Class information for: |
Basic class information |
| ID | Publications | Average number of references |
Avg. shr. active ref. in WoS |
|---|---|---|---|
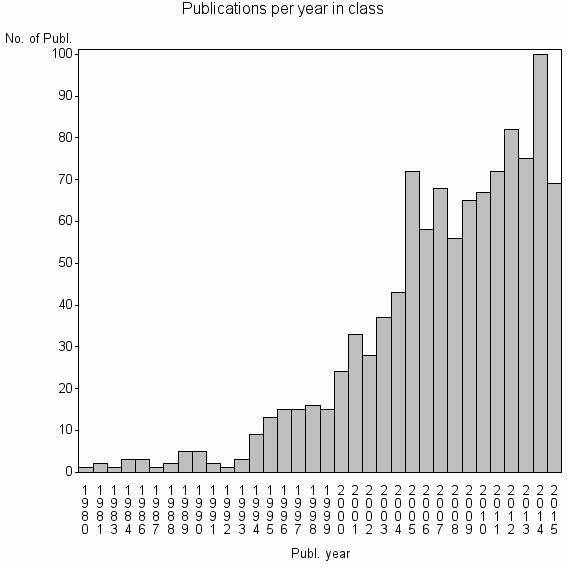
| 9732 | 1061 | 36.4 | 28% |
Classes in level above (level 2) |
| ID, lev. above |
Publications | Label for level above |
|---|---|---|
| 1591 | 6600 | DIGITAL INVESTIGATION//COMPUTERS & SECURITY//INTRUSION DETECTION |
Terms with highest relevance score |
| Rank | Term | Type of term | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|---|
| 1 | COMPUTERS & SECURITY | Journal | 46 | 20% | 19% | 206 |
| 2 | INFORMATION SYSTEMS SECURITY | Author keyword | 14 | 43% | 2% | 25 |
| 3 | IS SECUR | Address | 13 | 80% | 1% | 8 |
| 4 | INFORMATION SECURITY MANAGEMENT | Author keyword | 11 | 31% | 3% | 29 |
| 5 | COMPUTER ABUSE | Author keyword | 8 | 70% | 1% | 7 |
| 6 | BEHAVIORAL INFORMATION SECURITY | Author keyword | 8 | 100% | 0% | 5 |
| 7 | GENERAL DETERRENCE THEORY | Author keyword | 6 | 71% | 0% | 5 |
| 8 | IS SECURITY | Author keyword | 6 | 43% | 1% | 10 |
| 9 | SECURITY AWARENESS | Author keyword | 5 | 33% | 1% | 13 |
| 10 | SECURITY INVESTMENT | Author keyword | 4 | 42% | 1% | 8 |
Web of Science journal categories |
Author Key Words |
Key Words Plus |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | POLICY COMPLIANCE | 36 | 83% | 2% | 20 |
| 2 | SYSTEMS SECURITY | 30 | 79% | 2% | 19 |
| 3 | INFORMATION SECURITY | 23 | 40% | 4% | 45 |
| 4 | COMPUTER ABUSE | 20 | 67% | 2% | 18 |
| 5 | INFORMATION SYSTEMS SECURITY | 12 | 75% | 1% | 9 |
| 6 | INSIDER THREAT | 8 | 100% | 0% | 5 |
| 7 | SPYWARE | 6 | 71% | 0% | 5 |
| 8 | SOFTWARE VULNERABILITIES | 6 | 100% | 0% | 4 |
| 9 | PASSPOINTS | 5 | 63% | 0% | 5 |
| 10 | INTERNET SECURITY | 4 | 75% | 0% | 3 |
Journals |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | COMPUTERS & SECURITY | 46 | 20% | 19% | 206 |
Reviews |
| Title | Publ. year | Cit. | Active references |
% act. ref. to same field |
|---|---|---|---|---|
| Security-related behavior in using information systems in the workplace: A review and synthesis | 2013 | 6 | 24 | 83% |
| Proposing the control-reactance compliance model (CRCM) to explain opposing motivations to comply with organisational information security policies | 2015 | 1 | 99 | 29% |
| User Awareness of Security Countermeasures and Its Impact on Information Systems Misuse: A Deterrence Approach | 2009 | 89 | 55 | 27% |
| A review and analysis of deterrence theory in the IS security literature: making sense of the disparate findings | 2011 | 21 | 46 | 28% |
| Reinforcing the security of corporate information resources: A critical review of the role of the acceptable use policy | 2011 | 5 | 23 | 65% |
| The economics of information security | 2006 | 94 | 7 | 14% |
| Current directions in IS security research: towards socio-organizational perspectives | 2001 | 107 | 37 | 14% |
| A systematic review of approaches to assessing cybersecurity awareness | 2015 | 0 | 22 | 64% |
| Man-At-The-End attacks: Analysis, taxonomy, human aspects, motivation and future directions | 2015 | 0 | 44 | 57% |
| Wisecrackers: A theory-grounded investigation of phishing and pretext social engineering threats to information security | 2008 | 13 | 44 | 25% |
Address terms |
| Rank | Address term | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | IS SECUR | 13 | 80% | 0.8% | 8 |
| 2 | INFORMAT SECUR NETWORK GRP | 4 | 75% | 0.3% | 3 |
| 3 | STAND BANK INFORMAT TECHNOL | 4 | 75% | 0.3% | 3 |
| 4 | INFORMAT PROC SCI | 3 | 13% | 1.8% | 19 |
| 5 | TUCKS GLASSMEYER MCNAMEE DIGITAL STRATEGIES | 2 | 67% | 0.2% | 2 |
| 6 | SECUR COMMUN NETWORK | 1 | 38% | 0.3% | 3 |
| 7 | INFORMAT SECUR STUDIES | 1 | 50% | 0.2% | 2 |
| 8 | INTERNET FORENS | 1 | 100% | 0.2% | 2 |
| 9 | SYST COMP TECHNOL | 1 | 100% | 0.2% | 2 |
| 10 | INFORMAT TECHNOL OPERAT MANAGEMENT | 1 | 13% | 0.9% | 10 |
Related classes at same level (level 1) |
| Rank | Relatedness score | Related classes |
|---|---|---|
| 1 | 0.0000175110 | MTTSF//VULNERABILITY DISCOVERY MODEL//EMC APPROACH |
| 2 | 0.0000165247 | COMP IND ENGN//EIII//DIVERSIFIED MANAGEMENT |
| 3 | 0.0000127257 | CYBERLOAFING//CYBERSLACKING//NON WORK RELATED COMPUTING |
| 4 | 0.0000101002 | KEYSTROKE DYNAMICS//MOUSE DYNAMICS//KEYSTROKE ANALYSIS |
| 5 | 0.0000095897 | CRIT INFRASTRUCT PROTECT//AI SAFETY//BLP BELL LAPADULA SECURITY MODEL |
| 6 | 0.0000088523 | NETWORK READY DEVICES//COMMERCE PROCESSES//WIRELESS 1394 |
| 7 | 0.0000079926 | ANTI SPAM FILTERING//SPAM FILTERING//SPAM |
| 8 | 0.0000078294 | PRIVACY CALCULUS//INFORMATION PRIVACY//INFORMATION PRIVACY CONCERNS |
| 9 | 0.0000065797 | COUNTER FRAUD STUDIES//EDINBURGH DATA INTENS GRP//MASS MARKETING FRAUD |
| 10 | 0.0000059076 | COMPUTER VIRUS//MALWARE PROPAGATION//VIRAL EQUILIBRIUM |