Class information for: |
Basic class information |
| ID | Publications | Average number of references |
Avg. shr. active ref. in WoS |
|---|---|---|---|
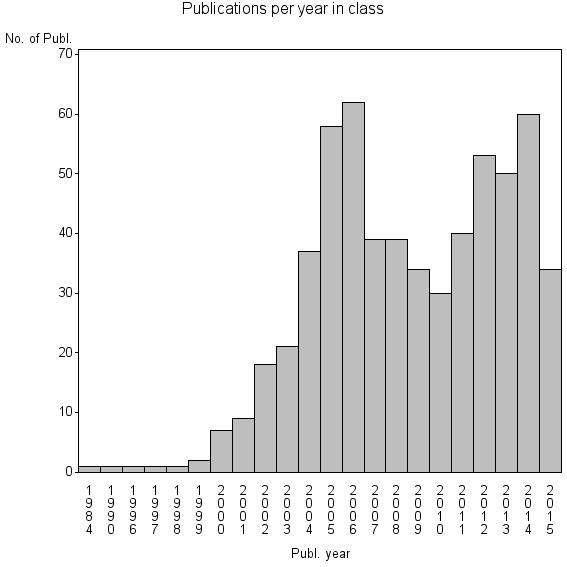
| 16256 | 598 | 26.1 | 23% |
Classes in level above (level 2) |
| ID, lev. above |
Publications | Label for level above |
|---|---|---|
| 1591 | 6600 | DIGITAL INVESTIGATION//COMPUTERS & SECURITY//INTRUSION DETECTION |
Terms with highest relevance score |
| Rank | Term | Type of term | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|---|
| 1 | IP TRACEBACK | Author keyword | 13 | 29% | 6% | 38 |
| 2 | DISTRIBUTED DENIAL OF SERVICE DDOS | Author keyword | 9 | 39% | 3% | 19 |
| 3 | DENIAL OF SERVICE | Author keyword | 9 | 15% | 9% | 51 |
| 4 | DDOS ATTACKS | Author keyword | 8 | 32% | 3% | 20 |
| 5 | DDOS | Author keyword | 8 | 16% | 7% | 44 |
| 6 | IP SPOOFING | Author keyword | 7 | 33% | 3% | 18 |
| 7 | COMP SCI IND | Address | 4 | 67% | 1% | 4 |
| 8 | DDOS DETECTION | Author keyword | 3 | 45% | 1% | 5 |
| 9 | PACKET LOGGING | Author keyword | 3 | 45% | 1% | 5 |
| 10 | TRACEBACK | Author keyword | 3 | 18% | 3% | 15 |
Web of Science journal categories |
Author Key Words |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | IP TRACEBACK | 13 | 29% | 6% | 38 | Search IP+TRACEBACK | Search IP+TRACEBACK |
| 2 | DISTRIBUTED DENIAL OF SERVICE DDOS | 9 | 39% | 3% | 19 | Search DISTRIBUTED+DENIAL+OF+SERVICE+DDOS | Search DISTRIBUTED+DENIAL+OF+SERVICE+DDOS |
| 3 | DENIAL OF SERVICE | 9 | 15% | 9% | 51 | Search DENIAL+OF+SERVICE | Search DENIAL+OF+SERVICE |
| 4 | DDOS ATTACKS | 8 | 32% | 3% | 20 | Search DDOS+ATTACKS | Search DDOS+ATTACKS |
| 5 | DDOS | 8 | 16% | 7% | 44 | Search DDOS | Search DDOS |
| 6 | IP SPOOFING | 7 | 33% | 3% | 18 | Search IP+SPOOFING | Search IP+SPOOFING |
| 7 | DDOS DETECTION | 3 | 45% | 1% | 5 | Search DDOS+DETECTION | Search DDOS+DETECTION |
| 8 | PACKET LOGGING | 3 | 45% | 1% | 5 | Search PACKET+LOGGING | Search PACKET+LOGGING |
| 9 | TRACEBACK | 3 | 18% | 3% | 15 | Search TRACEBACK | Search TRACEBACK |
| 10 | DDOS ATTACK | 3 | 20% | 2% | 13 | Search DDOS+ATTACK | Search DDOS+ATTACK |
Key Words Plus |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | DDOS ATTACKS | 35 | 67% | 5% | 32 |
| 2 | OF SERVICE ATTACKS | 15 | 49% | 4% | 22 |
| 3 | SERVICE ATTACKS | 12 | 42% | 4% | 23 |
| 4 | IP TRACEBACK | 11 | 30% | 5% | 31 |
| 5 | PACKET MARKING | 6 | 41% | 2% | 12 |
| 6 | TRACEBACK | 6 | 50% | 1% | 8 |
| 7 | DENIAL OF SERVICE | 4 | 47% | 1% | 7 |
| 8 | SCALE IP TRACEBACK | 4 | 75% | 1% | 3 |
| 9 | PROBABILISTIC PACKET MARKING | 3 | 57% | 1% | 4 |
| 10 | DDOS | 3 | 45% | 1% | 5 |
Journals |
Reviews |
| Title | Publ. year | Cit. | Active references |
% act. ref. to same field |
|---|---|---|---|---|
| Analyzing well-known countermeasures against distributed denial of service attacks | 2012 | 11 | 31 | 84% |
| DDoS Incidents and their Impact: A Review | 2010 | 3 | 6 | 83% |
Address terms |
| Rank | Address term | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | COMP SCI IND | 4 | 67% | 0.7% | 4 |
| 2 | ETS COMP TELECOMMUN ENGN | 2 | 67% | 0.3% | 2 |
| 3 | OPT INTERNET MOBILE INFORMAT NETWORK | 2 | 67% | 0.3% | 2 |
| 4 | CDBR SSE PROJECT | 1 | 100% | 0.3% | 2 |
| 5 | COMMPUTER SCI TECHNOL | 1 | 100% | 0.3% | 2 |
| 6 | NETWORK SCI CYBERSPACE | 1 | 19% | 0.7% | 4 |
| 7 | SPIIRAS | 1 | 33% | 0.3% | 2 |
| 8 | AKAMAI TECHNOL | 1 | 50% | 0.2% | 1 |
| 9 | COMMUN INFORMAT ENGINEER | 1 | 50% | 0.2% | 1 |
| 10 | CONVERGING INFRASTRUCT SECUR CISEC | 1 | 50% | 0.2% | 1 |
Related classes at same level (level 1) |
| Rank | Relatedness score | Related classes |
|---|---|---|
| 1 | 0.0000217085 | INTRUSION DETECTION//ALERT CORRELATION//INTRUSION DETECTION SYSTEM |
| 2 | 0.0000187267 | TRAFFIC CLASSIFICATION//HEAVY HITTERS//TRAFFIC PROFILING |
| 3 | 0.0000161337 | SESSION INITIATION PROTOCOL//SPAM OVER INTERNET TELEPHONY SPIT//ZRTP |
| 4 | 0.0000112648 | CAUSALITY GRAPH MODEL//EVENT CORRELATION//COGNIT ENGN PROGRAM |
| 5 | 0.0000100998 | COMPUTER VIRUS//MALWARE PROPAGATION//VIRAL EQUILIBRIUM |
| 6 | 0.0000099596 | BGP//BORDER GATEWAY PROTOCOL BGP//INTERDOMAIN ROUTING |
| 7 | 0.0000087037 | JAMMING DETECTION//REACTIVE JAMMING//RF FINGERPRINTS |
| 8 | 0.0000083101 | MTTSF//VULNERABILITY DISCOVERY MODEL//EMC APPROACH |
| 9 | 0.0000082437 | POTENTIAL MEMBRANE//DISCONTINUOUS SIMULATION//PHARMACEUT SCI DIFARMA |
| 10 | 0.0000072305 | NETWORK TOMOGRAPHY//END TO END MEASUREMENT//TRAFFIC MATRIX ESTIMATION |