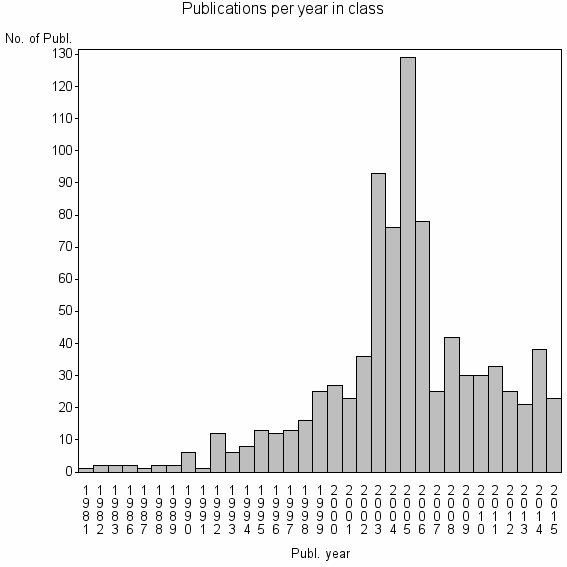
Class information for: |
Basic class information |
| ID | Publications | Average number of references |
Avg. shr. active ref. in WoS |
|---|---|---|---|
| 12286 | 853 | 25.1 | 29% |
Classes in level above (level 2) |
| ID, lev. above |
Publications | Label for level above |
|---|---|---|
| 216 | 20103 | FORMAL METHODS IN SYSTEM DESIGN//MODEL CHECKING//LECTURE NOTES IN COMPUTER SCIENCE |
Terms with highest relevance score |
| Rank | Term | Type of term | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|---|
| 1 | SECURITY PROTOCOLS | Author keyword | 21 | 28% | 7% | 62 |
| 2 | DOLEV YAO MODEL | Author keyword | 14 | 100% | 1% | 7 |
| 3 | CRYPTOGRAPHIC PROTOCOLS | Author keyword | 12 | 21% | 6% | 51 |
| 4 | DOLEV YAO INTRUDER | Author keyword | 6 | 80% | 0% | 4 |
| 5 | SECURITY PROTOCOL ANALYSIS | Author keyword | 6 | 53% | 1% | 8 |
| 6 | STRAND SPACES | Author keyword | 5 | 60% | 1% | 6 |
| 7 | APPLIED PI CALCULUS | Author keyword | 5 | 50% | 1% | 7 |
| 8 | LSV | Address | 4 | 13% | 4% | 31 |
| 9 | SPI CALCULUS | Author keyword | 4 | 47% | 1% | 7 |
| 10 | REACTIVE SIMULATABILITY | Author keyword | 4 | 67% | 0% | 4 |
Web of Science journal categories |
Author Key Words |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
LCSH search | Wikipedia search |
|---|---|---|---|---|---|---|---|
| 1 | SECURITY PROTOCOLS | 21 | 28% | 7% | 62 | Search SECURITY+PROTOCOLS | Search SECURITY+PROTOCOLS |
| 2 | DOLEV YAO MODEL | 14 | 100% | 1% | 7 | Search DOLEV+YAO+MODEL | Search DOLEV+YAO+MODEL |
| 3 | CRYPTOGRAPHIC PROTOCOLS | 12 | 21% | 6% | 51 | Search CRYPTOGRAPHIC+PROTOCOLS | Search CRYPTOGRAPHIC+PROTOCOLS |
| 4 | DOLEV YAO INTRUDER | 6 | 80% | 0% | 4 | Search DOLEV+YAO+INTRUDER | Search DOLEV+YAO+INTRUDER |
| 5 | SECURITY PROTOCOL ANALYSIS | 6 | 53% | 1% | 8 | Search SECURITY+PROTOCOL+ANALYSIS | Search SECURITY+PROTOCOL+ANALYSIS |
| 6 | STRAND SPACES | 5 | 60% | 1% | 6 | Search STRAND+SPACES | Search STRAND+SPACES |
| 7 | APPLIED PI CALCULUS | 5 | 50% | 1% | 7 | Search APPLIED+PI+CALCULUS | Search APPLIED+PI+CALCULUS |
| 8 | SPI CALCULUS | 4 | 47% | 1% | 7 | Search SPI+CALCULUS | Search SPI+CALCULUS |
| 9 | REACTIVE SIMULATABILITY | 4 | 67% | 0% | 4 | Search REACTIVE+SIMULATABILITY | Search REACTIVE+SIMULATABILITY |
| 10 | CARDHOLDER AUTHENTICATION | 4 | 75% | 0% | 3 | Search CARDHOLDER+AUTHENTICATION | Search CARDHOLDER+AUTHENTICATION |
Key Words Plus |
| Rank | Web of Science journal category | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | CRYPTOGRAPHIC PROTOCOLS | 50 | 46% | 9% | 81 |
| 2 | SECURITY PROTOCOLS | 35 | 41% | 8% | 67 |
| 3 | PUBLIC KEY PROTOCOLS | 12 | 86% | 1% | 6 |
| 4 | FORMAL ENCRYPTION | 10 | 40% | 2% | 19 |
| 5 | SPI CALCULUS | 9 | 43% | 2% | 16 |
| 6 | ACTIVE ADVERSARIES | 9 | 44% | 2% | 15 |
| 7 | SECURITY PROPERTIES | 6 | 71% | 1% | 5 |
| 8 | RECURSIVE AUTHENTICATION PROTOCOL | 4 | 67% | 0% | 4 |
| 9 | STRAND SPACES | 4 | 75% | 0% | 3 |
| 10 | SYMBOLIC PROTOCOL ANALYSIS | 4 | 75% | 0% | 3 |
Journals |
Reviews |
| Title | Publ. year | Cit. | Active references |
% act. ref. to same field |
|---|---|---|---|---|
| Security protocols over open networks and distributed systems: formal methods for their analysis, design, and verification | 1999 | 12 | 12 | 75% |
Address terms |
| Rank | Address term | Relevance score (tfidf) |
Class's shr. of term's tot. occurrences |
Shr. of publ. in class containing term |
Num. of publ. in class |
|---|---|---|---|---|---|
| 1 | LSV | 4 | 13% | 3.6% | 31 |
| 2 | FUTURS PROJET SECSI | 4 | 75% | 0.4% | 3 |
| 3 | SECSI | 3 | 60% | 0.4% | 3 |
| 4 | UGBS | 3 | 60% | 0.4% | 3 |
| 5 | UMR 8643 | 3 | 16% | 1.8% | 15 |
| 6 | FUTURS PROJET | 2 | 67% | 0.2% | 2 |
| 7 | IST PLICAZ TELEMAT | 2 | 67% | 0.2% | 2 |
| 8 | LORIA INRIA | 2 | 67% | 0.2% | 2 |
| 9 | IST INFORMAT TELEMAT | 2 | 14% | 1.6% | 14 |
| 10 | LOG COMPUTAT | 2 | 50% | 0.4% | 3 |
Related classes at same level (level 1) |
| Rank | Relatedness score | Related classes |
|---|---|---|
| 1 | 0.0000141759 | PROCESS CALCULI//PI CALCULUS//THE PI CALCULUS |
| 2 | 0.0000138623 | PASSWORD//SMART CARD//PASSWORD AUTHENTICATION |
| 3 | 0.0000106188 | BYTECODE VERIFICATION//PREVENT INFORMATION LEAKAGE//SEPARATION LOGIC |
| 4 | 0.0000084243 | INFORMAT IFI//BEYOND WEB//MAQS |
| 5 | 0.0000080301 | TRUSTED PERSONAL DEVICE//HIMALIS//LIBERTY ALLIANCE |
| 6 | 0.0000080035 | TRUST NEGOTIATION//DISTRIBUTED PROVING//JAVA BASED MOBILE PHONE APPLICATION |
| 7 | 0.0000077851 | MOBILE INNOVAT//ULTRA FLAT ARCHITECTURE//ROHC |
| 8 | 0.0000077551 | RANDOM ORACLE MODEL//PROXY SIGNATURE//DIGITAL SIGNATURE |
| 9 | 0.0000068673 | TERM REWRITING//LUFG INFORMAT 2//TERM REWRITING SYSTEMS |
| 10 | 0.0000068280 | INTERNATIONAL JOURNAL OF CRITICAL INFRASTRUCTURE PROTECTION//SUPERVISORY CONTROL AND DATA ACQUISITION SCADA SYSTEMS//TRUST CASE |