Class information for: |
Basic class information |
| ID | Publications | Average number of references |
Avg. shr. active ref. in WoS |
|---|---|---|---|
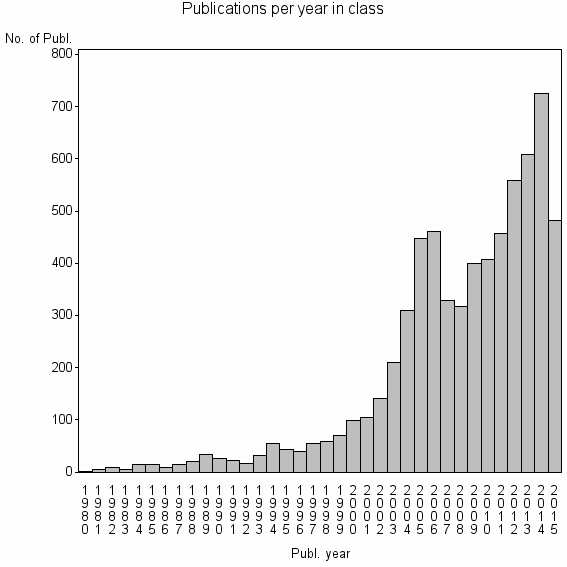
| 1591 | 6600 | 29.1 | 25% |
Classes in level above (level 3) |
| ID, lev. above |
Publications | Label for level above |
|---|---|---|
| 39 | 101210 | TELECOMMUNICATIONS//COMPUTER SCIENCE, INFORMATION SYSTEMS//COMPUTER SCIENCE, THEORY & METHODS |
Classes in level below (level 1) |
Terms with highest relevance score |
| Rank | Term | Type of term | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|---|
| 1 | DIGITAL INVESTIGATION | Journal | 325 | 72% | 4% | 255 |
| 2 | COMPUTERS & SECURITY | Journal | 263 | 44% | 7% | 453 |
| 3 | INTRUSION DETECTION | Author keyword | 80 | 18% | 6% | 399 |
| 4 | IEEE SECURITY & PRIVACY | Journal | 61 | 30% | 3% | 168 |
| 5 | COMPUTER SECURITY | Author keyword | 42 | 24% | 2% | 153 |
| 6 | DIGITAL FORENSICS | Author keyword | 36 | 25% | 2% | 123 |
| 7 | NETWORK SECURITY | Author keyword | 31 | 12% | 4% | 255 |
| 8 | ANOMALY DETECTION | Author keyword | 24 | 11% | 3% | 200 |
| 9 | INFORMATION SECURITY | Author keyword | 22 | 11% | 3% | 194 |
| 10 | TRAFFIC CLASSIFICATION | Author keyword | 22 | 32% | 1% | 57 |
Web of Science journal categories |
Author Key Words |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | INTRUSION DETECTION | 80 | 18% | 6% | 399 | Search INTRUSION+DETECTION | Search INTRUSION+DETECTION |
| 2 | COMPUTER SECURITY | 42 | 24% | 2% | 153 | Search COMPUTER+SECURITY | Search COMPUTER+SECURITY |
| 3 | DIGITAL FORENSICS | 36 | 25% | 2% | 123 | Search DIGITAL+FORENSICS | Search DIGITAL+FORENSICS |
| 4 | NETWORK SECURITY | 31 | 12% | 4% | 255 | Search NETWORK+SECURITY | Search NETWORK+SECURITY |
| 5 | ANOMALY DETECTION | 24 | 11% | 3% | 200 | Search ANOMALY+DETECTION | Search ANOMALY+DETECTION |
| 6 | INFORMATION SECURITY | 22 | 11% | 3% | 194 | Search INFORMATION+SECURITY | Search INFORMATION+SECURITY |
| 7 | TRAFFIC CLASSIFICATION | 22 | 32% | 1% | 57 | Search TRAFFIC+CLASSIFICATION | Search TRAFFIC+CLASSIFICATION |
| 8 | COMPUTER VIRUS | 21 | 43% | 1% | 37 | Search COMPUTER+VIRUS | Search COMPUTER+VIRUS |
| 9 | LIVE FORENSICS | 20 | 67% | 0% | 18 | Search LIVE+FORENSICS | Search LIVE+FORENSICS |
| 10 | MALWARE | 16 | 19% | 1% | 77 | Search MALWARE | Search MALWARE |
Key Words Plus |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | MALICIOUS OBJECTS | 112 | 97% | 0% | 32 |
| 2 | INTRUSION DETECTION | 56 | 28% | 3% | 171 |
| 3 | DDOS ATTACKS | 38 | 69% | 1% | 33 |
| 4 | POLICY COMPLIANCE | 36 | 83% | 0% | 20 |
| 5 | SYSTEMS SECURITY | 30 | 79% | 0% | 19 |
| 6 | INFORMATION SECURITY | 30 | 45% | 1% | 50 |
| 7 | SERVICE ATTACKS | 20 | 51% | 0% | 28 |
| 8 | ANOMALY DETECTION | 20 | 22% | 1% | 80 |
| 9 | COMPUTER ABUSE | 20 | 67% | 0% | 18 |
| 10 | MALWARE | 18 | 45% | 0% | 29 |
Journals |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | DIGITAL INVESTIGATION | 325 | 72% | 4% | 255 |
| 2 | COMPUTERS & SECURITY | 263 | 44% | 7% | 453 |
| 3 | IEEE SECURITY & PRIVACY | 61 | 30% | 3% | 168 |
| 4 | SECURITY AND COMMUNICATION NETWORKS | 19 | 14% | 2% | 124 |
| 5 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 13 | 17% | 1% | 70 |
| 6 | INTERNATIONAL JOURNAL OF CRITICAL INFRASTRUCTURE PROTECTION | 9 | 25% | 0% | 29 |
| 7 | INTERNATIONAL JOURNAL OF INFORMATION SECURITY | 6 | 16% | 1% | 37 |
| 8 | INTERNATIONAL JOURNAL OF NETWORK MANAGEMENT | 4 | 14% | 0% | 29 |
| 9 | ACM TRANSACTIONS ON INFORMATION AND SYSTEM SECURITY | 3 | 13% | 0% | 23 |
Reviews |
| Title | Publ. year | Cit. | Active references |
% act. ref. to same field |
|---|---|---|---|---|
| Security Challenges for Medical Devices | 2015 | 1 | 3 | 100% |
| A survey of intrusion detection techniques in Cloud | 2013 | 28 | 4 | 100% |
| An intrusion detection and prevention system in cloud computing: A systematic review | 2013 | 20 | 33 | 82% |
| Intrusion detection system: A comprehensive review | 2013 | 19 | 32 | 59% |
| Intrusion detection by machine learning: A review | 2009 | 62 | 30 | 80% |
| Network attacks: Taxonomy, tools and systems | 2014 | 3 | 21 | 90% |
| The use of computational intelligence in intrusion detection systems: A review | 2010 | 88 | 84 | 40% |
| A review of machine learning approaches to Spam filtering | 2009 | 59 | 51 | 75% |
| Biometric personal authentication using keystroke dynamics: A review | 2011 | 26 | 18 | 83% |
| A survey of network flow applications | 2013 | 9 | 21 | 90% |
Address terms |
| Rank | Address term | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | SECUR COMMUN NETWORK | 17 | 100% | 0.1% | 8 |
| 2 | INFORMAT ASSURANCE GRP | 15 | 67% | 0.2% | 14 |
| 3 | MECHATRON CONTROL | 14 | 45% | 0.3% | 23 |
| 4 | IS SECUR | 13 | 80% | 0.1% | 8 |
| 5 | FORENS COMP | 9 | 83% | 0.1% | 5 |
| 6 | RELIABLE SOFTWARE GRP | 9 | 67% | 0.1% | 8 |
| 7 | COMP SYST TECHNOL | 7 | 21% | 0.5% | 32 |
| 8 | INFORMAT MANAGEMENT INT BUSINESS | 6 | 80% | 0.1% | 4 |
| 9 | INFORMAT SECUR EXCELLENCE | 6 | 80% | 0.1% | 4 |
| 10 | SMARTNESS SEMANT SECUR S3 | 6 | 80% | 0.1% | 4 |
Related classes at same level (level 2) |
| Rank | Relatedness score | Related classes |
|---|---|---|
| 1 | 0.0000015655 | PRIVACY CALCULUS//ACCESS CONTROL//INFORMATION PRIVACY |
| 2 | 0.0000014944 | CONCEPTUAL IMMUNOL GRP//SEQUENCE UNIQUENESS//ARTIFICIAL IMMUNE SYSTEMS |
| 3 | 0.0000014645 | ACM SIGCOMM COMPUTER COMMUNICATION REVIEW//PEER-TO-PEER NETWORKING AND APPLICATIONS//PEER TO PEER |
| 4 | 0.0000009702 | RISK MANAGEMENT ENGN SYST//NETWORK INTERDICTION//J VALUE |
| 5 | 0.0000008746 | CREDIT SCORING//MACHINE LEARNING//FEATURE SELECTION |
| 6 | 0.0000007398 | ASSOCIATION RULES//SEQUENTIAL PATTERNS//UTILITY MINING |
| 7 | 0.0000005743 | WIRELESS SENSOR NETWORKS//AD HOC NETWORKS//INTERNATIONAL JOURNAL OF DISTRIBUTED SENSOR NETWORKS |
| 8 | 0.0000005546 | HUMAN INTERACTIVE PROOFS//CAPTCHA//CAPTCHAS |
| 9 | 0.0000005359 | STRING MATCHING//DATA STRUCTURES//SUCCINCT DATA STRUCTURES |
| 10 | 0.0000005052 | ACM SIGPLAN NOTICES//REGISTER ALLOCATION//GARBAGE COLLECTION |