |
|---|---|---|---|
| 21991 | 398 | 20.4 | 30% |
Hierarchy of classes |
The table includes all classes above and classes immediately below the current class. |
Terms with highest relevance score |
| rank | Term | termType | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|---|
| 1 | MULTIVARIATE PUBLIC KEY CRYPTOSYSTEM | authKW | 1231799 | 4% | 94% | 17 |
| 2 | MULTIVARIATE CRYPTOGRAPHY | authKW | 864389 | 3% | 87% | 13 |
| 3 | SFLASH | authKW | 460327 | 2% | 100% | 6 |
| 4 | F 5 ALGORITHM | authKW | 446373 | 2% | 73% | 8 |
| 5 | GROBNER BASES | authKW | 442544 | 11% | 13% | 45 |
| 6 | MQ PROBLEM | authKW | 409174 | 2% | 67% | 8 |
| 7 | HIDDEN FIELD EQUATION | authKW | 383606 | 1% | 100% | 5 |
| 8 | DIFFERENCE DIFFERENTIAL MODULE | authKW | 306885 | 1% | 100% | 4 |
| 9 | ISOMORPHISM OF POLYNOMIALS | authKW | 306885 | 1% | 100% | 4 |
| 10 | MULTIVARIATE PUBLIC KEY CRYPTOGRAPHY | authKW | 306885 | 1% | 100% | 4 |
Web of Science journal categories |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | Computer Science, Theory & Methods | 9839 | 43% | 0% | 172 |
| 2 | Mathematics, Applied | 3393 | 37% | 0% | 147 |
| 3 | Computer Science, Software Engineering | 1513 | 15% | 0% | 58 |
| 4 | Mathematics | 772 | 20% | 0% | 80 |
| 5 | Computer Science, Information Systems | 761 | 12% | 0% | 47 |
| 6 | Computer Science, Hardware & Architecture | 457 | 6% | 0% | 25 |
| 7 | Computer Science, Interdisciplinary Applications | 266 | 8% | 0% | 30 |
| 8 | Physics, Mathematical | 66 | 4% | 0% | 17 |
| 9 | Engineering, Electrical & Electronic | 27 | 8% | 0% | 30 |
| 10 | Telecommunications | 15 | 2% | 0% | 9 |
Address terms |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | CRYPTO CP8 | 175359 | 1% | 57% | 4 |
| 2 | AG MADLENER | 76721 | 0% | 100% | 1 |
| 3 | ALGORITHMEN KOGNITIVE SYSTEME | 76721 | 0% | 100% | 1 |
| 4 | CNRSUFR INGN 919UMR 7606LIP6 | 76721 | 0% | 100% | 1 |
| 5 | EQUIPE COMBINATOIRE ALGORITHMES | 76721 | 0% | 100% | 1 |
| 6 | EQUIPE POLSVS | 76721 | 0% | 100% | 1 |
| 7 | HBEREICH INFORNAT | 76721 | 0% | 100% | 1 |
| 8 | INRI OLSYS PROJECTUMR 7606 | 76721 | 0% | 100% | 1 |
| 9 | LEHHSTUHL B MATH | 76721 | 0% | 100% | 1 |
| 10 | LEHRSTUHL MATHEMAT B | 76721 | 0% | 100% | 1 |
Journals |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
|---|---|---|---|---|---|
| 1 | PROGRAMMING AND COMPUTER SOFTWARE | 107830 | 9% | 4% | 34 |
| 2 | JOURNAL OF SYMBOLIC COMPUTATION | 106728 | 14% | 2% | 56 |
| 3 | APPLICABLE ALGEBRA IN ENGINEERING COMMUNICATION AND COMPUTING | 12620 | 3% | 2% | 10 |
| 4 | DESIGNS CODES AND CRYPTOGRAPHY | 5366 | 3% | 1% | 11 |
| 5 | LECTURE NOTES IN COMPUTER SCIENCE | 5217 | 20% | 0% | 78 |
| 6 | JOURNAL OF SYSTEMS SCIENCE & COMPLEXITY | 3390 | 2% | 1% | 6 |
| 7 | IEICE TRANSACTIONS ON FUNDAMENTALS OF ELECTRONICS COMMUNICATIONS AND COMPUTER SCIENCES | 3104 | 5% | 0% | 18 |
| 8 | FINITE FIELDS AND THEIR APPLICATIONS | 2696 | 2% | 1% | 6 |
| 9 | SCIENCE CHINA-MATHEMATICS | 1992 | 2% | 0% | 6 |
| 10 | APPLIED AND COMPUTATIONAL MATHEMATICS | 1137 | 1% | 1% | 2 |
Author Key Words |
| Rank | Term | Chi square | Shr. of publ. in class containing term |
Class's shr. of term's tot. occurrences |
#P with term in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | MULTIVARIATE PUBLIC KEY CRYPTOSYSTEM | 1231799 | 4% | 94% | 17 | Search MULTIVARIATE+PUBLIC+KEY+CRYPTOSYSTEM | Search MULTIVARIATE+PUBLIC+KEY+CRYPTOSYSTEM |
| 2 | MULTIVARIATE CRYPTOGRAPHY | 864389 | 3% | 87% | 13 | Search MULTIVARIATE+CRYPTOGRAPHY | Search MULTIVARIATE+CRYPTOGRAPHY |
| 3 | SFLASH | 460327 | 2% | 100% | 6 | Search SFLASH | Search SFLASH |
| 4 | F 5 ALGORITHM | 446373 | 2% | 73% | 8 | Search F+5+ALGORITHM | Search F+5+ALGORITHM |
| 5 | GROBNER BASES | 442544 | 11% | 13% | 45 | Search GROBNER+BASES | Search GROBNER+BASES |
| 6 | MQ PROBLEM | 409174 | 2% | 67% | 8 | Search MQ+PROBLEM | Search MQ+PROBLEM |
| 7 | HIDDEN FIELD EQUATION | 383606 | 1% | 100% | 5 | Search HIDDEN+FIELD+EQUATION | Search HIDDEN+FIELD+EQUATION |
| 8 | DIFFERENCE DIFFERENTIAL MODULE | 306885 | 1% | 100% | 4 | Search DIFFERENCE+DIFFERENTIAL+MODULE | Search DIFFERENCE+DIFFERENTIAL+MODULE |
| 9 | ISOMORPHISM OF POLYNOMIALS | 306885 | 1% | 100% | 4 | Search ISOMORPHISM+OF+POLYNOMIALS | Search ISOMORPHISM+OF+POLYNOMIALS |
| 10 | MULTIVARIATE PUBLIC KEY CRYPTOGRAPHY | 306885 | 1% | 100% | 4 | Search MULTIVARIATE+PUBLIC+KEY+CRYPTOGRAPHY | Search MULTIVARIATE+PUBLIC+KEY+CRYPTOGRAPHY |
Core articles |
The table includes core articles in the class. The following variables is taken into account for the relevance score of an article in a cluster c: (1) Number of references referring to publications in the class. (2) Share of total number of active references referring to publications in the class. (3) Age of the article. New articles get higher score than old articles. (4) Citation rate, normalized to year. |
| Rank | Reference | # ref. in cl. |
Shr. of ref. in cl. |
Citations |
|---|---|---|---|---|
| 1 | WANG, LC , YANG, BY , HU, YH , LAI, FP , (2006) A "MEDIUM-FIELD" MULTIVARIATE PUBLIC-KEY ENCRYPTION SCHEME.TOPICS IN CRYPTOLOGY - CT-RSA 2006, PROCEEDINGS. VOL. 3860. ISSUE . P. 132 -149 | 23 | 96% | 20 |
| 2 | HASHIMOTO, Y , TAKAGI, T , SAKURAI, K , (2013) GENERAL FAULT ATTACKS ON MULTIVARIATE PUBLIC KEY CRYPTOSYSTEMS.IEICE TRANSACTIONS ON FUNDAMENTALS OF ELECTRONICS COMMUNICATIONS AND COMPUTER SCIENCES. VOL. E96A. ISSUE 1. P. 196 -205 | 20 | 80% | 1 |
| 3 | NIE, XY , PETZOLDT, A , BUCHMANN, J , LI, FG , (2014) LINEARIZATION EQUATION ATTACK ON 2-LAYER NONLINEAR PIECE IN HAND METHOD.IEICE TRANSACTIONS ON FUNDAMENTALS OF ELECTRONICS COMMUNICATIONS AND COMPUTER SCIENCES. VOL. E97A. ISSUE 9. P. 1952 -1961 | 15 | 100% | 0 |
| 4 | HASHIMOTO, Y , (2016) CRYPTANALYSIS OF THE MULTIVARIATE SIGNATURE SCHEME PROPOSED IN PQCRYPTO 2013.IEICE TRANSACTIONS ON FUNDAMENTALS OF ELECTRONICS COMMUNICATIONS AND COMPUTER SCIENCES. VOL. E99A. ISSUE 1. P. 58 -65 | 13 | 100% | 0 |
| 5 | ZHAO, X , FENG, D , (2010) BYPASSING THE DECOMPOSITION ATTACKS ON TWO-ROUND MULTIVARIATE SCHEMES BY A PRACTICAL CUBIC ROUND.IET INFORMATION SECURITY. VOL. 4. ISSUE 3. P. 167 -184 | 21 | 70% | 1 |
| 6 | EDER, C , FAUGERE, JC , (2017) A SURVEY ON SIGNATURE-BASED ALGORITHMS FOR COMPUTING GROBNER BASES.JOURNAL OF SYMBOLIC COMPUTATION. VOL. 80. ISSUE . P. 719 -784 | 18 | 67% | 0 |
| 7 | GOTAISHI, M , TADAKI, K , FUJITA, R , TSUJII, S , (2010) DUALLY-PERTURBED MATSUMOTO-IMAI SIGNATURE (DPMS) SCHEME.IEICE TRANSACTIONS ON FUNDAMENTALS OF ELECTRONICS COMMUNICATIONS AND COMPUTER SCIENCES. VOL. E93A. ISSUE 6. P. 1078 -1085 | 12 | 100% | 0 |
| 8 | HU, YH , CHOU, CY , WANG, LC , LAI, F , (2006) CRYPTANALYSIS OF VARIANTS OF UOV.INFORMATION SECURITY, PROCEEDINGS. VOL. 4176. ISSUE . P. 161-170 | 12 | 100% | 1 |
| 9 | TSUJII, S , TADAKI, K , FUJITA, R , GOTAISHI, M , KANEKO, T , (2009) SECURITY ENHANCEMENT OF VARIOUS MPKCS BY 2-LAYER NONLINEAR PIECE IN HAND METHOD.IEICE TRANSACTIONS ON FUNDAMENTALS OF ELECTRONICS COMMUNICATIONS AND COMPUTER SCIENCES. VOL. E92A. ISSUE 10. P. 2438 -2446 | 11 | 100% | 2 |
| 10 | SUN, Y , HUANG, ZY , WANG, DK , LIN, DD , (2016) AN IMPROVEMENT OVER THE GVW ALGORITHM FOR INHOMOGENEOUS POLYNOMIAL SYSTEMS.FINITE FIELDS AND THEIR APPLICATIONS. VOL. 41. ISSUE . P. 174 -192 | 10 | 91% | 0 |
Classes with closest relation at Level 1 |