Pontus Johnson
Professor
Details
Researcher
About me
Pontus Johnson is a professor at the KTH Royal Institute of Technology in Stockholm, Sweden. His research interests mainly lie in the area of cyber security and the analysis of architectural models of computer networks – in particular simulating cyber attacks on such networks. Pontus supervises a number of PhD students and holds courses in Ethical hacking.
He is the director of the Center for Cyber Defense and Information Security at KTH, a collaboration with the Swedish Armed Forces, the National Defence Radio Establishment (FRA), the Swedish Civil Contingencies Agency (MSB), The Swedish Defence Research Agency (FOI) and the Swedish Defense University (FHS).
He is also the vice director of the national initiative Cybercampus Sweden, inaugurated February of 2024.
He received his MSc from the Lund Institute of Technology in 1997 and his PhD and Docent titles from the Royal Institute of Technology in 2002 and 2007. He was appointed professor in 2009.
Since 2013, Pontus is a member of the Swedish Royal Academy of Engineering Sciences (IVA). From 2024, he is serving on the IVA board as deputy chair. He has previously participated in various IVA projects – most notably the project on Cybersecurity and Competitiveness – chaired IVA's Division II, been a member of the medal committee, among other things.
From 2025, Pontus serves on the board of the Swedish Research Council.
In 2014, he co-foundedForeseeti, a research spin-off company developing cyber security attack simulation software. Foreseeti was acquired by Google in 2022. Since 2023, Google offers Attack Path Simulations to its Cloud customers based on the technology developed by Pontus and his research colleagues. Pontus worked at Google Cloud one day per week from 2022 to 2025.
In 2025, he left Google and started a new company, Nørdsnipe, together with Jacob Henricson, Erik Ringdahl, Sven Hagströmer and Lars Stugemo. Nørdsnipe develops an AI assistant for security testing.
In 2021, Pontus was credited with the discovery of the worlds oldest security vulnerability, in the universal Turing machine. In 2022 as well as 2023, Tech Awards Sweden listed him among the 50 most influential people in Swedish tech.
He has chaired, co-chaired, and participated as steering committee member in many international conferences and workshops and participated in program committees in over fifty such events. He has authored well over 100 scientific articles, mainly on the assessment and prediction of cyber security and other non-functional properties in software and computer networks.
Pontus spends 20% of his work time at Nørdsnipe. In the remaining 80%, he is a member of the Software Systems Architecture and Security (SSAS) research group within the Division of Network and Systems Engineering (NSE) at the Department of Computer Science in the School of Electrical Engineering and Computer Science (EECS) at KTH.
Ph.D. Students
If you would like to develop your expertise significantly, consider applying for a PhD student position in our group. We regularly announce new positions.
Simon Gökstorp (Main Supervisor)
Jakob Nyberg (Main Supervisor)
Nikolaos Kakouros (Main Supervisor)
Sotirios Katsikeas (Main Supervisor)
Sandor Berglund (Assistant Supervisor)
Yeongwoo Kim (Assistant Supervisor)
Fredrik Heiding (2024) (Assistant Supervisor)
Kim Hammar (2024) (Assistant Supervisor)
Margus Välja (2018) (Assistant Supervisor)
Markus Buschle (2014) (Main Supervisor)
Moustafa Chenine (2013) (Assistant Supervisor)
Ulrik Franke (2012) (Main Supervisor)
Per Narman (2012) (Assistant Supervisor)
Robert Lagerstrom (2010) (Main Supervisor)
Marten Simonsson (2008) (Main Supervisor)
Magnus Gammelgard (2007) (Assistant Supervisor)
Asa Lindstrom (2006) (Assistant Supervisor)
Erik Johansson (2005) (Assistant Supervisor)
Publications
Pontus publication are (usually) available in a link on the right-hand side of the page, and also on Google Scholar.
Vulnerabilities
Check out vulnerabilities discovered by Pontus, his colleagues and students in the Software Systems Architecture and Security (SSAS) research group.
Media Coverage
Television
 Swedish TV interview live hacking demonstration.
Swedish TV interview live hacking demonstration.
 SVT Aktuellt on cyber security (in Swedish).
SVT Aktuellt on cyber security (in Swedish).
 Interview on the Center for Cyber Defense and Information Security.
Interview on the Center for Cyber Defense and Information Security.
 Swedish TV interview on the vulnerabilities of smart consumer products.
Swedish TV interview on the vulnerabilities of smart consumer products.
 Swedish TV interview on the vulnerabilities of the 5G network.
Swedish TV interview on the vulnerabilities of the 5G network.
Expert: Så skyddar du dig i de populära träningsapparna (SVT Nyheter, Juli 2025)
Så lätt hackas ditt barns smarta klocka (SVT Nyheter, Juni 2024)
Så används AI-verktyg i hackerattacker (SVT Nyheter, Feb 2024)
Aftonbladet erbjuds köpa hemliga uppgifter – av ryska hackare (Aftonbladet, Feb 2024)
Professorn: Myndigheter bör inte prata hemligheter i en Volvo (SVT Nyheter, Juni 2023)
Professor: Vi har överskattat det ryska cybervapnet (SVT Nyheter, April 2023)
Professor i it-säkerhet: Tiktokförbud överdrivet trubbigt (SVT Agenda, Mars 2023)
Kommentar om Turk Hack Teams angrepp mot Sverige (SVT Rapport, Feb 2023)
Cybersäkerhetsexperten: Datasystemen överraskande sårbara (SVT Aktuellt, Maj 2022)
Vad är en cyberattack? (SVT Lilla Aktuellt, Maj 2022)
Intervju om cybersäkerhet (SVT Aktuellt, Oct 2021)
Forskaren om största hackerhoten: Har lyckats ta över pacemakers (SVT Aktuellt)
Folk och Försvar, Cybersäkerhet i digitaliseringens tid (SVT Forum)
Digitala lås kan hackas och styras av kunniga tjuvar – så väljer du rätt (SVT Nyheter Västmanland)
5g-auktionerna avslutade – utan Kina (SVT Rapport)
YouTube
Cyberblick: Hur ökar digitaliseringen sårbarheten i energisystemet? (Energiutblick 2021)
Radio/Podcast
IT-säkerhet och cyberhotet - AI:s påverkan (Trygghetspodden, Jan 2026)
Ständiga “driftstörningar” och cyberattacker – hur mår Sveriges beredskap? (Sveriges Radio UR, Juni 2025)
Bank-ID down for several hours due to cyber attack (Radio Sweden)
Kina har använt svenskars routrar för cyberattacker (Sveriges Radio P1 Studio Ett)
Starka reaktioner i Kina efter amerikanskt Tiktokförslag (Sveriges Radio P1 Studio Ett)
Fler it-attacker tvingar företag att satsa mer på säkerhet (Sveriges Radio P1)
Ryska hackare med dunkla motiv bakom it-attacken (Sveriges Radio P1 Ekonomiekot Extra)
Pegasus, prinsen och en mördad journalist (Podden Månskott)
EU kallar in cyberstyrka efter hackerattacker mot Ukraina (Sveriges Radio P1 Studio Ett)
KTH-professor: Uppmuntra era barn att bli etiska hackare (Sveriges Radio P4 Gotland)
Executing arbitrary Turing tapes (Risky Business podcast)
Är telefonspionaget ett hot mot demokratin? (Sveriges Radio P1 Studio Ett)
TILL SALU: Företagshemligheter och privata detaljer (Sveriges Radio P1 Ekonomiekot Extra)
Om cyberkriget kommer (Sveriges Radio P1 Konflikt)
Rolf möter Pontus Johnson från KTH (Cyber Talks)
Säkerhetsexperten: "Region Gotland hade kunnat skydda sig mycket bättre" (Sveriges Radio P4 Gotland)
Avslöjandet som beskrivs som något av århundradets underrättelsekupp (Sveriges Radio Studio Ett)
New research center aims to fortify Sweden's cyber defenses (Sveriges Radio, Radio Sweden)
Kurser i etisk hackning ska öka it-säkerhet (Sveriges Radio P1 Ekot)
Den goda hackern (Sveriges Radio P1 Uppkopplad)
KTH utbildar i etisk hackning (Sveriges Radio P3)
News articles
Han hackar för säkerhet (Karriär)
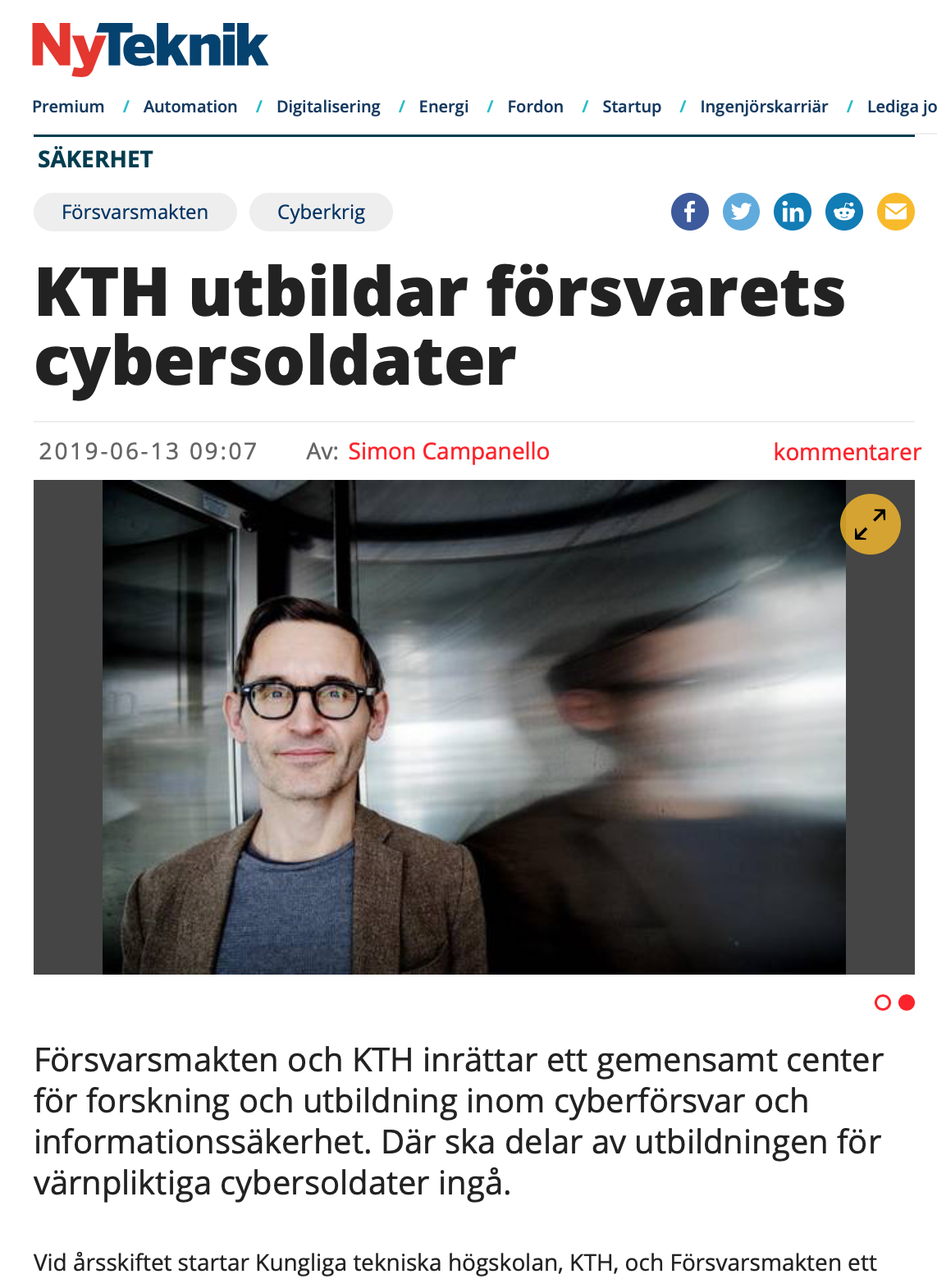
Cybersoldater ska skydda samhällets system mot hackare (KTH)
KTH öppnar sin utbildning i etisk hackning – företagen också välkomna (Computer Sweden)
Ny KTH-kurs ska lära företag att tänka som hackare (Ny Teknik)
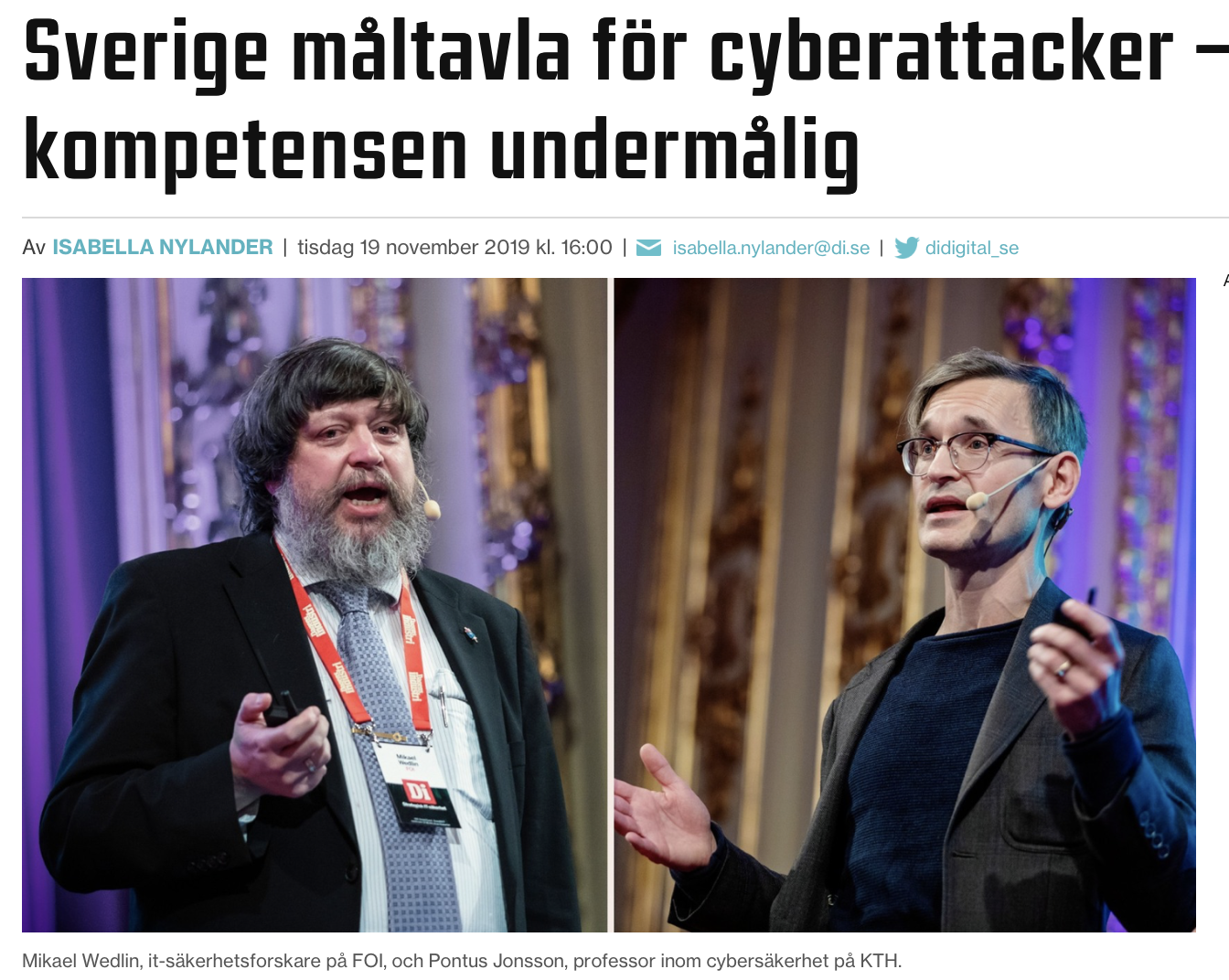
Han utbildar företagare till hackare (DI)
Vithattar blir svarta på KTH (Voister)
Nu kan du plugga till hackare på KTH (Computer Sweden)
Swedish University Offers ‘Ethical Hacking' Courses for 'Greater IT Security' (Sputnik news)
Hacking Master Thesis Projects
If you would like to do a master thesis project aimed at hacking something, don't hesitate to contact me. Previous projects have targeted control systems, electric locks, electric scooters, motor vehicle remote control units,and more.
Some students were featured in Swedish news outlets in recent years.
Attacken på det uppkopplade hemmet
 Så lätt hackas ditt barns smarta klocka
Så lätt hackas ditt barns smarta klocka
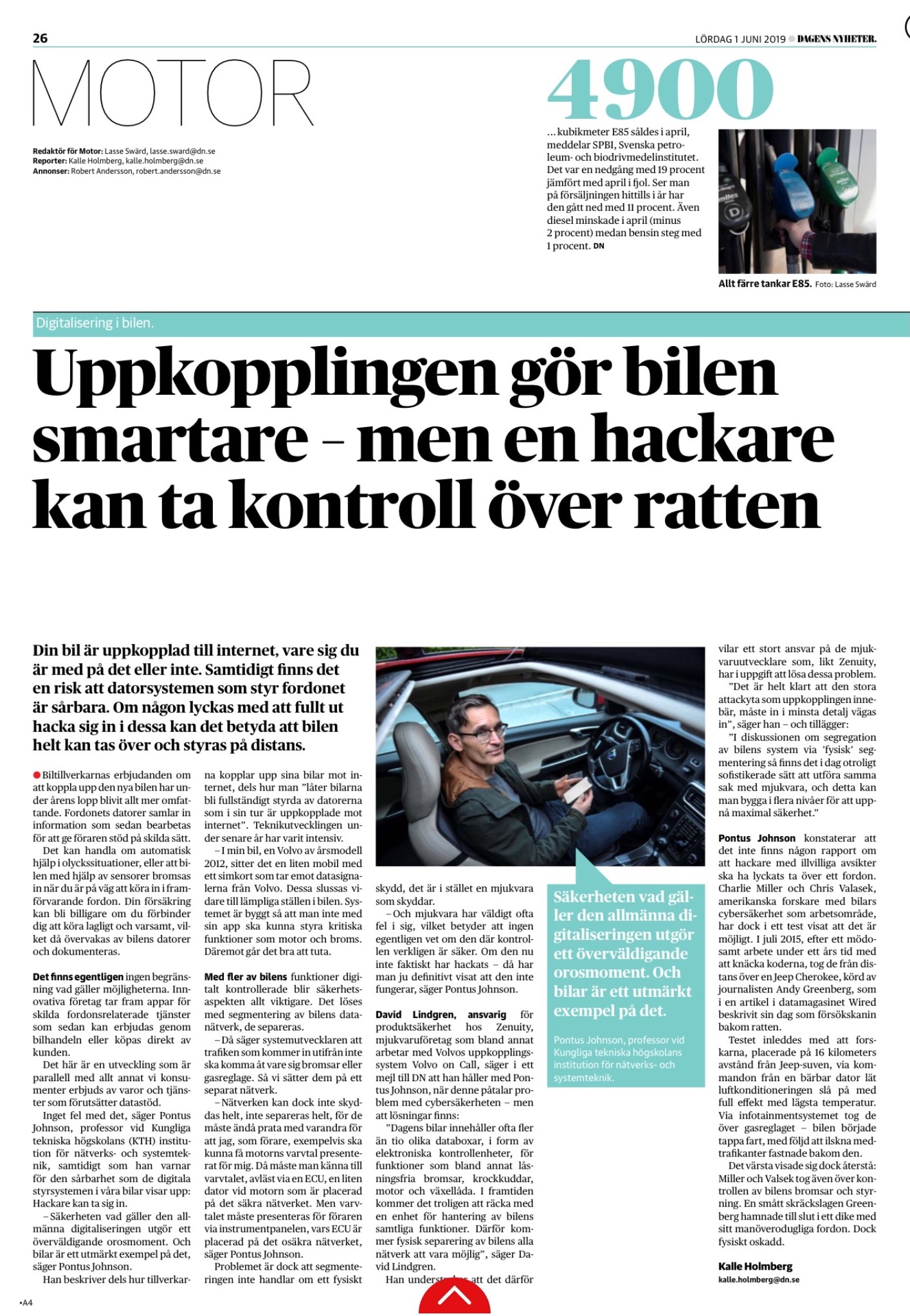
 SVT - Varningen: Uppkopplade bilar kan hackas och tas över
SVT - Varningen: Uppkopplade bilar kan hackas och tas över
 SVT - Hon fixade systemets kryphål: ”Ditt garage kan bli kriminellt”
SVT - Hon fixade systemets kryphål: ”Ditt garage kan bli kriminellt”
 TV4 Nyheter - KTH-studenter hackar robotdammsugare
TV4 Nyheter - KTH-studenter hackar robotdammsugare
 SVT - Här hackar KTH-studenten elsparkcykeln i farten och låser den
SVT - Här hackar KTH-studenten elsparkcykeln i farten och låser den
Courses
Advanced Ethical Hacking (FEP3370), teacher, course responsible, examiner
Degree Project in Computer Engineering, First Cycle (II142X), examiner
Degree Project in Computer Science and Engineering, Second Cycle (DA239X), examiner
Degree Project in Computer Science and Engineering, Second Cycle (DA250X), examiner
Degree Project in Computer Science and Engineering, Second Cycle (DA231X), examiner
Degree Project in Electrical Engineering, Second Cycle (EA250X), examiner
Degree Project in Electrical Engineering, Second Cycle (EA238X), examiner
Degree Project in Electrical Engineering, specialising in ICT Innovation, Second Cycle (EA258X), examiner
Degree Project in Electrical Engineering, specialising in ICT Innovation, Second Cycle (EA256X), examiner
Degree Project in Electronics and Computer Engineering, First Cycle (IL142X), examiner
Degree Project in Information and Communication Technology, First Cycle (IA150X), examiner
Ethical Hacking (EN2720), teacher, course responsible, examiner
Ethical Hacking (EP283U), examiner, course responsible
Ethical Hacking (EP282U), course responsible, examiner
Ethical Hacking I (EP274V), examiner, course responsible
Ethical Hackning, project assignment (EP284U), teacher, examiner
Ethical hacking II (EP275V), examiner, course responsible
Seminar on Advanced Topics in Communication Networks 1 (FEP3316), examiner
Seminar on Advanced Topics in Communication Networks 2 (FEP3317), examiner